Satori Threat Intelligence Alert: Scallywag Extensions Monetize Piracy
Read time: 10 minutesSatori Threat Intelligence and Research Team

Researchers: Louisa Abel, Nico Agnese, Haniya Ali, Mathieu Bissonnette, Will Herbig, Lindsay Kaye, Francis Kitrick, João Marques, Vikas Parthasarathy, João Santos, Adam Sell
(This is the third in a series examining ad cloaking operations uncovered and defended against by HUMAN’s research teams. Read our earlier Merry-Go-Round and Camu investigations for more information.)
IVT Taxonomy: False Representation, Undisclosed Use of Incentives
Digital piracy has been one of the enduring challenges of the internet: there will always be a demand for free access to premium paid content. The big question for would-be digital pirates is how to turn the risk of stealing and distributing this content into an opportunity to cash in. Some threat actors, like those behind our earlier Camu investigation, pack the pages hosting the pirated content full of ads and stand up alternate, brand-acceptable versions of those pages for the ad tech community to see when they come looking.
The threat actors behind Scallywag—so named for its association with digital piracy—took a more indirect route to monetizing piracy. Scallywag is a collection of WordPress extensions that threat actors install to redirect users from piracy catalog sites or URL-shortening service sites through one or more intermediary cashout sites on which the threat actors stage a bunch of ads, and finally to the promised pirated content or shortened URL.
These extensions lower the barrier to entry for a would-be threat actor who wants to monetize content that wouldn’t generally be monetizable with advertising; indeed, several threat actors have published videos to coach others on setting up their own schemes. Domain cloaking threat models continue to be a pervasive and persistent threat in the advertising landscape and are exacerbated by easy-to-configure schemes like Scallywag. This threat represents another large-scale attempt to abuse advertisers by hiding the (often illicit) source of the traffic and passing off users seeking pirated goods as engaged users visiting blog sites.
At its peak, Scallywag accounted for 1.4 billion fraudulent bid requests a day across 407 cashout domains. Customers partnering with HUMAN for protection from ad fraud are and have been safe from the Scallywag threat.
Stuck in the Middle with Ads: How Scallywag Monetizes Piracy and URL Shorteners
Scallywag is the name HUMAN researchers have given to a collection of four WordPress modules designed to help monetize digital piracy and URL-shortening services. These modules redirect users through one or more intermediary pages to request and render ads before delivering the promised content or shortened URL.
The cashout sites staged by the Scallywag modules include a variety of tactics designed to slow users and maximize the number of ads the pages can request and render. These tactics include:
- Buttons that must be clicked on to advance to the content/shortened URL delivery
- CAPTCHAs that must be solved
- Hard-coded wait times before progress is possible
- Automatic and/or required scrolling through a full page before progressing
- Required navigation through multiple intermediary pages on the same or related domains
These cashout sites, when cloaked, often take the form of a seemingly benign blog with no obvious relationship to the original piracy/URL shortening domains.
Here’s a diagram of what some of the most frequent paths of the Scallywag experience look like:
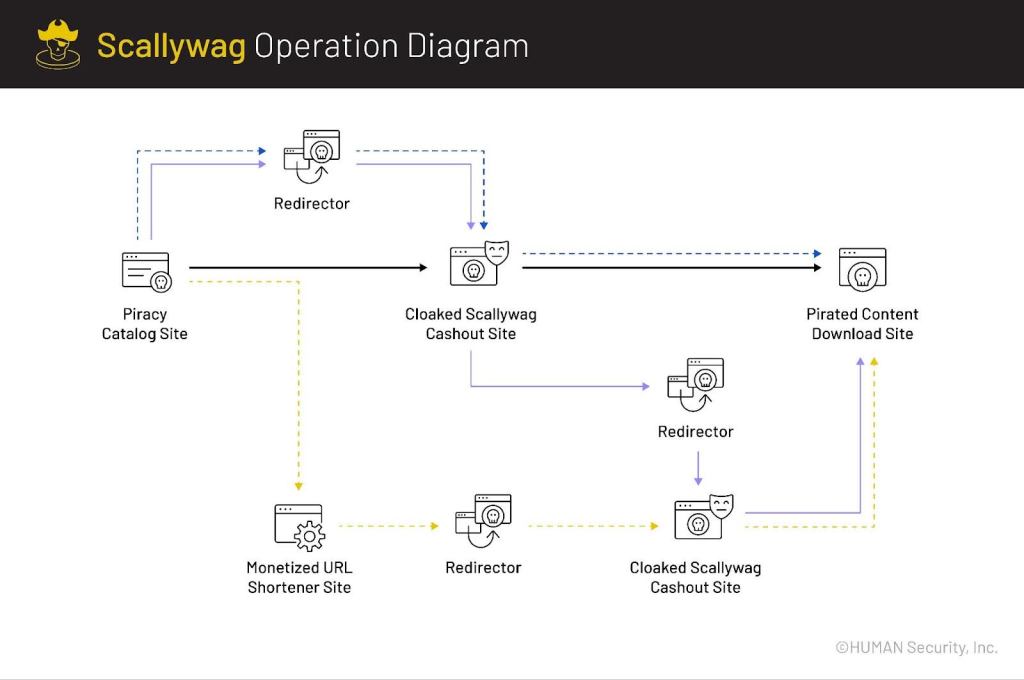
The above diagram represents a typical set of navigation paths. The process begins with a user visiting a piracy catalog site. On choosing the content they want to view, they’re sent on one of several paths, passing through a Scallywag-associated cashout blog (which is loaded with ads and tactics to slow progress) and eventually to their final destination, where the content is hosted.
