Key Capabilities
Block bots at the account perimeter and remediate risky user behavior within accounts.

Protection Across Full User Sessions
Catch fraud at every stage by blocking credential stuffing and brute forcing at login, providing deep credential intelligence, and continuously evaluating activities within accounts.
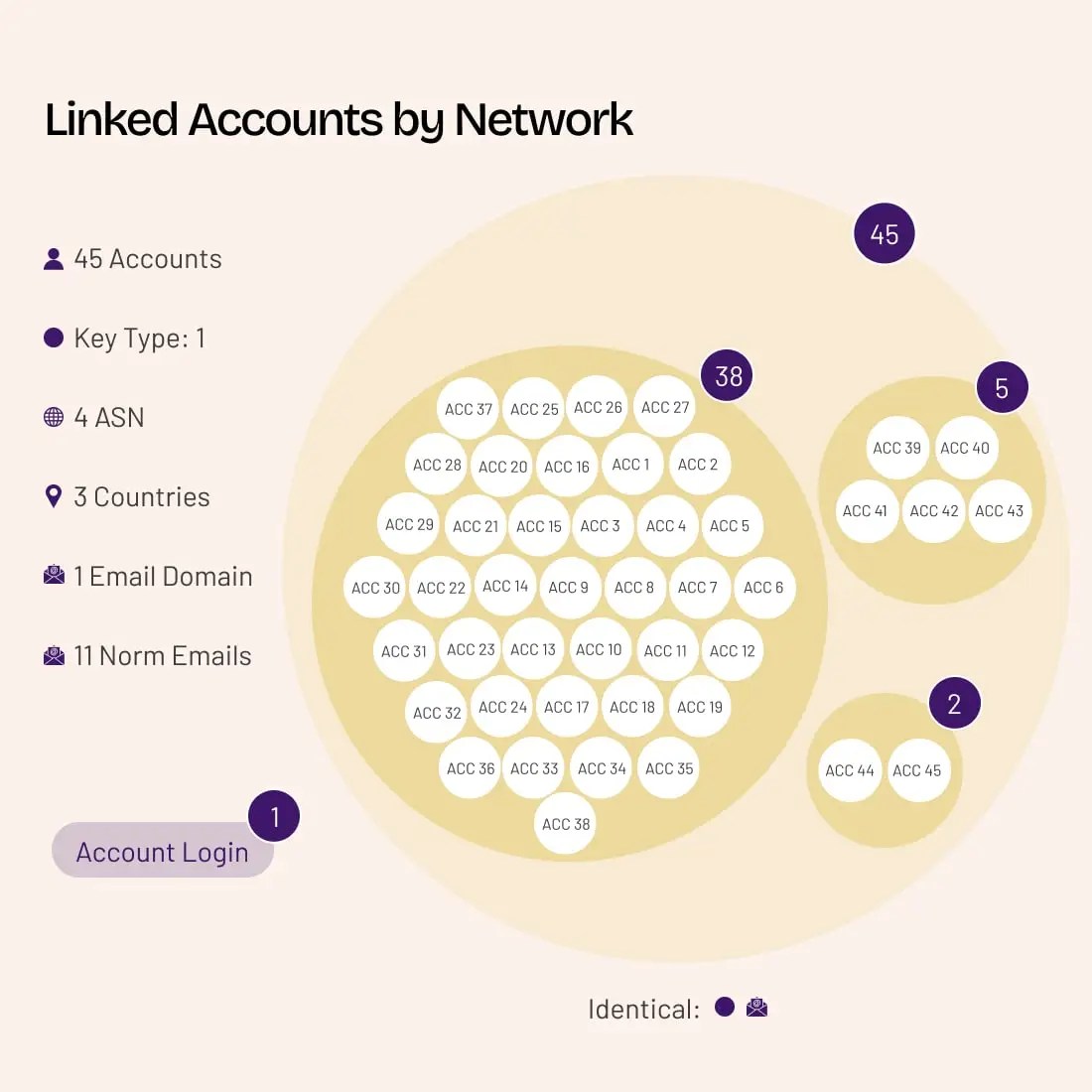
Understand Patterns of Fraud
Identify compromised accounts being used to commit fraud and abuse. Flag, group, and automatically respond to accounts with common identifiers (e.g. email).
