What is account takeover?
Back to glossaryAccount takeover (ATO) is a form of fraud in which cybercriminals gain unauthorized access to online personal or business accounts using stolen credentials.
Once a malicious attacker gains access to the targeted account, it can transfer funds, use stored credit card information, deplete gift card balances and loyalty points, redeem airline miles, submit fraudulent credit applications, plant ransomware or other malware, steal corporate data, and perform acts of cyberterrorism.
The basis of an ATO attack is relatively simple, but it can be difficult to detect. Let’s break down the basic steps in taking over an unsuspecting user’s online account:
- Malicious actors lay the foundation of an ATO attack by gaining access to a large volume of user credentials. Some attackers start with an email or text-based phishing campaign or by hacking a network to collect usernames, passwords, and other personal data. Other attackers simply buy a list of credentials on the dark web.
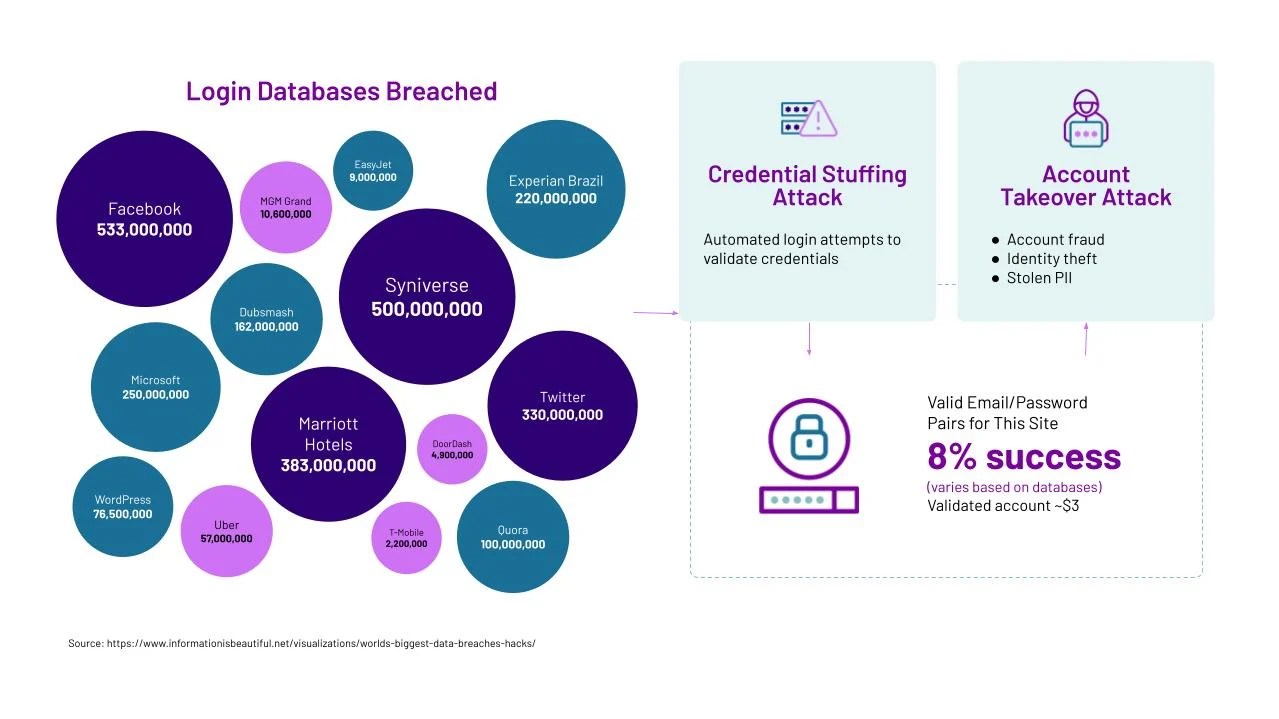
- Once an attacker has a list of user login credentials, it can test these credentials against target sites. Most often, an attacker will try various validation techniques using an army of automated bots. Automated bots make it easy for an attacker to execute brute force and credential stuffing attacks by quickly rolling through countless username and password combinations to identify valid combinations. With this automated approach, attackers can successfully crack as many as 8% of targeted accounts.
- Once an attacker has amassed a list of validated credentials, it can profit by initiating malicious actions such as withdrawing users’ funds, opening lines of credit, making purchases, or reselling the validated credentials to others for exploitation.
- Most people reuse login credentials among many sites. So, once a malicious attacker identifies a valid username and password combination, it will likely try to scale its efforts with the same credential combination on other popular retail, travel, social media, bank, and e-commerce sites. This helps a cybercriminal increase the profitability of each validated credential.
