Easily Enable Browser Script Value
HUMAN puts invisible guardrails around client-side scripts—enabling value for CMOs and peace of mind for CISOs.


Get Complete Visibility
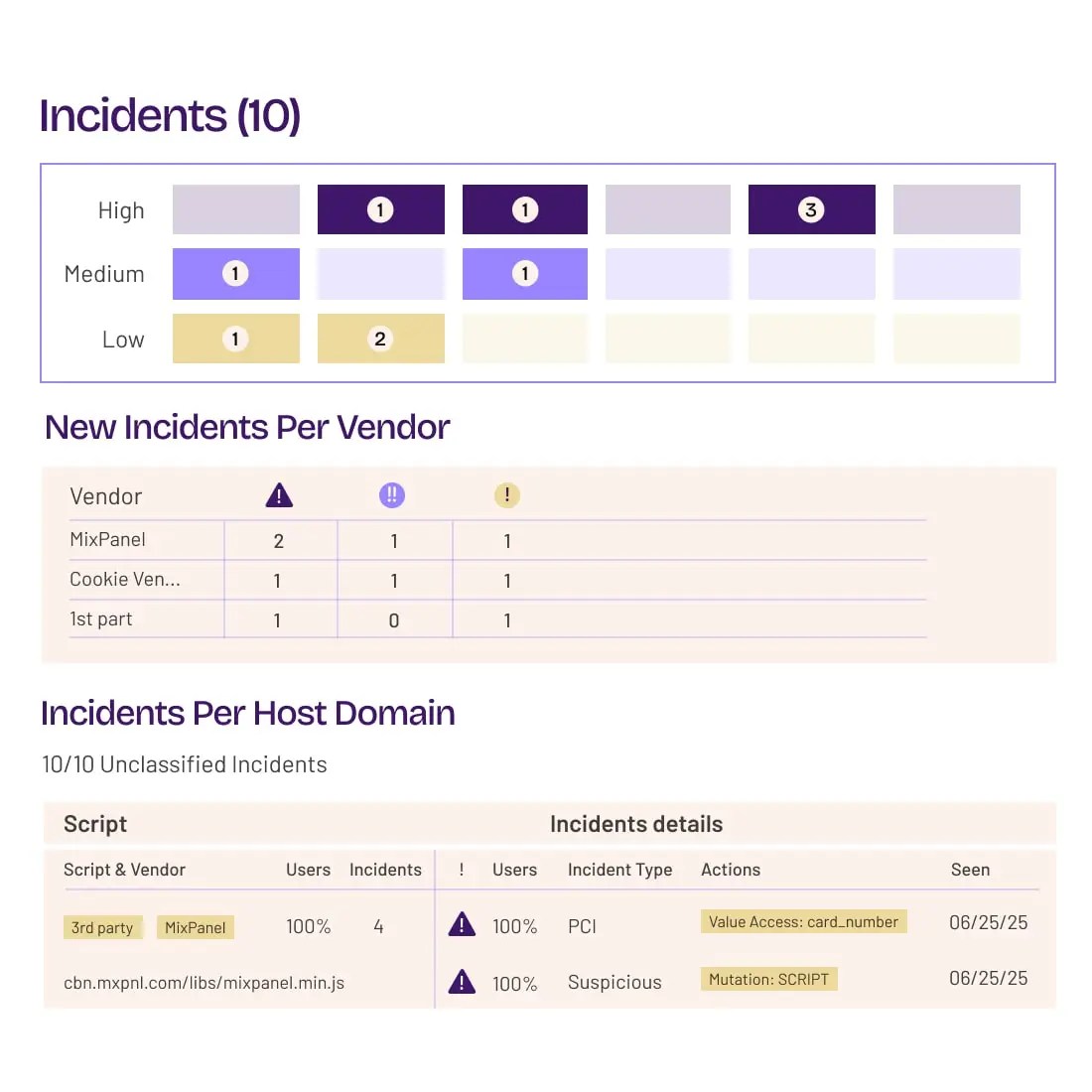
See all client-side 1st- and Nth-party script behavior in the browser during real visitor sessions.
