How to Focus and Accelerate Security Investigations with HUMAN Sightline
Read time: 5 minutesAlexa Levine
HUMAN Sightline provides unprecedented visibility into isolated threats, revolutionizing security teams’ investigative capabilities. It is powered by HUMAN’s secondary detection engine, purpose-built AI that analyzes traffic data after a block or allow decision is made. Unlike primary detection that directly blocks or flags threats as they first appear, secondary detectio isolates automated traffic into distinct attack profiles based on shared characteristics, behaviors, and evolving attacker tactics. Analysts can access granular insights into each profile’s behavior, including targeted routes, severity, evasion techniques, and capabilities, enabling security teams to adapt their mitigation strategies as threats evolve.
This capability fundamentally changes the way investigations are conducted by moving from manual, time-intensive analysis of generalized traffic data to instant, precise insights into specific attackers. This article will demonstrate the effectiveness of HUMAN Sightline by comparing investigative processes and outcomes before and after the introduction of attack profiles.
How it works
HUMAN Sightline accelerates investigations by immediately providing security teams with detailed insights into specific attacker behaviors. To illustrate its impact, let’s consider a common investigative scenario—understanding what triggered a sudden spike in malicious traffic. The following comparison will show how investigations are typically conducted with traditional tools versus how they’re transformed by HUMAN Sightline’s attack profiles:
Investigating a suspicious spike in traffic
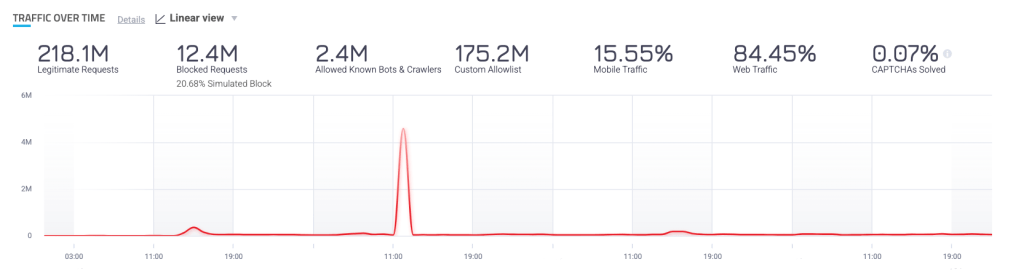
The old way: Attempting to manually isolate the attack traffic using traditional tools
When investigating this spike with traditional tools, analyst would typically zoom in on the spike in an attempt to isolate the attack traffic, but this only effectively isolates the time range of the attack.
You can get some high-level information (e.g., how many requests and top paths), but the other bot traffic during that timeframe skews the data. During traffic spikes, this traditional approach typically shows:
- Aggregated number of requests that combine data from all active bots, including unrelated traffic, making it difficult to isolate the attack-specific activity.
- Top paths visited, which generally reflect all bot interactions rather than highlighting suspicious or anomalous activity. For instance, if bots consistently crawl your entire site, common pages like the login page will dominate this data, obscuring specific attacker paths.
Anything that is not a huge, obvious spike will never stand out, and you won’t even know to investigate it. You can export the data to an external tool for deeper investigation, but this is time-consuming and still doesn’t allow really deep analysis.
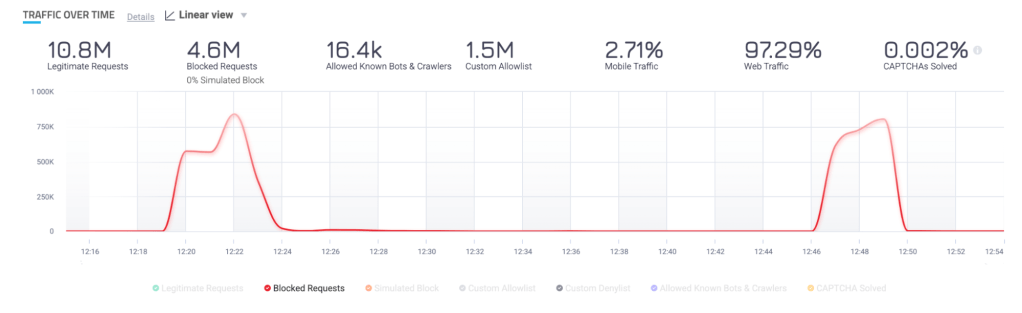
The new way: Automatically isolate traffic with HUMAN Sightline
HUMAN Sightline automatically isolates traffic into individual bot profiles. This is persistent over time and is much more powerful than simply analyzing traffic spikes.
