Why Security Leaders Need Advertisers
Read time: 5 minutesPeter Craig

Last year, as part of our appearance at the (virtual) Cannes Lions International Festival of Creativity conference, we held a session called “Why Advertisers Need Hackers”. It was a look at the role that cybersecurity can—and does—play in the advertising technology ecosystem. Hell, we’ve been saying for years that ad fraud isn’t a measurement problem, it’s a cybersecurity problem, and our Satori Threat Intelligence and Research Team is a key player in demonstrating that. Shutting down operations like Terracotta, PARETO, and 3ve don’t happen without the likes of the folks on that team, and those clearly benefited the advertising ecosystem directly.
But the coin has two sides. While the advertising ecosystem needs the expertise of hackers like our Satori team, cybersecurity leaders can also benefit directly from advertising. I know, that sounds borderline sacrilegious, but it’s true. Here’s why.
This is where the cybercriminals eat.
Tamer Hassan, our co-founder and CEO, mentioned this in a recent post about collective protection, but ad fraud is, perhaps paradoxically, the highest reward/lowest risk avenue of cybersecurity:
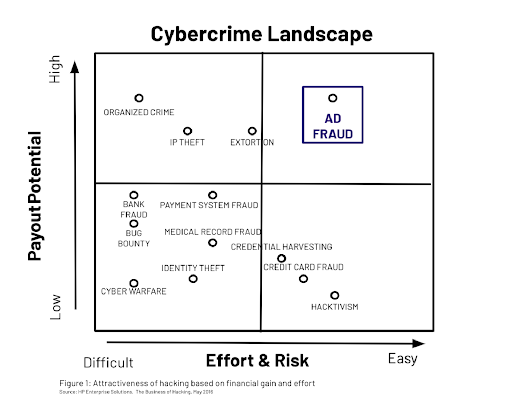
The short version is, ad fraud isn’t the sexiest kind of cybercrime out there. Look at some of the other items on that chart:
- Organized crime (I mean, have you seen The Sopranos?)
- Identity theft
- Hacktivism
- Medical record fraud
You could imagine most of the criminal avenues here appearing on the front page of the newspaper. But ad fraud? Harder to visualize. After all, and I write this knowing full well who “sits” beside me on our Zoom meetings, what average user out there is going to be especially upset if a brand loses a little money because somebody figured out a way to click on their banner ads a whole bunch of times?
The subreddit r/beermoney used to be filled with folks who had mobile device farms that clicked on ads to create just enough cash for the weekend to buy a case of beer to split with friends. The startup costs were low and the payouts were enough to be meaningful.
Over time, though, as the industry wised up, so too did the cybercriminals. It got harder for the beer money folks, and the domain of ad fraud was left to the professionals. These are the folks with two-week sprint cycles and full-time developers, deep knowledge of the industry and its inner workings, and expertise in programming languages (and in some cases, obscure foreign alphabets).
Okay, but what does this have to do with cybersecurity?
In a word, volume.
Here’s the front page of the website for the Chicago Tribune as of the time of writing:
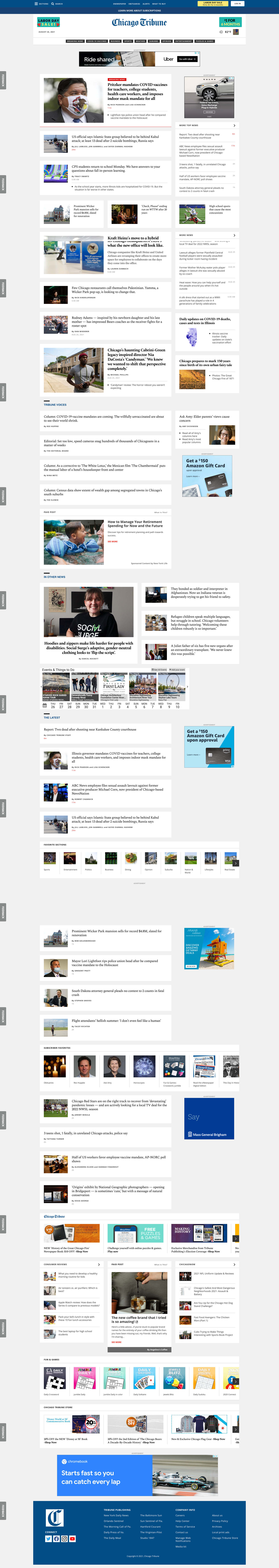
That’s nine individual ads that loaded at the time of the pageview (plus another modal pop-up ad that appears when you move your mouse to navigate away from the page). In the time between when I hit “enter” on my keyboard to visit the page and when the page loaded, every one of those ads went through a live auction for my eyeballs. My eyeballs are worth a certain amount of money to every company doing digital advertising, and that number changes based on a wide variety of factors, including where on the page the ad is, how much they know about me (based on cookies I have on my computer), and what organizations in the advertising ecosystem are working with The Tribune for placements.
That whole process, that real-time auction, that’s called “programmatic advertising”. We talk about it a lot here at HUMAN, but I wanted to give that really short primer because of this one number:
HUMAN verifies the humanity of 85% of programmatic advertising. That’s how we get to ten trillion interactions verified each week (and that number is still growing).
And that’s important to cybersecurity leaders because the things we look for to figure out if an interaction is bot or not aren’t necessarily advertising-specific. Automation is automation – if one node in a botnet is capable of clicking on a fake ad, it might also be capable of filling out a webform, or creating a new account on a website, or hoarding inventory. They’re roughly the same signals of bot activity, regardless of the venue.
Ten trillion times a week, we make a call: is this activity bot or not? Ten trillion times a week, we look through our 2500+ signals of automation and apply those to web traffic and say, “yeah, this is a real person” or “no, this looks like a bot”.
But why does scale matter so much?
The more you see, the better you can protect. In ten years of hunting for bots, we’ve encountered several instances of cybercriminals thinking they’ve found a way to counteract or sidestep our detection – PARETO was one good example, but so too were 3ve and Tushu, an operation we uncovered (twice) in 2019. Add to that volume our philosophy of collective protection and our Satori team’s ability to go on offense and proactively find new threats before they emerge, and you’ve got a compelling solution for finding and mitigating bots better than anybody else.
Recent research from ESG uncovered that two-thirds of cybersecurity leaders believe a dedicated bot mitigation solution is the best approach. That’s not an accident: security practitioners see the value in a team of folks whose only goal is to identify and stop the bots that could break into their web apps.
Ten years of finding bots and ten trillion interactions a week is a lot of practice at spotting even the most sophisticated cybercriminals. Our history in advertising—and the cat-and-mouse game that we’ve been engaged in—these speak to the importance of scale for cybersecurity. It’s a proof point of why cybersecurity leaders need advertisers: they give us the visibility and exposure to spot things others can’t.