Protect Your Business
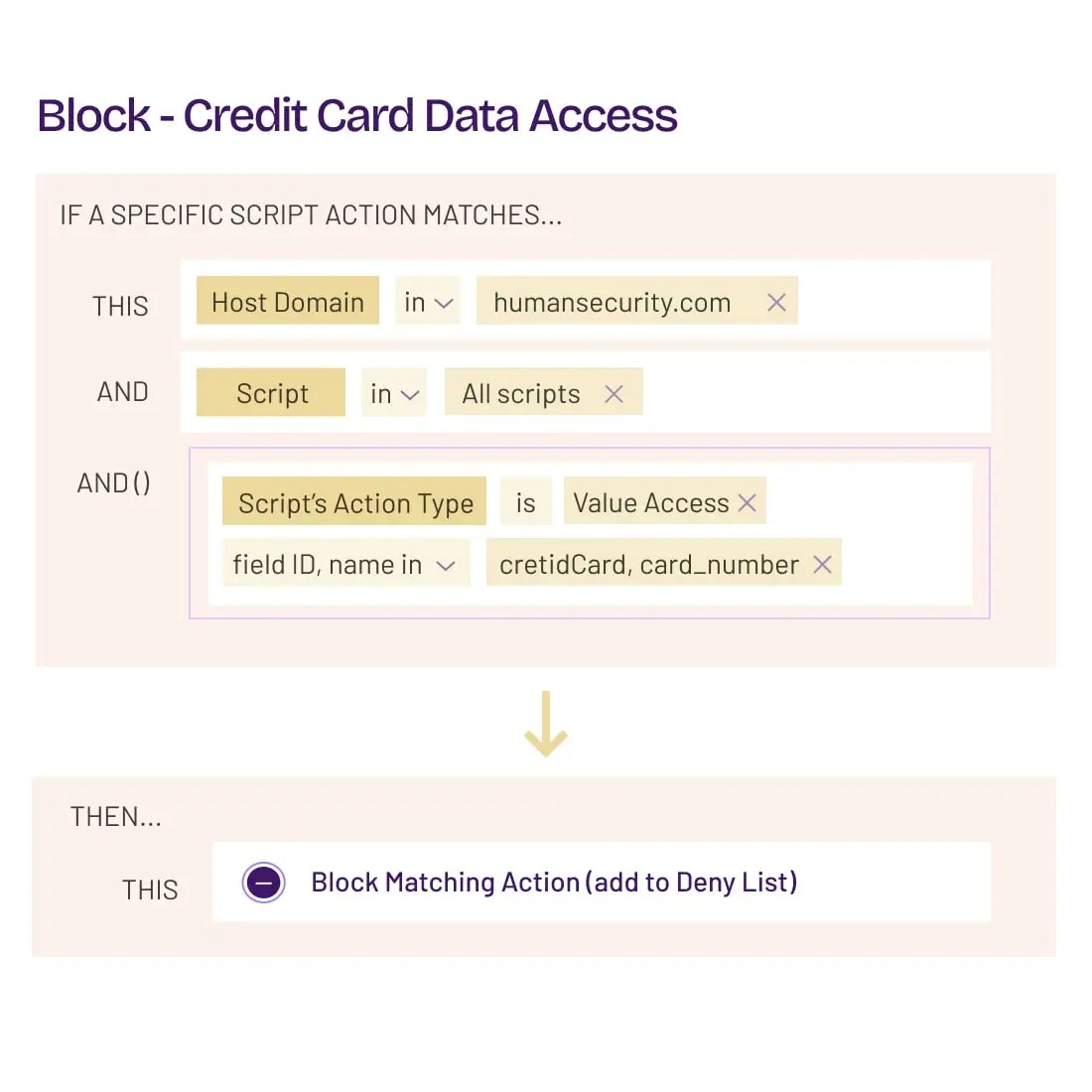
Automate zero-trust policies to surgically block risky script actions such as reading payment data and credentials.