Cybercriminals often employ various techniques to gain access to the account of an unsuspecting user. If an attacker has a list of usernames for a targeted site, but not the passwords, it may employ the technique password spraying in which an attacker tries a common default password, such as “Password1,” against a large number of usernames. The attacker uses the brute force of bot automation to systematically try the guessed password against as many usernames as possible until the attacker identifies one that works.
If an attacker has a valid username and password combination for a targeted site, they may try to scale the attack to take over the user’s accounts on additional sites. This technique is called credential stuffing. Again, an attacker will employ the brute force of bot automation to quickly try the credentials across e-commerce, banking, travel and other popular websites in the hopes that some users have reused the same usernames and passwords for multiple sites.
For cybercriminals, an account takeover is easy to accomplish and profitable. Bots continuously evolve to evade detection mechanisms, so account takeover attacks get through and website owners are none the wiser. Bots can mimic user behavior and hide inside a validated user session by running as malware on actual user devices.
As with many cyberattacks, financial services companies were the original targets for ATO as criminals attempted to access the funds in a user’s account or open lines of credit in a user’s name.
Today, any organization that maintains user accounts that can be exploited for profit is a potential target. This can include taking over e-commerce or travel accounts to make fraudulent purchases or cash in loyalty points. It can also include targeting business accounts such as email or network logins to gain a foothold for a larger data theft or ransomware attack.
Account takeover attacks can have severe consequences. These include:
- Stolen stored value/account balances (e.g., monetary balances, loyalty points, digital credits, airline miles, gift card balances)
- Illicit credit card use
- Fraudulent credit applications
- Distributing malware and phishing emails
- Theft of users’ stored PII
- Return fraud
- Stealing restricted content (e.g. product details, content behind paywall)
This can result in financial losses, damage to brand reputation and consumer trust, resource costs for remediation and recovery, as well as lawsuits and fines.
Even if attacks take over a small percentage of user accounts, the damage can be substantial when user account values are high. Theft of stored credit card numbers or loyalty points, for example, could easily net millions of dollars for a cybercriminal. And theft also negatively affects end users.
The speed and evolution of today’s attacks present significant challenges for businesses. Unfortunately, some of the most commonly used techniques aren’t enough to stop ATO.
- Web application firewalls: While web application firewalls (WAFs) help secure web servers, they are not as effective in detecting ATO attacks or triggering alerts. WAFs are largely bypassed and ignored by the latest, sophisticated bot attacks, but their prevalence has contributed to a false sense of security among website owners. Neither WAFs nor regular website logging have the sensitivity to see patterns in the traffic and detect modern ATO attacks, so they go largely undetected.
- Homegrown bot management: Homegrown solutions use signatures and pre-configured rules and policies, such as volumetric-based and geo-based detection to stop bots. But, the efficacy of signature-based detection has declined rapidly over time. If you block traffic because of an unknown spike, you might also block real users. Signature-based systems also have difficulty dealing with hyper-distributed bot attacks.
- CAPTCHAs: Over time, the original CAPTCHAs have become easy to solve for bots equipped with image processing software. Some bots have a 90% success rate for solving CAPTCHAs. To counter the growing capabilities of bots, CAPTCHA services have gradually increased the difficulty of the challenges, ultimately escalating to visual processing challenges that are actually hard for humans to solve. At the same time, more challenging CAPTCHAs also violate a core user experience principle, which is to make the user’s experience smoother, faster and better, not more disjointed, slower, and worse.
HUMAN Account Takeover Defense combats account takeover attacks at every step of the user journey. The solution take a layered approach:
- Blocks logins with stolen credentials that are actively being used in real-world attacks, reducing your vulnerable attack surface
- Stops bot attacks at login, blocking automated credential stuffing and brute-forcing attacks in real time
- Detects suspicious behavior post-login and remediates breached accounts, no matter how the account was compromised
Account Takeover Defense stops ATO attacks with unparalleled accuracy. By combining proactive, real-time, and reactive detection methods, the solution protects digital organizations and their users from this growing threat.
Learn more about HUMAN Account Takeover Defense.
- What is credential stuffing? | Definition, attack types, & solutions
- What does CAPTCHA mean? | How CAPTCHAs work
- What is a brute force attack? | Definitions, types, & prevention
- What is fake account creation? | How to prevent it
- How to neutralize compromised and fake accounts
- What is bot mitigation? | 4 types of bots & botnets | How to stop bots