Satori Perspectives: Examining Threat Activity During the Big Game
Read time: 6 minutesGabriel Cirlig, Satori Threat Intelligence and Research Team
The Super Bowl signals more than just the end of the American football season—it also marks the tail end of a high-risk period for account takeovers (ATO) and sports-related fraud. Year after year, attackers eagerly await major sporting events, capitalizing on heightened user engagement and transaction volumes to make a quick profit. There are a lot of misconceptions out there about how the deep and dark web works, and about the economics of cybercrime. We decided to shed some light on the cyclical, event-driven nature of fraud and account takeovers, especially around major sporting events like the Super Bowl. Using attack and threat intelligence data from this year’s Super Bowl, we’ll show you real-world trends in attack patterns—so you can recognize these signals and protect your accounts in the future.
How threat actors prepare for the big game
For sports-related platforms, championships and major events like the Super Bowl are the biggest business events of the season. They drive spikes in user registrations, ticket purchases, betting activity, and overall spending. As legitimate traffic hits this seasonal peak, dark web marketplaces mirror this flurry of activity, with opportunistic sellers offering compromised accounts, credit cards, or betting logins, while buyers look to exploit them immediately for financial gain. Attackers focus on immediate returns while fan enthusiasm and betting fervor are at their peak.
The months leading up to the Super Bowl witnessed rising levels of illicit data trading and account breaches—particularly around e-commerce and betting platforms. By the time the actual game is happening, most of the dark web marketplaces are dried up, with stolen credentials and compromised accounts already sold and ready for use. Just as fans are glued to their screens, criminals take advantage of unchecked account vulnerabilities and payment flows.