Simplify and Maintain Compliance
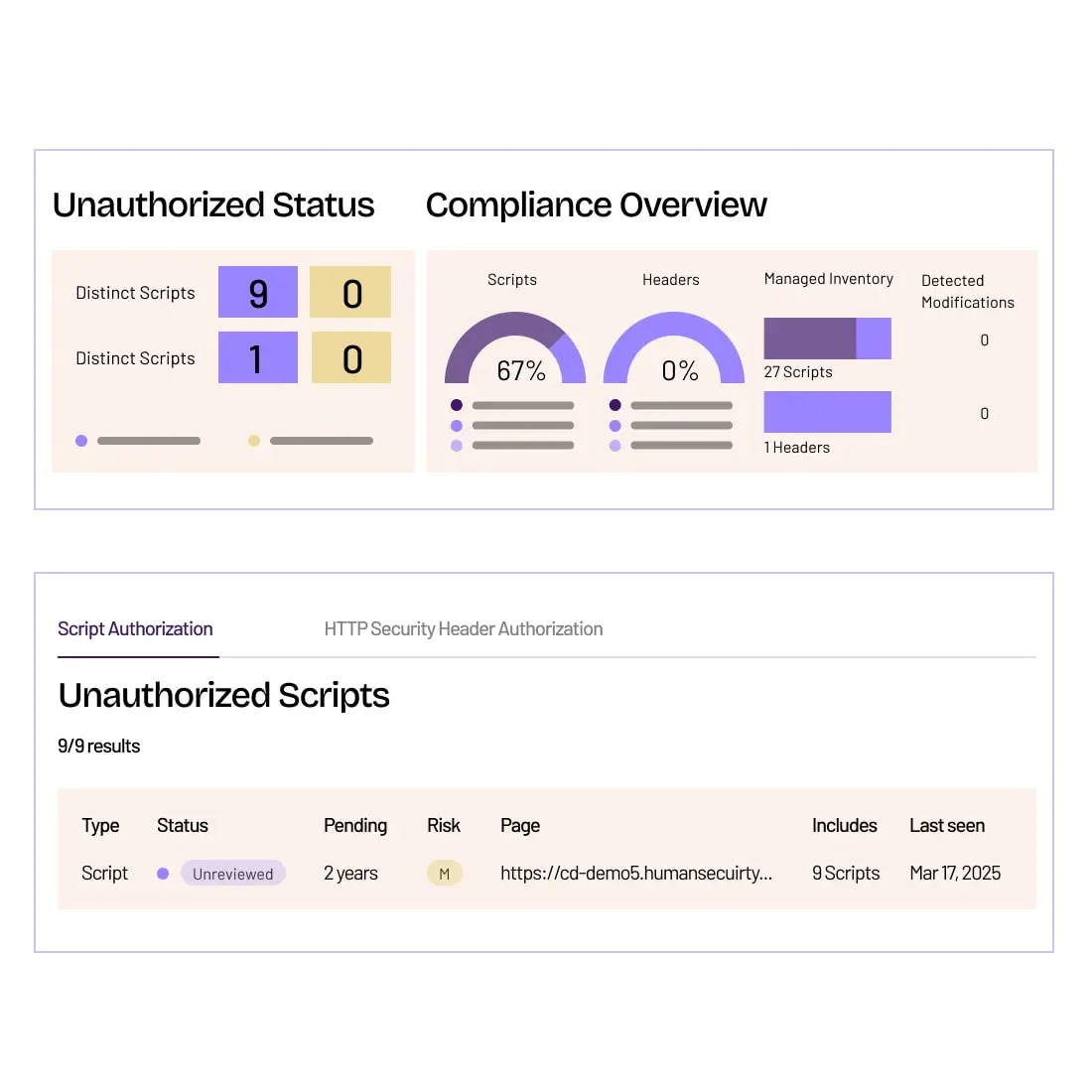
Stay compliant with standards and regulations, including PCI DSS 4, NIST CSF, GDPR, and HIPAA.
Enable Browser Script Value
Stop client-side supply chain attacks like digital skimming, Magecart, formjacking, and malicious redirects, while simplifying compliance with PCI DSS reqs 6.4.3 and 11.6.1.
Secure Your Client-Side Scripts
Get full visibility and control of browser scripts to reduce the risk of client-side attacks. Enable your business to make use of client-side browser scripts while reducing the risk of privacy, security, and compliance violations.