Here’s what that experience looks like with actual websites:
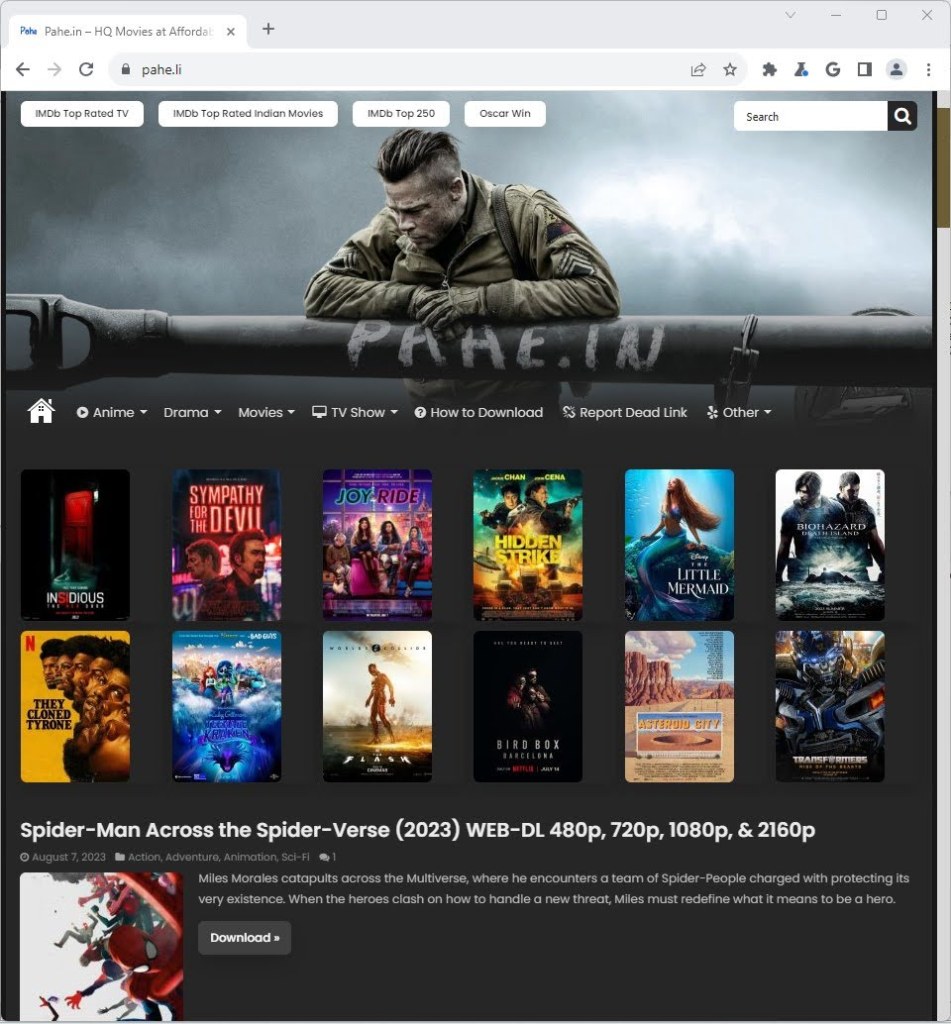
Above, a piracy content catalog site. Note that there are no ads; the content on this page would run afoul of most advertisers’ policies. The user chooses what they want to watch, clicks on the link, and is redirected to a cashout page associated with the Scallywag operation:
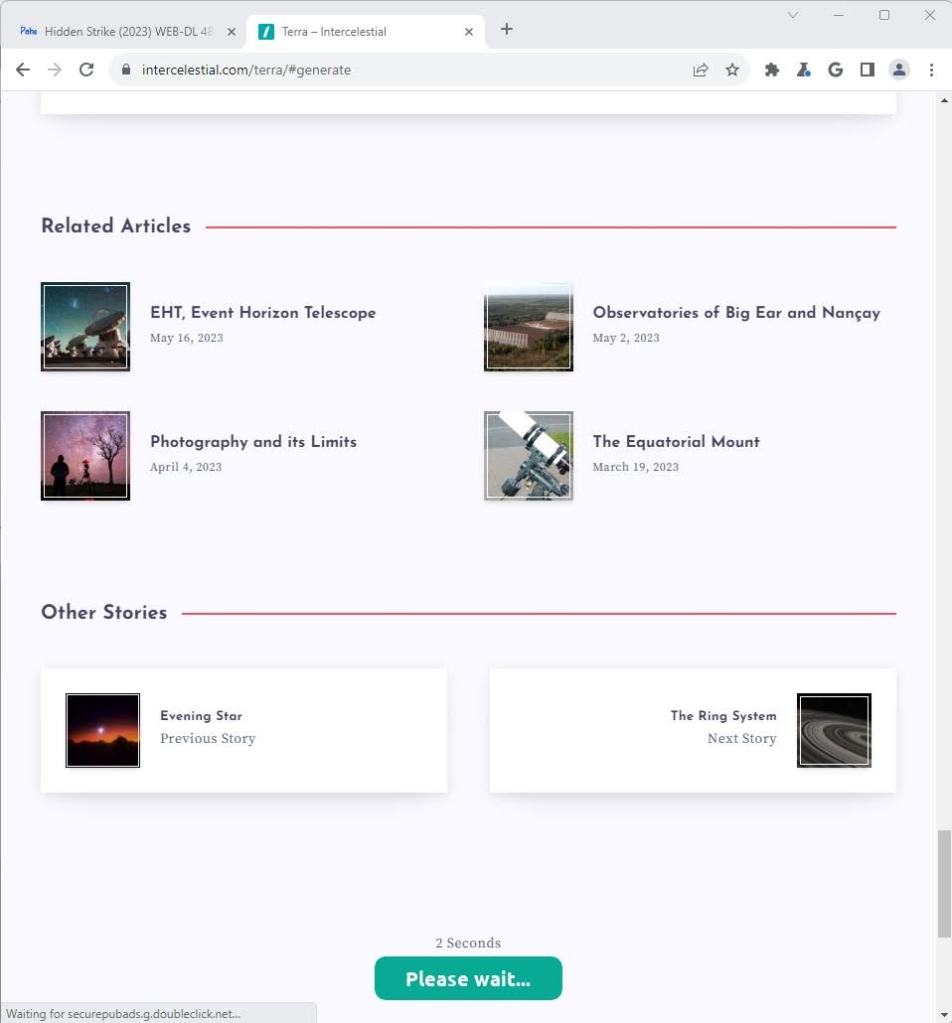
Above is an example of a Scallywag-associated intermediary cashout page. Note the button near the bottom of the screenshot, which