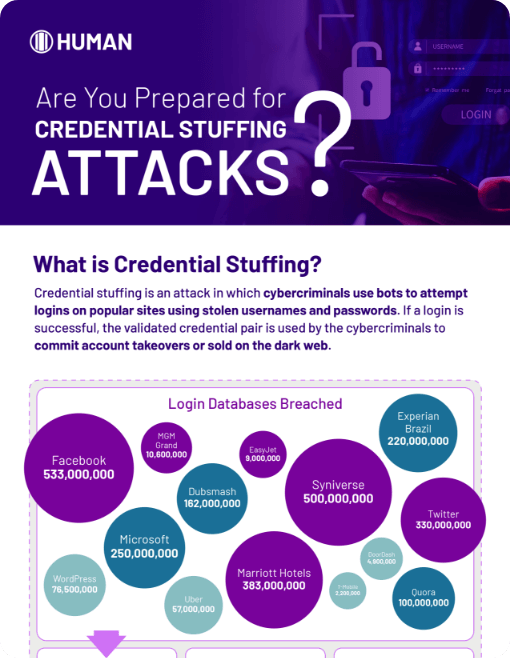
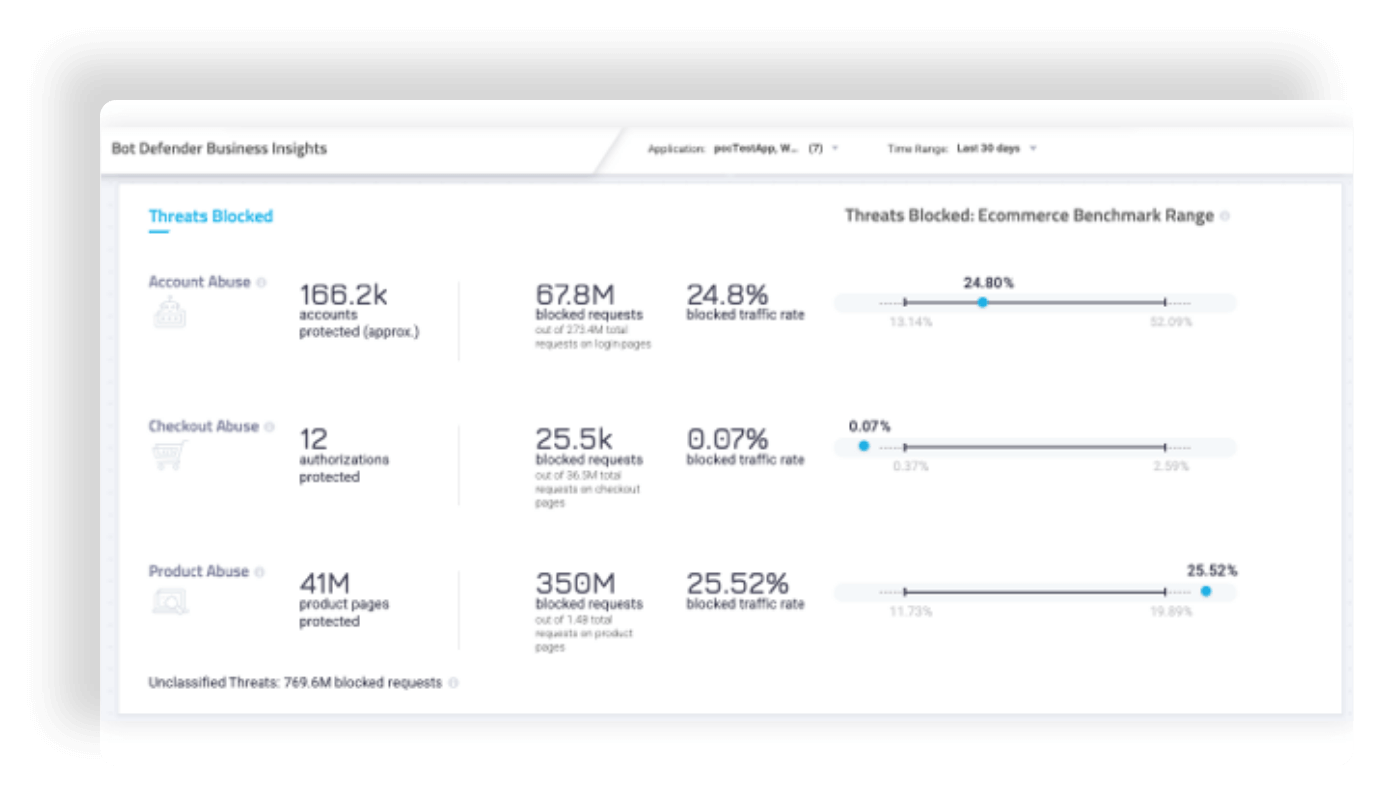
Credential Intelligence
Early Warning Indicator to Prevent Account Takeover
HUMAN Credential Intelligence stops the user of compromised credentials in real-time.
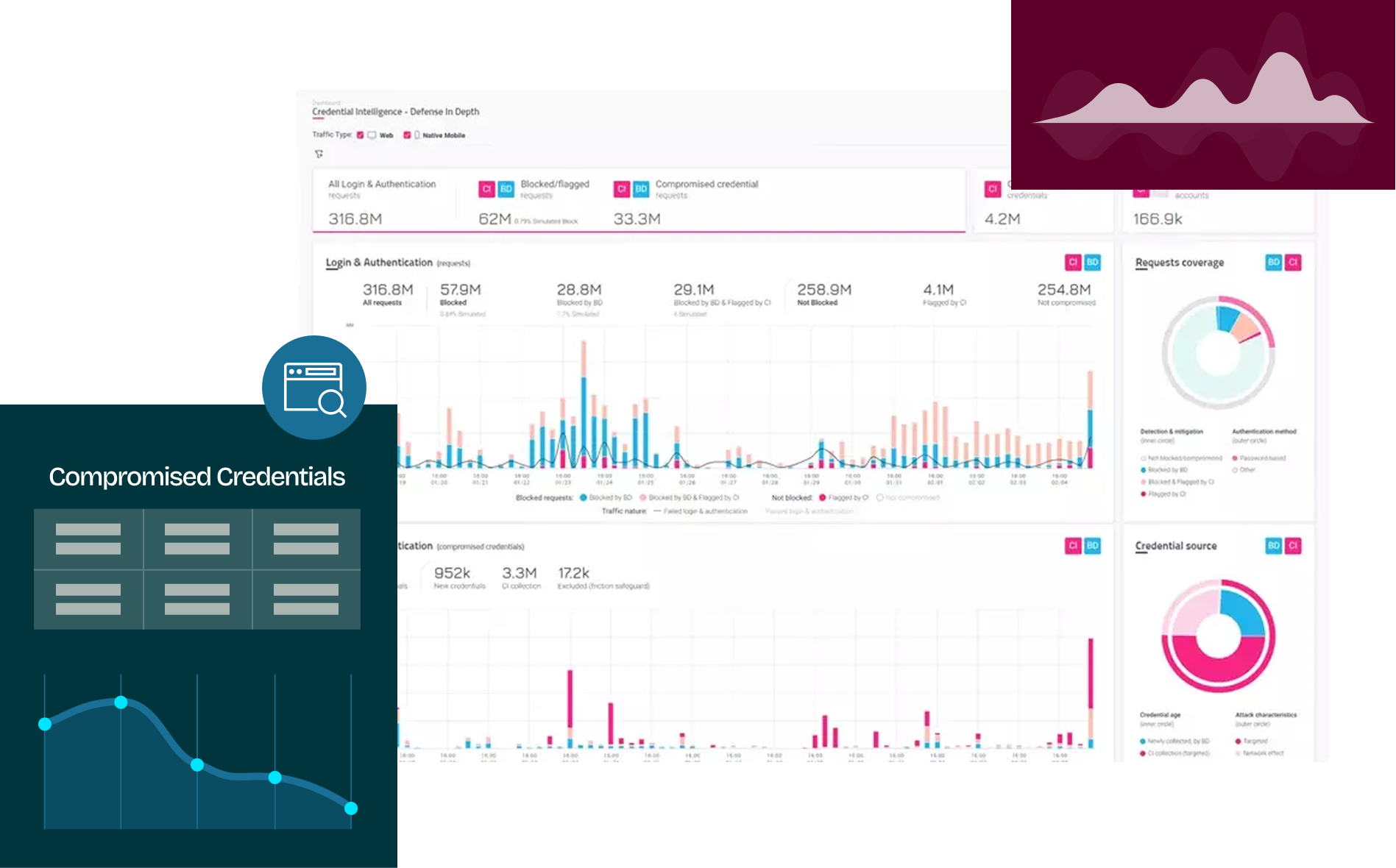
HUMAN Credential Intelligence detects and stops the use of compromised credentials in real-time.
An expansive, dynamic, and up-to-date collection is leveraged by HUMAN, gathered from its position protecting some of the most popular and highly-trafficked sites on the web.
Acting upon the breached signal can stop a threat actor from accessing the account and can warn real users that their credentials have been breached. Changing an account password will remove the vulnerable account, reduce the attack surface, and lower the overall risk of account takeover.
How you win with Credential Intelligence
HUMAN protects against compromised credential usage and provides detection with unmatched scale, speed, and precision to safeguard user accounts.