- Script Visibility
- Behavioral Analysis
- Mitigation and Control
- PCI DSS Compliance
- Script Visibility
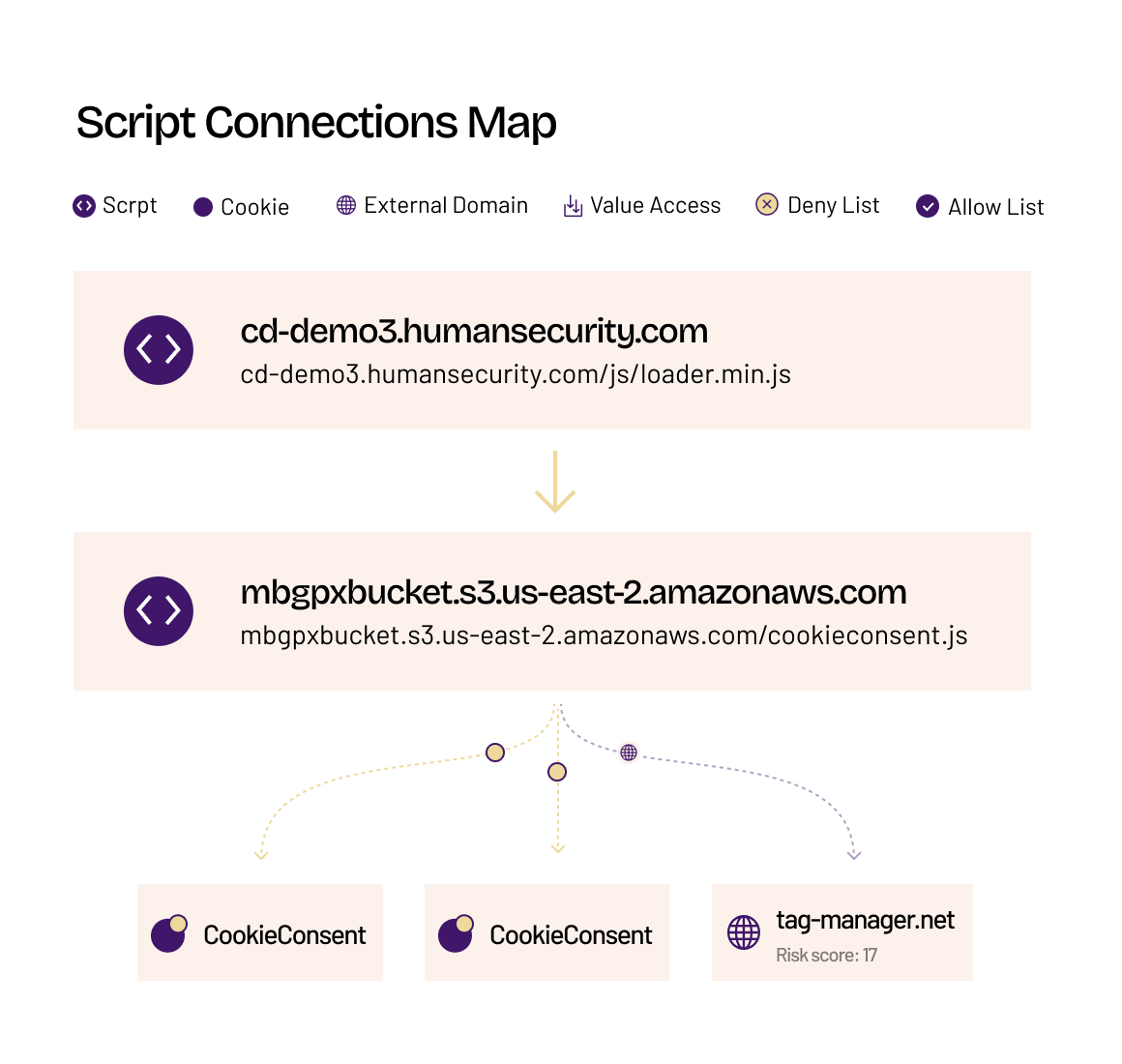
Script Visibility
Script Inventory
Collect script activity signals via a JavaScript sensor running in your users’ browsers to auto-inventory sensitive fields, scripts and script actions, domains, cookies, and more.
Script Analyzer
Analyze 1st- and Nth-party scripts for provenance, vulnerabilities, cookies, and behaviors—like DOM access, storage reads, sensitive data handling, and risky-domain communications.
- Behavioral Analysis
- Mitigation and Control
- PCI DSS Compliance
Security that Optimizes Your Business Goals


HUMAN is a fantastic solution for managing business critical scripts, and addressing the new PCI DSS 4 requirements (6.4.3 & 11.6.1) with ease. It not only adds another layer of defense to our overall security posture, but helps my team prioritize and reduces the need for time-intensive manual investigations and record-keeping activities.
Senior Security Developer, Information Security Team, Priceline
$20M
Fine on one company for failing to prevent a skimming attack
97%
Reduction in fraud costs after deploying HUMAN
The solution pays for itself by reducing our risk from client-side data breaches and helping us avoid fines and the subsequent negative impact to our brand reputation.
CISO, Top 5 Global Airline
2x
Jump in carding attacks

Threat Intelligence:
The HUMAN Element
The Satori Threat Intelligence and Research Team uncovers, analyzes, and disrupts cyberthreats and fraud schemes that undermine trust across the digital landscape, delivering cutting-edge research that strengthens protection for customers and thwarts bad actors for a safer internet.
Explore Satori
See HUMAN Client-Side Defense in Action