Satori Perpectives: Tracking the Ongoing Evolution of Harly Trojan Android Fraud
Read time: 6 minutesJoão Marques, Satori Threat Intelligence and Research Team

Joker, also known as Bread, is one of the oldest and most persistent Android malware families still active today. First tracked by Google in 2017, Joker remains a major threat, accounting for 38% of identified malicious apps detected according to Zscaler’s 2024 Mobile Threat Report.
Initially, Joker focused on SMS fraud, but quickly evolved into toll fraud, automatically subscribing users to premium services while keeping the process hidden from view. These unauthorized subscriptions happen via the Wireless Application Protocol (WAP) billing service, a feature originally designed to simplify purchasing digital content by charging it directly to users’ mobile phone bills.
Joker is mainly known for downloading malicious code from one or more command-and-control (C2) servers and loading it during execution. However, in 2022, Kaspersky identified a Joker variant named ‘Harly’ which embedded malicious code within the APK and employed a series of decryption techniques to run it. In this variant, the C2 servers are primarily used to track infected devices and manage the subscription process.
The Satori Threat Intelligence team regularly investigates various fraud threats that could impact our customers and partners. During our investigation of Harly, we uncovered 95 malicious applications that were hosted in the Google Play Store. We collaborated closely with our industry partners and Google to promptly remove these malicious applications, helping protect users from further harm.
What Does a Harly Application Look Like?
These malicious applications are often disguised as common, legitimate apps, such as games, wallpapers, flashlights, and photo editors, making it easier for users to unwittingly download them. To evade detection, the malicious payload is sometimes hidden in the app’s resources or assets, or even embedded within a native library, making it harder to identify during the review process.
Although these malicious apps often receive tens or hundreds of thousands of installs within a short timeframe, they usually lack genuine user reviews. This suggests that the installs may be artificially inflated using bots to make the app appear more legitimate for real users to download it. The screenshot below shows an example of a Harly application.
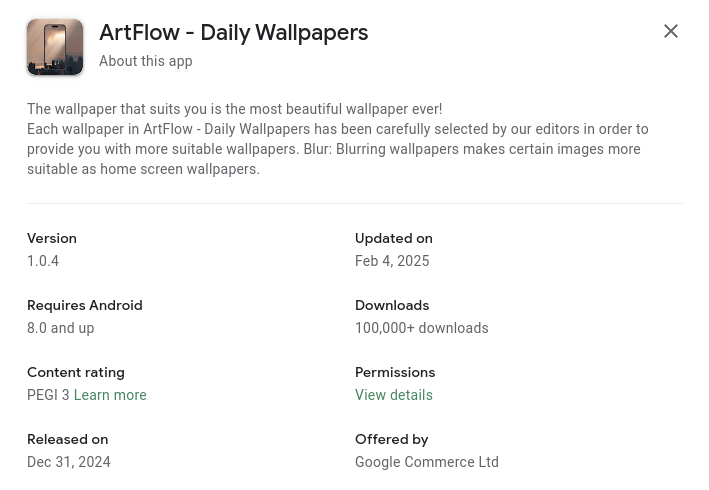
How Does a Harly Application Work?
Toll fraud applications like Harly fraudulently subscribe victims to recurrent paid services like games, wallpapers, or ringtones without the user’s awareness or interaction. To achieve this, the malware carries out a series of actions to automate the subscription:
- The malware visits the subscription page in the background
- Parses the page to perform automatic clicks to submit the subscription
- Intercepts a PIN SMS to confirm the subscription
- Sends the PIN to the subscription page
- Hides the PIN SMS to remain undetectable by the user
Joker and Harly are prominent examples of toll fraud malware. Joker typically does not have the malicious code in the application, instead, it uses C2 servers to download this code and load it during execution. This approach helps the malicious application avoid detection via analysis of the application source code, but these C2 communications can be easily detected when monitoring the application’s network traffic. While Harly also loads the malicious code during execution, this code comes bundled with the application already, usually in the form of an encrypted file or inside an obfuscated native library, making it much harder to find.
Since the malicious code is already within the application, Harly uses cloaking techniques to hide the malicious behavior so it may be kept undetected for the longest time possible. The two most notable techniques are the usage of code obfuscators like BlackObfuscator, a Java Control Flattening Obfuscator, and the use of native libraries created in languages like Rust or Go, or protected with OLLVM. The figures below illustrate two examples: the first using BlackObfuscator to obfuscate code, and the second one using a suspicious native library that contains the malicious code encrypted inside.
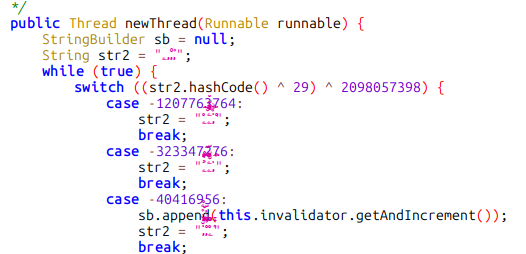
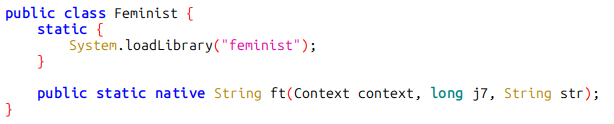
During our investigation of the Harly apps, we found that the native library, developed in Rust, contains an encrypted payload. This payload is decrypted into a DEX file and loaded when the application is launched.
This DEX file contains the malicious code responsible for the entire WAP subscription process. It includes a NotificationListenerService that reads the PIN for the subscription and hides the notification message, executes JavaScript to perform the subscription automatically, and communicates with the C2 server which manages all these operations.
Tracking Harly via Infrastructure
While investigating these applications, the Satori team discovered that the threat actors inadvertently exposed crucial information about their infrastructure, listing domains, IPs, endpoints, and even encryption keys used by the applications since 2020. Revisiting previously analyzed applications, we found the same domain and endpoints that were present in the code and exposed information and successfully used the decryption key to decrypt all C2 communications.
We were also able to discover an endpoint exposing data containing a list of both old and new applications, including those available on the Google Play Store, with a total of 243 apps, all created from 2023 onwards. A second endpoint exposed a list of JavaScript entries designed to automate clicks, bypass captchas, and perform other tasks required on different subscription pages. With this information, we were able to monitor how the threat was developing by tracking new C2 domains and applications even before they were published on the Play Store.
How HUMAN Turns Threat Intelligence into Ongoing Protection
The Satori team actively collaborates with partners to ensure these malicious applications are banned from the Google Play Store and removed from users’ devices and continues to monitor and investigate this threat by tracking new applications that may emerge.
At HUMAN, we directly integrate findings from these investigations into our products, providing our customers with proactive protection. By identifying and tracking threat actor infrastructure in real-time, we enhance the capabilities of HUMAN’s Ad Fraud Defense and Bot defense solutions, ensuring robust defense against evolving fraud threats.
Explore more from the Satori Threat Intelligence and Research team:
- Disrupting BADBOX 2.0: Discover how our team uncovered and disrupted a complex operation targeting consumer devices.
- Reverse Engineering BADBOX 2.0: Delve into the technical analysis behind dismantling BADBOX 2.0.
- Examining Threat Activity During the Big Game: Track how threat actors exploit major sporting events.