Stop account takeovers before they happen. Credential stuffing is a common technique used to commit account takeover attacks. Credential Intelligence gets ahead of account takeovers by flagging logins with compromised credentials and prompting a password reset. This restores the security of your users’ credentials, proactively protecting against account takeover attacks.
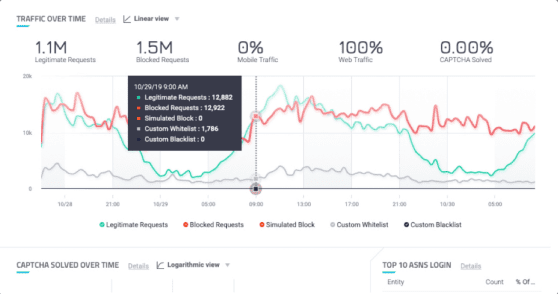
Raise the cost for attackers and reduce the cost of collective protection. Because people often reuse passwords, cybercriminals keep using the same lists in multiple credential stuffing attacks. Credential Intelligence disrupts their ROI by turning a previously renewable resource—compromised credentials—into a single-use resource. And we do it across the entire HUMAN network.
Stop playing an endless game of whac-a-mole. Instead of just blocking attacks as they come, Credential Intelligence stops the attacks at their core. The solution intercepts compromised credentials and renders them useless before bots attempt to take over the account. This shrinks your vulnerable surface area, reducing your risk of future attacks.
Trusted by the largest enterprises and internet platforms














How Credential Intelligence works
Fast deployment as a JS snippet or SDK

Collect

Detect

Protect