reads “Please wait…” and features a timer above it. That timer forces the user to wait for ads to render before they can progress to the next step. Note also the text in the loading bar at the very bottom of the screenshot. That text reads “Waiting for securepubads.g.doubleclick.net”, indicating that an ad network is rendering an ad.
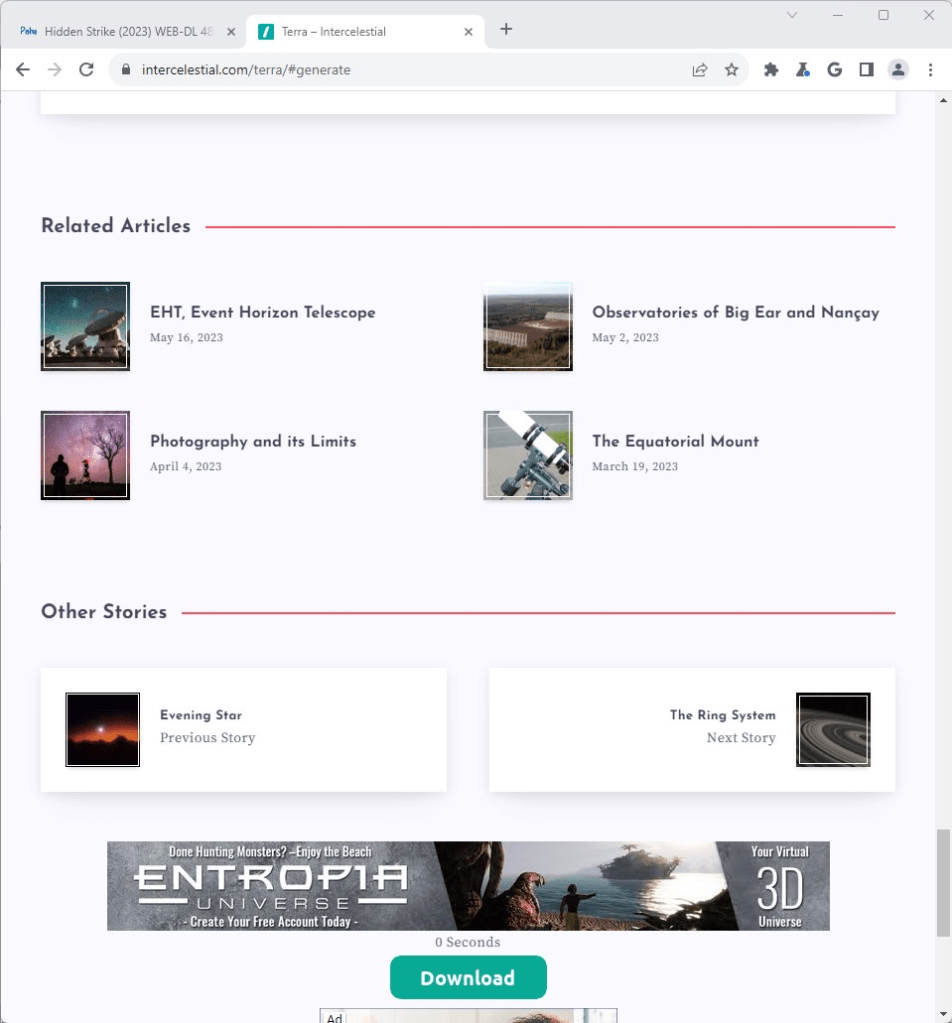
After the timer has run out, multiple ads have rendered, and the “Please wait” button now reads “Download”. From here, the user can now proceed to the pirated content.