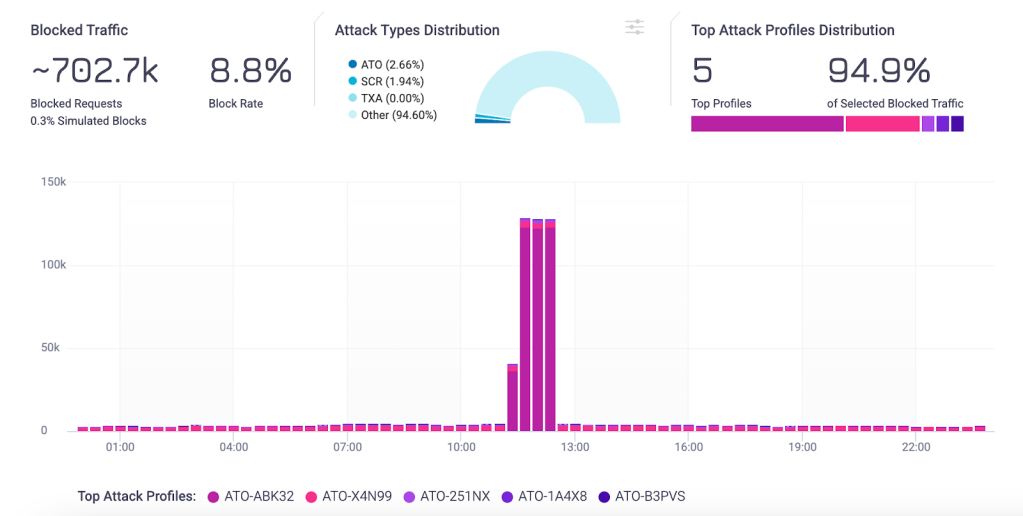
Details are surfaced at the profile level, including the targeted routes, the primary characteristics, and the behaviors of the profile.
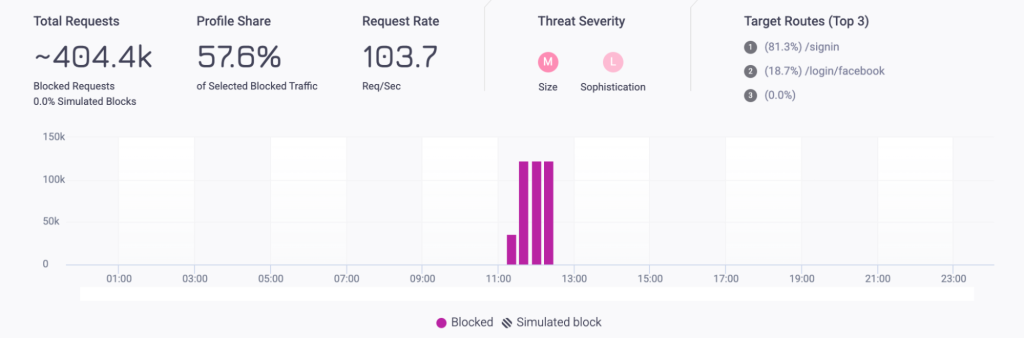
Security teams can isolate the traffic they want to investigate and get details about how that specific profile is behaving with a single click.
Key insights surfaced at the attack profile level include:
- The top paths visited by a profile.
- The number of requests, request rate, threat severity, and associated signatures.
- An explanation of why the traffic was flagged as a bot
- Evasion tactics employed by bots to avoid detection.
- Comparative analysis of bot versus legitimate human traffic (IP addresses, ASNs, devices, browsers, referrers, regions).
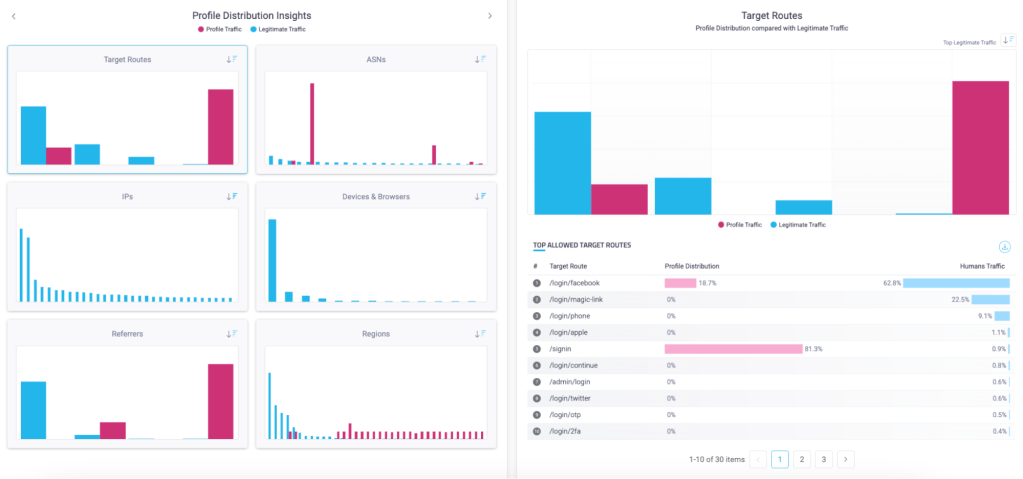
Case study: Grocery retailer discovers product scraping attack
Using HUMAN Sightline, an online grocery retailer uncovered a scraping bot that was only visiting its alcohol pages–which would have otherwise flown under the radar. If they had only looked at scraping traffic in aggregate, the retailer would have only seen that some bots were visiting all of their product pages; they would not have been able to single out the specific alcohol scraper.
This discovery was of great concern to the organization because alcohol sales are heavily regulated in the U.S. and they had not previously accounted for this threat. The retailer updated their threat model accordingly and continued to use HUMAN Sightline to track this scraping bot over time and see the impact of their efforts.
A new era of bot visibility
HUMAN Sightline enables analysts to accelerate their investigations, turning hours of exploratory analysis into a quick, focused examination of contextualized data. With automatic insights on isolated traffic, security teams can fully understand what specific bot profiles are doing on their application. HUMAN Sightline is now included for all Bot Defender customers. Reach out to book a demo today.