In fact, dark web chatter often ramps up right as the football season starts in autumn. People trade tips and tools for popular betting and ticketing platforms, getting prepared for when user engagement peaks. Compared to other industries—like hospitality, which lacks a clear “off-season”—sports see stark rises in dark web activity aligned with the season kickoff.
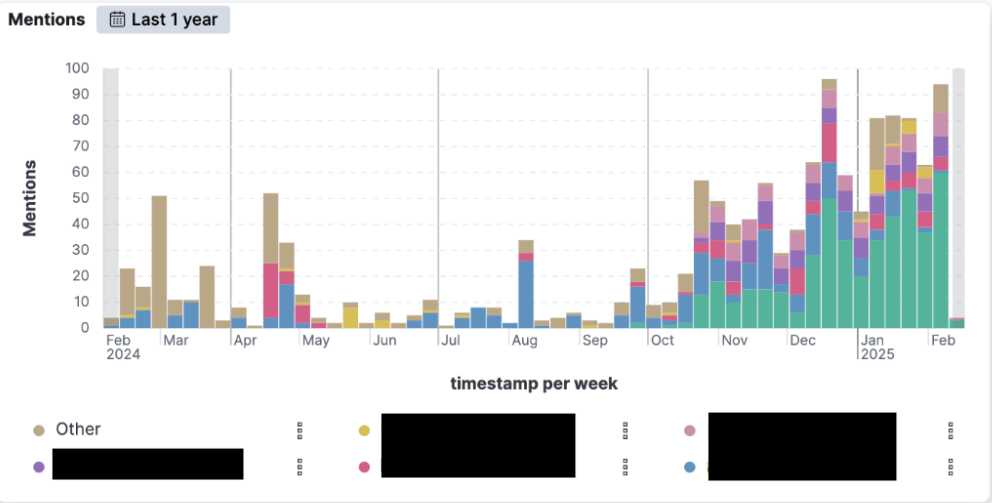
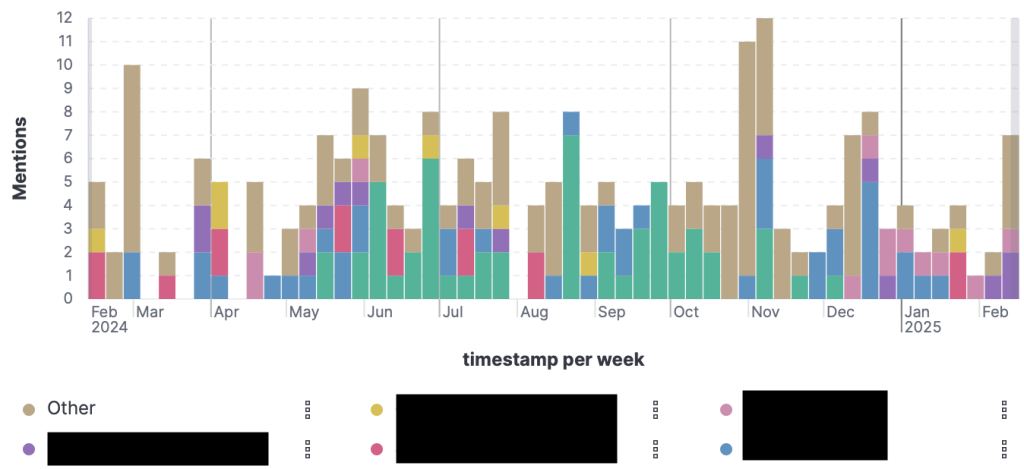
Why would attackers do this? Simple: for a fraction of the total account balance, they can buy credential pairs for betting apps that might yield a 10x ROI. Take the example (in the bottom-right corner the chart below) of an account with almost $6,000 on it, being sold for $500. If attackers can cash out successfully, they walk away with 12 times what they paid—turning this into a lucrative business (if you can stomach the risk of becoming a criminal!).
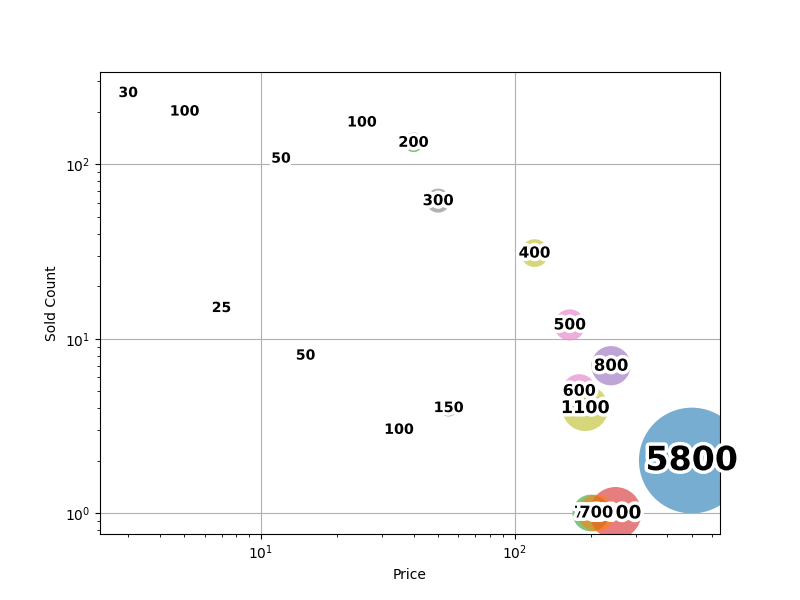
Source: HUMAN Threat Intelligence
Game day: examining the attackers’ playbook
During big events, security teams may be stretched thin or focusing on business-as-usual ops—giving criminals an exploitable gap. However, this does not massively change attackers’ patterns, as they rely on automated tools to crack accounts day and night. Some opportunistic attackers will start hitting a few days before the event, essentially doubling the number of attacks for a few days.
Account Takeover (ATO) is a favored technique: fraudsters deploy bots or manual login attempts on sports-related platforms, hoping compromised credentials will yield winning bets or allow fraudulent transactions.