The intermediate cashout websites fall under the category of Undisclosed Use of Incentives in the IVT Taxonomy, as users only visit these sites with the intention of moving on to the pirated content.
Additionally, and in a similar vein to the earlier Camu and Merry-Go-Round threats, these sites display ads and content differently when visited directly as opposed to via the piracy or URL-shortening domains:
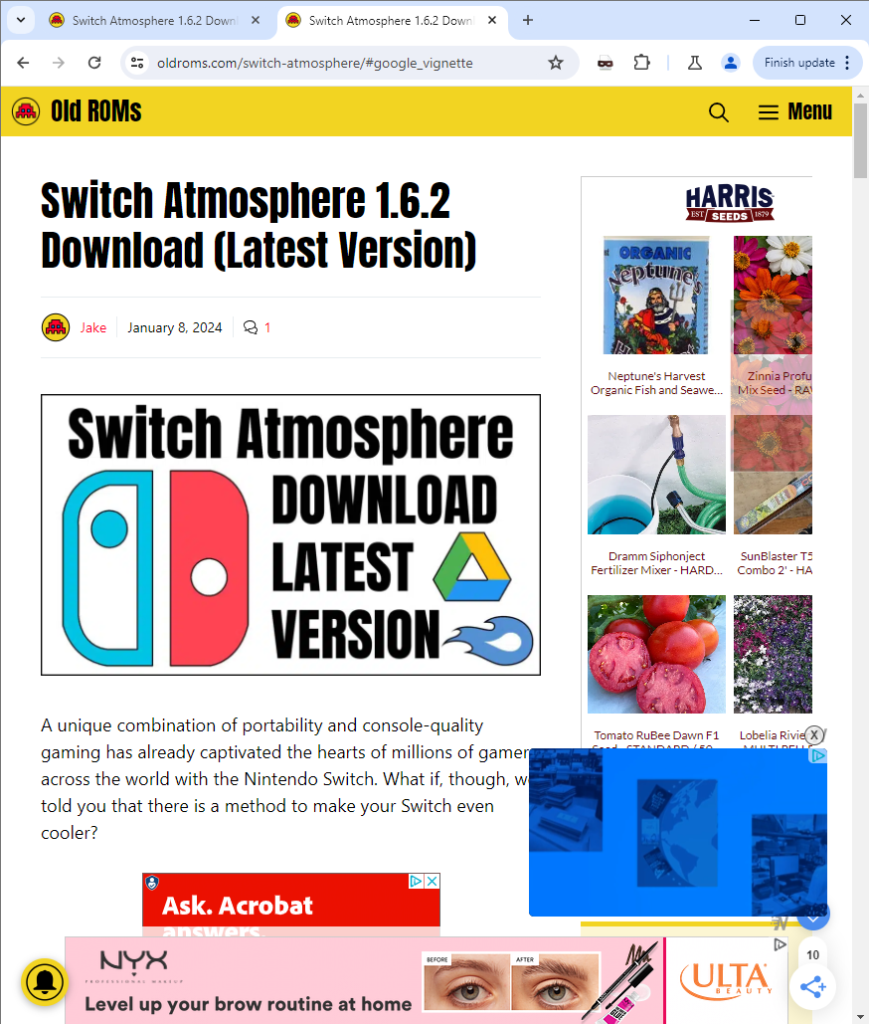
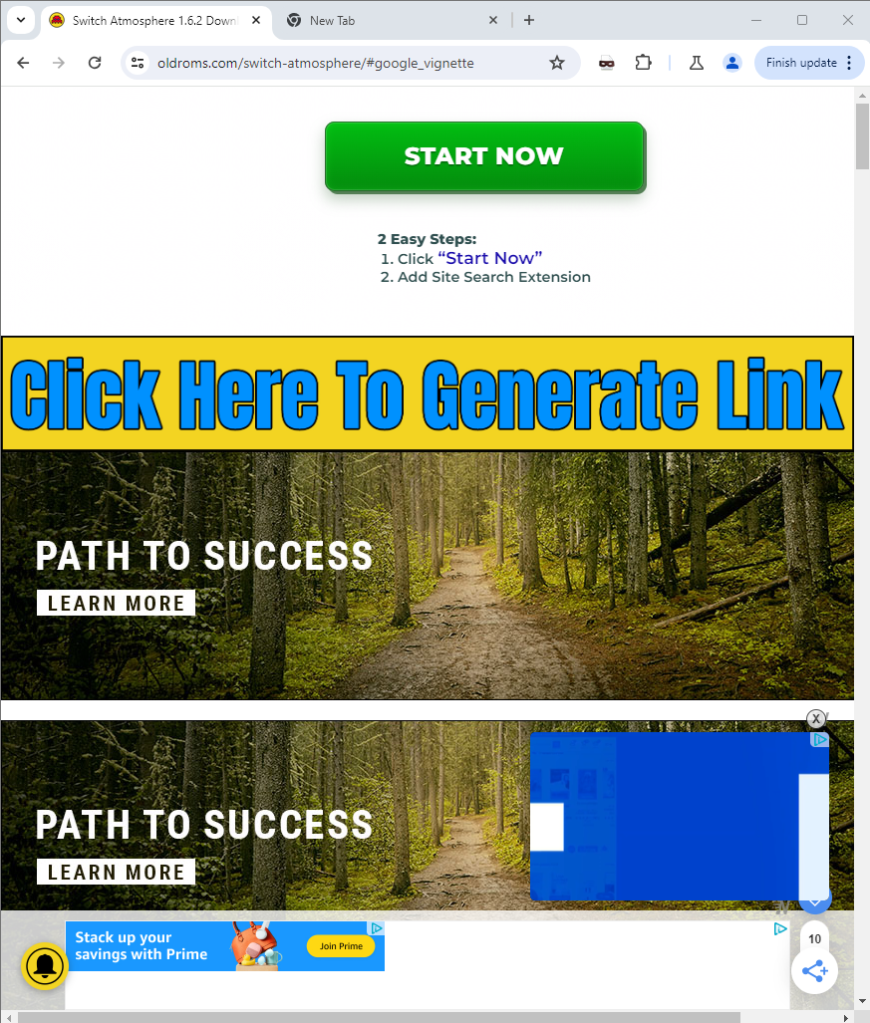
Notice that the URL (and scroll depth) for both screenshots is the same. The screenshot on the left is the cashout site when visited directly – ads load, but