Since we released BADBOX 2.0 on March 5, HUMAN has continued tracking the threat actors responsible for it and has continued our disruption of their campaign. Working with Google, Trend Micro, The Shadowserver Foundation, and other partners, we’ve deployed a multi-faceted strategy to disrupt their operations. Our goal is to demonetize the actors behind BADBOX 2.0 by tackling both the backdoored devices and the specific fraud schemes they conducted via these devices.
In this article, I’ll provide an update on our disruption efforts so far, though the investigation–led by HUMAN and our partners–is far from over. Given that the threat actors behind this operation reside in countries without extradition treaties, the demonetization of their fraud schemes remains the most effective tool for disrupting their activities.
The clock starts… last year: Disrupting BADBOX 2.0 ad fraud
Our first order of business was to demonetize the two largest ad fraud campaigns the threat actors engaged in through BADBOX 2.0: one involving hidden ads and the other involving hidden webviews and automated browsing to HTML5 games. Last year, HUMAN implemented markers in our products to block this fraudulent ad traffic from impacting our customers. A few weeks later, the threat actors changed the tactics they were using to get around the blocks, and we blocked them again.
Ultimately, they abandoned the advertising fraud aspect of the campaign, just like in the original BADBOX campaign. The graph below shows the very real impact our team had on reducing the profitability of the ad fraud portion of the campaign–you can see both points at which we launched mitigations and the point at which the fraud eventually subsided.
Timeline note — 6 Jun 2025: The FBI’s latest PSA (I-060525-PSA) recognises Human Security’s disruption work and places the BADBOX 2.0 device count in the millions. Details: https://www.ic3.gov/PSA/2025/PSA250605
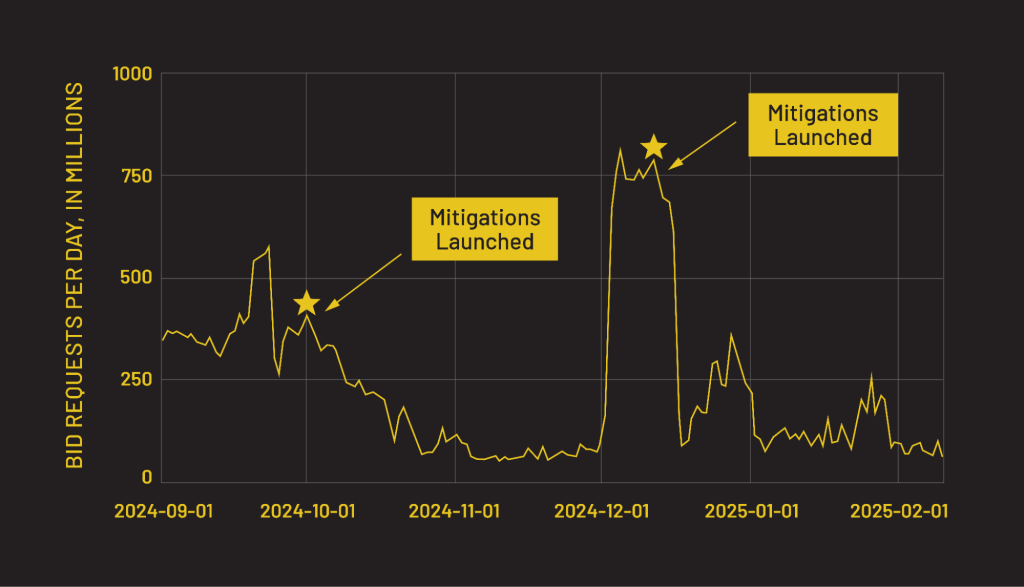
What about the residential proxy network?
As you may remember from the BADBOX 2.0 technical report, the BADBOX 2.0 threat actor, MoYu sold access to the proxy network made up of the backdoored devices via the IpMoYu residential proxy service. Other threat actors purchased access to the network in order to conduct various types of cyberattacks; HUMAN observed a wide variety of attacks, including account takeover (ATO), fake account creation, scalping, scraping, and ad fraud.
We disrupt these activities in two ways. First, HUMAN’s bot defense solution mitigates these bot-driven attacks from affecting our customers, which addresses the second-order effects of the residential proxy network. However, we also wanted to more directly disrupt the actual proxy network itself by taking down the backdoored devices at their source.