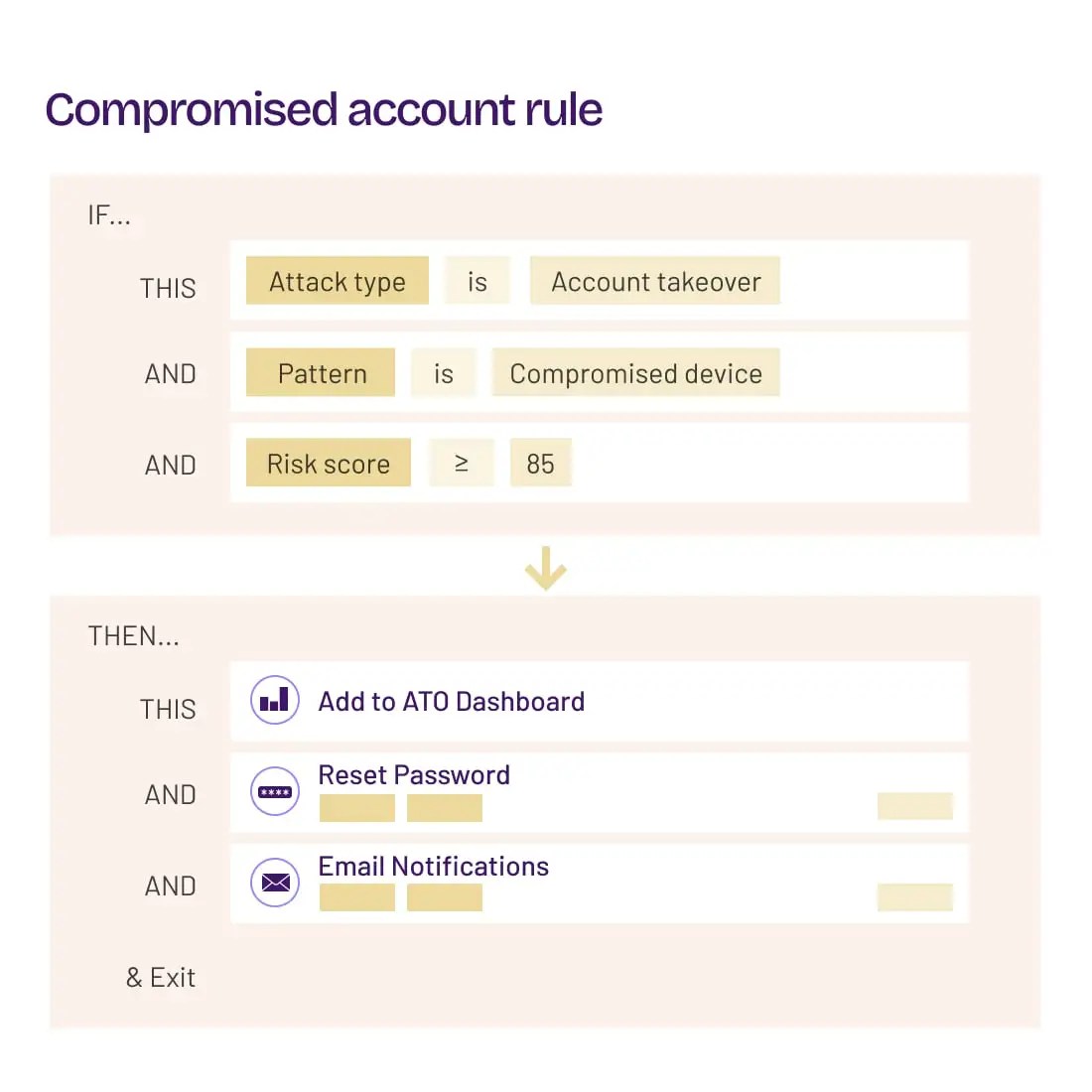
Build Custom Rules and Responses
Create multi-criteria rules and responses that automatically trigger when conditions are met. Actions can be custom built via API to interface with internal systems.
Protecting Customers from Evolving Risks
HUMAN is trusted by global organizations across industries to protect against account takeover attacks and compromised account fraud.
Threat Intelligence:
The HUMAN Element
The Satori Threat Intelligence and Research Team uncovers, analyzes, and disrupts cyberthreats and fraud schemes that undermine trust across the digital landscape, delivering cutting-edge research that strengthens protection for customers and thwarts bad actors for a safer internet.
Explore Satori
Secure Your Accounts with HUMAN
Protect user accounts from automated and human-led fraud and abuse with HUMAN Sightline.
Learn More
FAQ
What are compromised accounts?
Compromised accounts refer to user accounts that have been accessed by unauthorized individuals, often through stolen credentials, phishing, or malware. Once inside, attackers can steal personal information, make fraudulent transactions, or use the account as a stepping stone for broader attacks. Account takeover incidents not only harm individual users but can also damage a business’s reputation and result in financial loss. Protecting against compromised accounts is essential for maintaining trust and security in any online environment.
What types of fraud and abuse are consequences of compromised accounts?
Common examples include, theft of funds or sensitive personally identifiable information, fraudulent credit applications and sending of phishing emails.
Request a Demo