the content is benign. The screenshot on the right, however, is what shows when arriving on the cashout site while using a threat actor-owned URL-shortening service. There’s no content at all, just a collection of ads surrounding a banner telling the user to click to generate a shortened URL.
In another example:
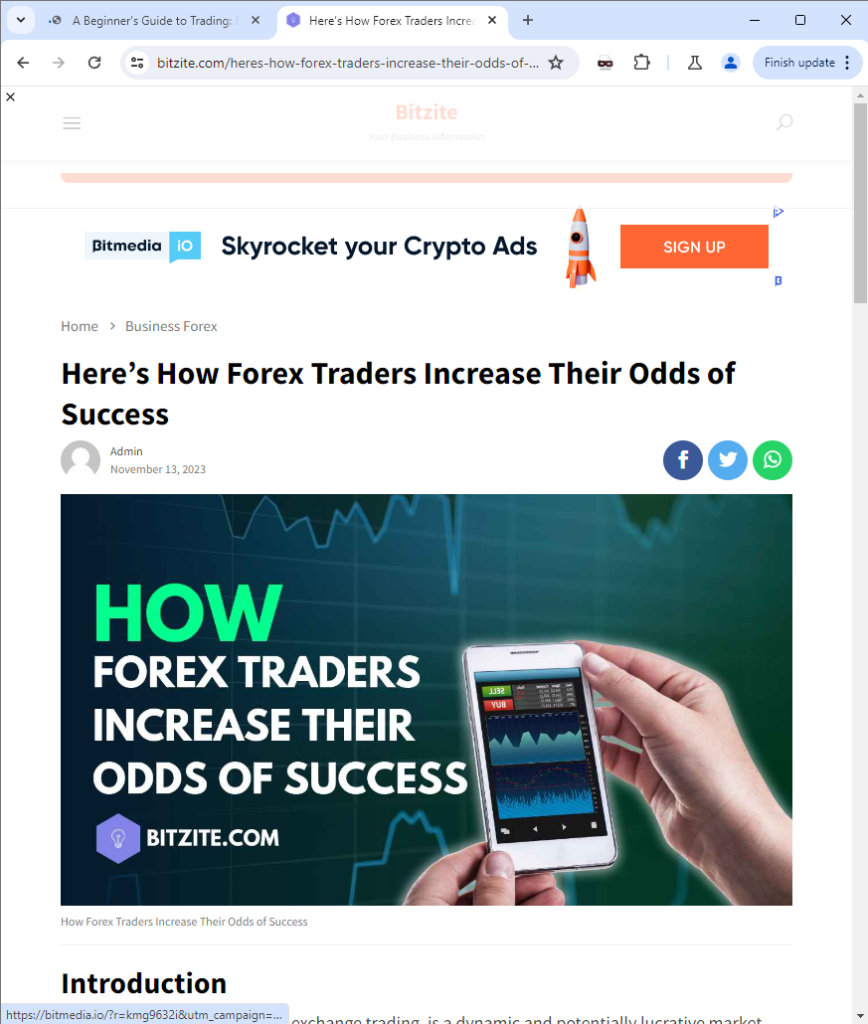
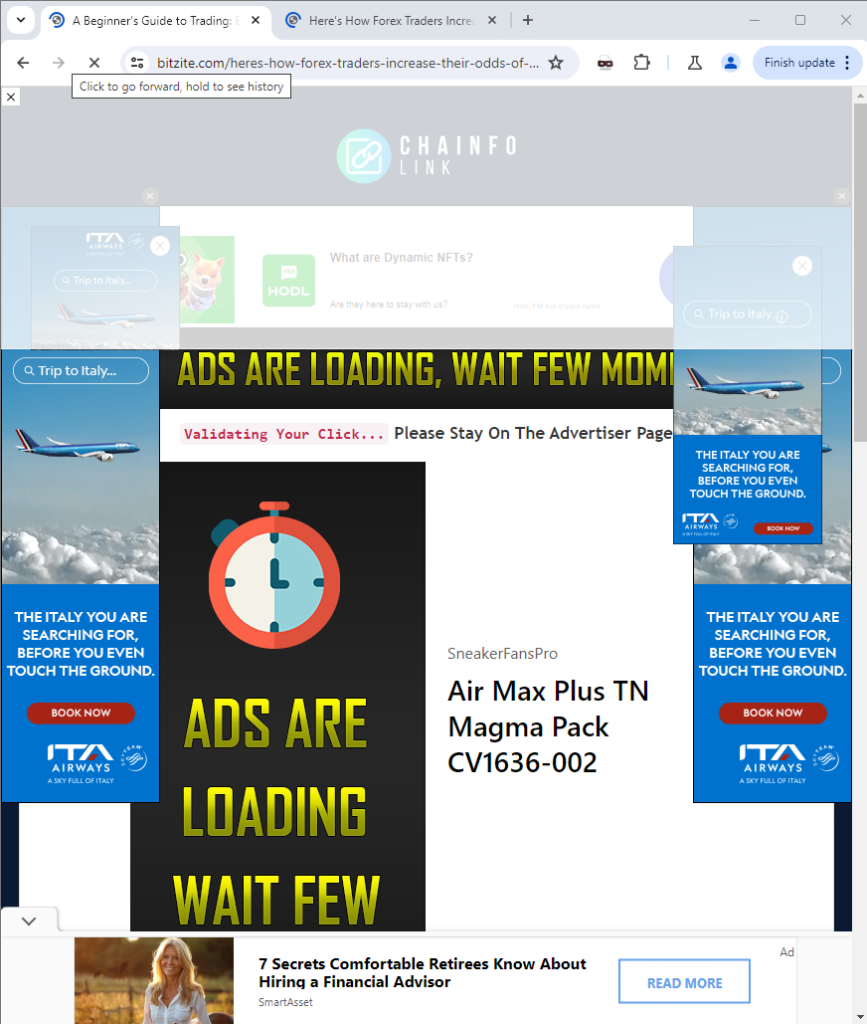
Notice again that the URL and scroll depth are identical. The screenshot on the left—which was how the cashout site looked when visited directly—features an ad on a benign cryptocurrency blog. The screenshot on the right, however, overloads the site with no fewer than seven ads (with visible warnings to a user to allow those ads to load).
This cloaking behavior falls under the category of False Representation in the IVT Taxonomy.
Researchers found that most Scallywag cashout sites decloak their content (read: render the versions of the pages on the right) using a process called deep linking. The link on the catalog page includes a deep link to a page with a webform, that webform automatically submits and redirects the user to the decloaked version of the desired page. That webform completion tells the website that the user should receive the decloaked version, rather than the benign version.