Disrupting the backdoored devices
HUMAN worked very closely with our partners at Google and The Shadowserver Foundation to directly disrupt the backdoored devices themselves. In addition to sharing intelligence with these organizations and others, we were able to sinkhole several of the BADBOX 2.0 domains through action by The Shadowserver Foundation. Nearly 500,000 devices, almost half of those we estimated were impacted by the BADBOX 2.0 backdoors, are now beaconing to these sinkholes. This means that the threat actor can no longer control these devices and use them for fraud. Check out the graphic of the worldwide impact the sinkholing has had (thanks to The Shadowserver Foundation) in Figure 2:
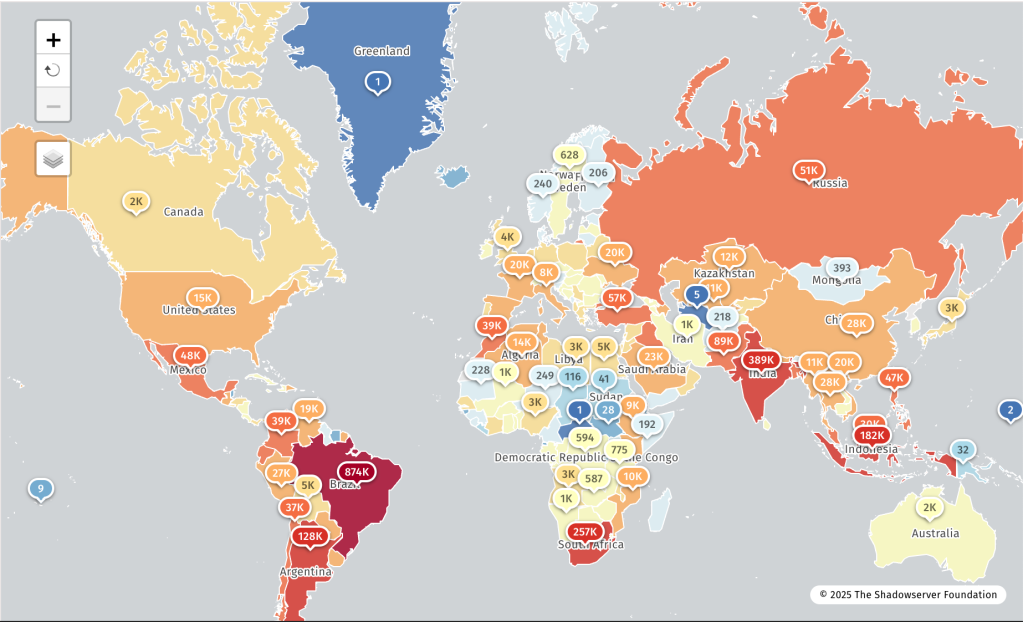
As you can see, the sinkholed device volume per country closely aligns with the overall device volume we saw during the investigation. By sinkholing these domains, we reduce the number of devices under the threat actors’ control and further undermine the profitability of their operation.
The BADBOX 2.0 operation used over 200 backdoors in both applications and devices, including the Vo1d backdoor. In addition to those from BADBOX 2.0, The Shadowserver Foundation also sinkholed domains associated with Vo1d and Vo1d 2, a newer version of the original Vo1d backdoor. If we take into consideration all three sets, we can see in Figure 3 that the overall impact was around 3.5 million unique IPs beaconing to the sinkholed domains to date:
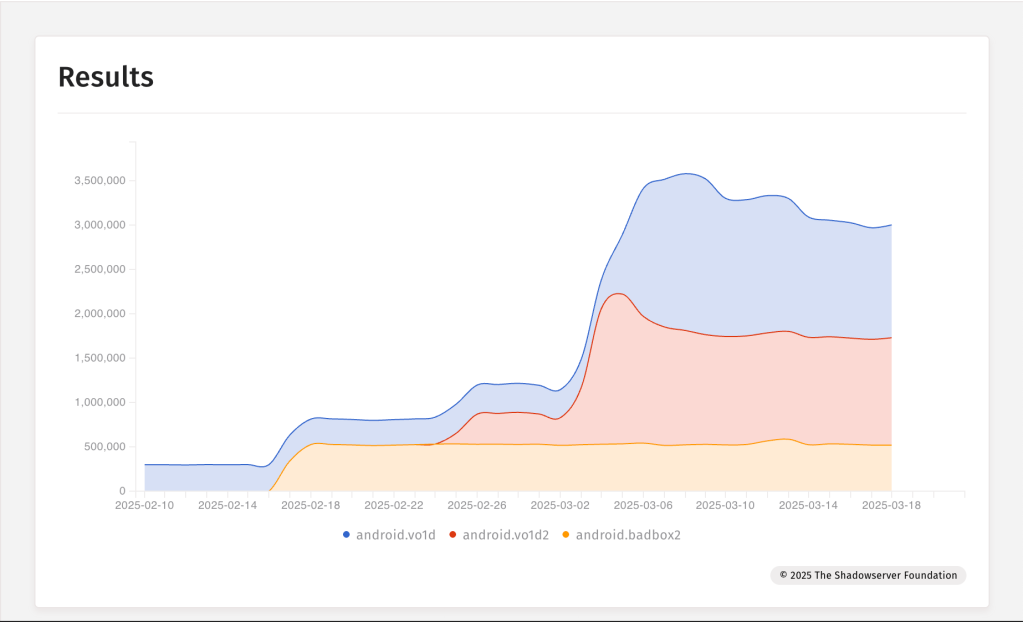
As the threat actors continue to implement new TTPs, we continue to follow them and update our defenses in the Human Defense Platform as needed. This is just the beginning of the disruption operation against BADBOX 2.0, and this remains an ongoing operation that HUMAN Security continues to work on with our partners.
What to learn more about Satori Threat Intelligence? Get an overview of our team and disruption efforts here.
Or attend our upcoming webinar to discuss the threat intel behind the BADBOX 2.0 disruption with the Satori team:
About the Shadowserver Foundation:
The Shadowserver Foundation is an altruistic not-for-profit organization (NPO) working to make the Internet more secure for everyone. Shadowserver has unique sources, a global vantage point, and partnerships with National Computer Security Incident Response Teams (CSIRTs), Law Enforcement, industry, and security researchers worldwide. It works collaboratively and shares information with Internet defenders at no cost to mitigate vulnerabilities, detect malicious activity, and counter emerging threats. Shadowserver’s mission is to make the Internet more secure by bringing to light vulnerabilities, malicious activity and emerging threats, and is driven by the vision of a secure, threat-free Internet. It is funded through a variety of grants, sponsorship,s and donations from organizations who value the public benefit services Shadowserver provides for free to the whole Internet.