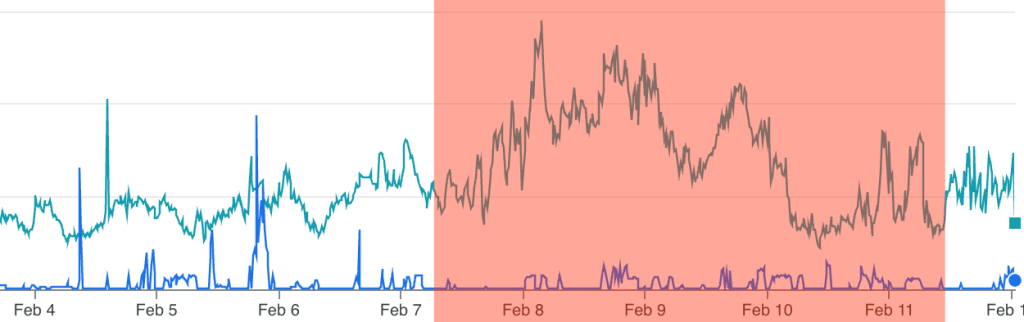
By monitoring attacker chatter and feeding it to our Satori pre-game monitoring, HUMAN provides a quick turnaround that doesn’t just look at raw traffic but also evaluates the potential for abuse. Threats like ATO or scraping closely correlate with viewer engagement, so by mapping these attack vectors, we can often pinpoint each quarter’s kickoff—and even the halftime show—based on the spike in malicious activity.
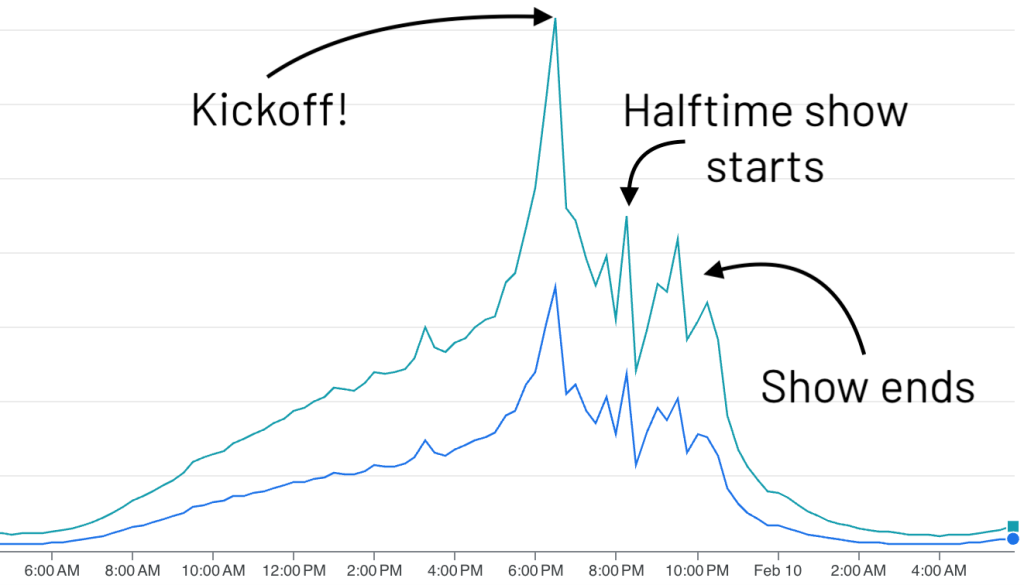
As we celebrate touchdowns and big plays, criminals keep their eyes firmly on the profit. Understanding these cyclical, event-driven abuse trends helps security teams stay one step ahead—even when the rest of us are tuning in for the halftime show.
Intercepting the offense with HUMAN Security
Stay focused on the game—let us handle the attackers. The HUMAN Threat Intelligence team recommends deploying advanced anti-bot solutions, such as Bot Defender, to prevent scraping, credential checking (the repeated testing of logins until one works), and other automated account takeover (ATO) attempts. These measures also disrupt the automated tools cybercriminals rely on to compromise user accounts.
Credential Intelligence minimizes the chances of successful “monetization” by blocking the use of stolen credentials. Meanwhile, Account Defender curbs the success of refund fraud, subscription scams, gift card cracking, and cookie theft—providing comprehensive protection against the threats detailed in this report.
Fraudsters don’t just target the big game; they ramp up their attacks at every major sporting event—from the World Cup to March Madness—often kicking off in mid-October. Fans should safeguard themselves by enabling multi-factor authentication (MFA), using strong passwords, and avoiding phishing links. Sports betting and e-commerce platforms must bolster their anti-fraud defenses during peak traffic periods. Ultimately, cybercriminals capitalize on predictable event spikes, timing their campaigns to coincide with surges in user activity.