The Scallywag modules allow a great deal of customization for digital pirates. Several of the actors implementing these modules include a redirection jump through Google, X (formerly Twitter), or other open redirectors before visiting Scallywag domains. This is an effort to sanitize the referrer data and further hide their fraudulent activity from the ad tech ecosystem. Navigating through open redirectors replaces the real referrer (the piracy catalog domain) with Google, X, or the open redirector, and reflects the traffic as organic from the advertiser’s point of view.
Sailing the Seven Seas: The WordPress Extensions Associated with Scallywag
The four WordPress extensions associated with the Scallywag operation are:
- Soralink, which the developer claims was first created in 2016
- Yu Idea, for which the first available documentation dates to 2017
- WPSafeLink, which the developer claims was first created in 2020
- Droplink, for which the first available documentation dates to 2022
Additionally, there’s an extensive library of coaching videos for Scallywag extensions:
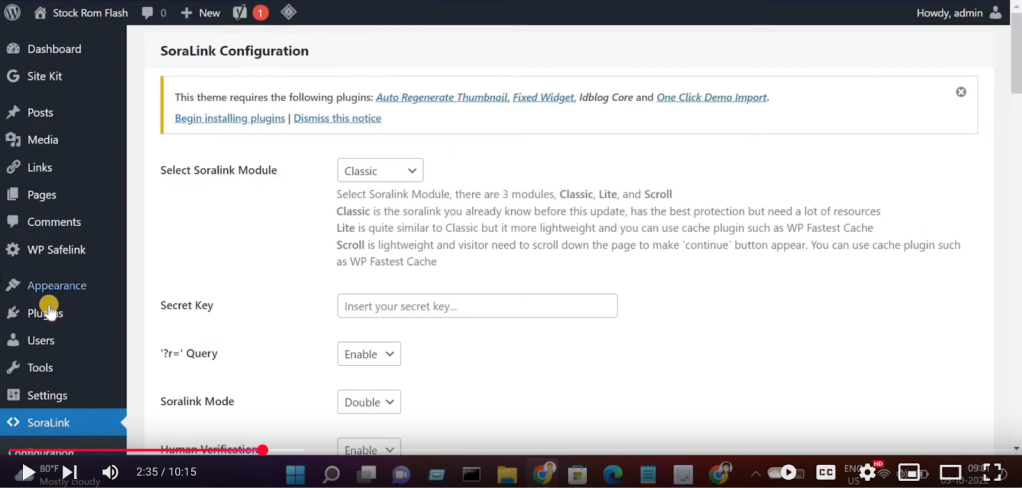
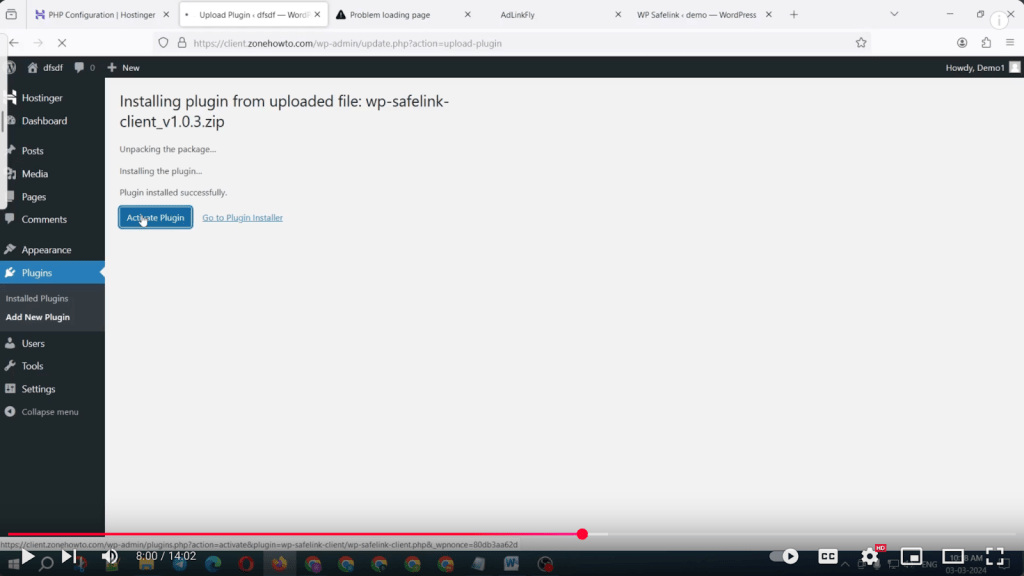
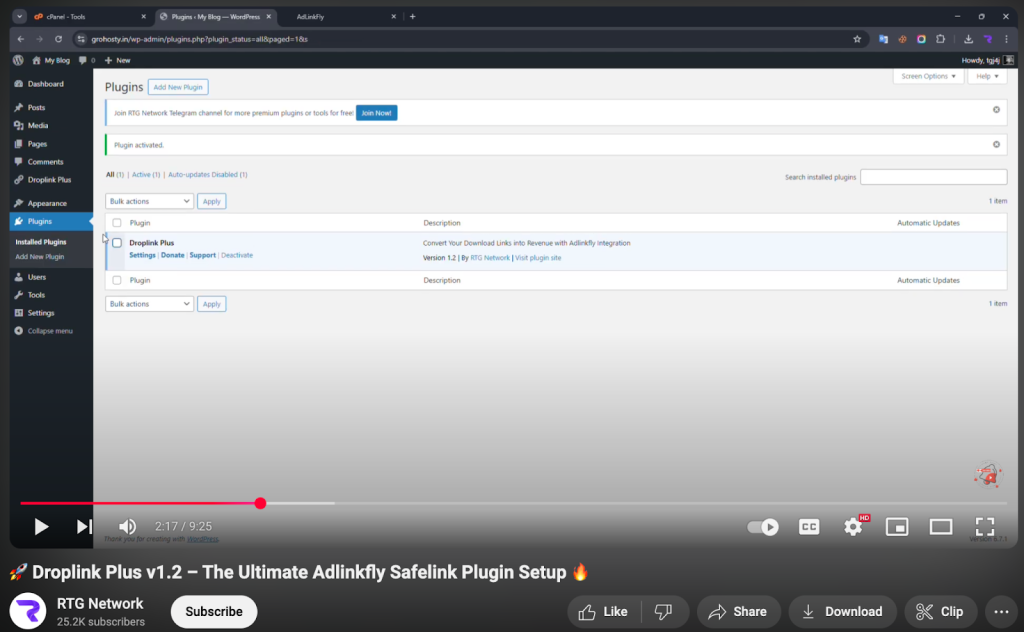
Many of these videos are recorded and staged by individual threat actors using the Scallywag extensions as sources of income, not by the extension’s developers themselves.
Three of the extensions—Soralink, WPSafeLink, and Yu Idea—are sold by their developers to individual threat actors, while Droplink is available for free behind its own Scallywag path (the license and files provided only after navigating through cashout blogs with ads).
Fighting the Pirates: Protecting HUMAN Customers from Scallywag and Watching for Further Adaptations
Customers partnering with HUMAN for ad fraud defense are and have been protected from Scallywag.
HUMAN’s efforts to combat Scallywag are extensive and ongoing. The threat actors have made several adaptations, but each time, HUMAN researchers identify the changes and deploy new protections to enhance the platform:
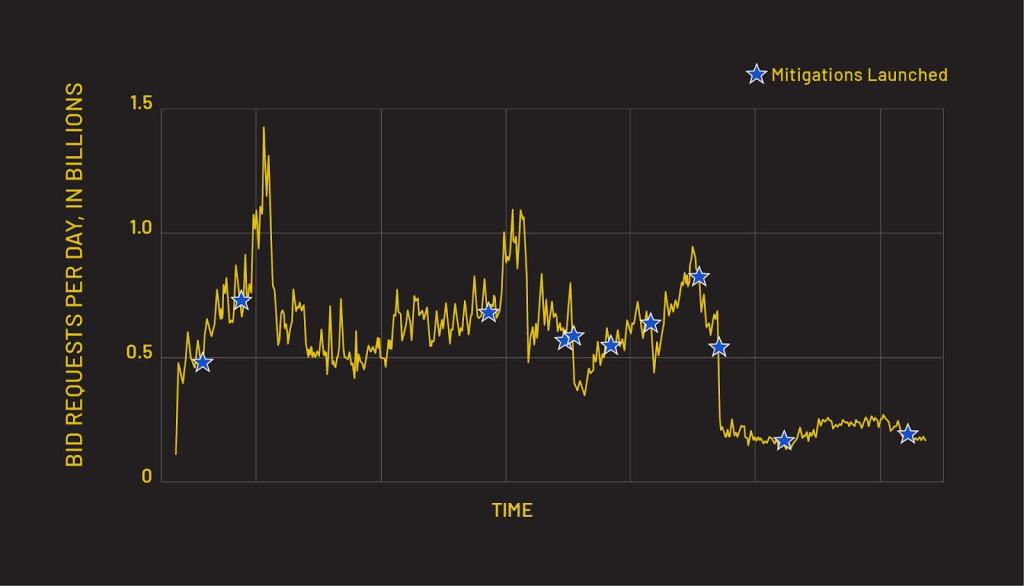
Traffic associated with Scallywag has declined 95% from a peak of 1.4 billion bid requests per day.
Those potential adaptations tend to come in the form of new cashout sites. When threat actors notice their payouts from their cashout sites evaporating due to HUMAN’s protections, they introduce new sites into the mix. This adaptation, commonly utilized by threat actors, is called “Domain Rotation”, and helps threat actors evade simple flaglists. HUMAN’s defenses against attacks like Scallywag go beyond flaglists and key in on behavioral patterns in fraudulent traffic and domains, protecting customers even when new domains are launched.
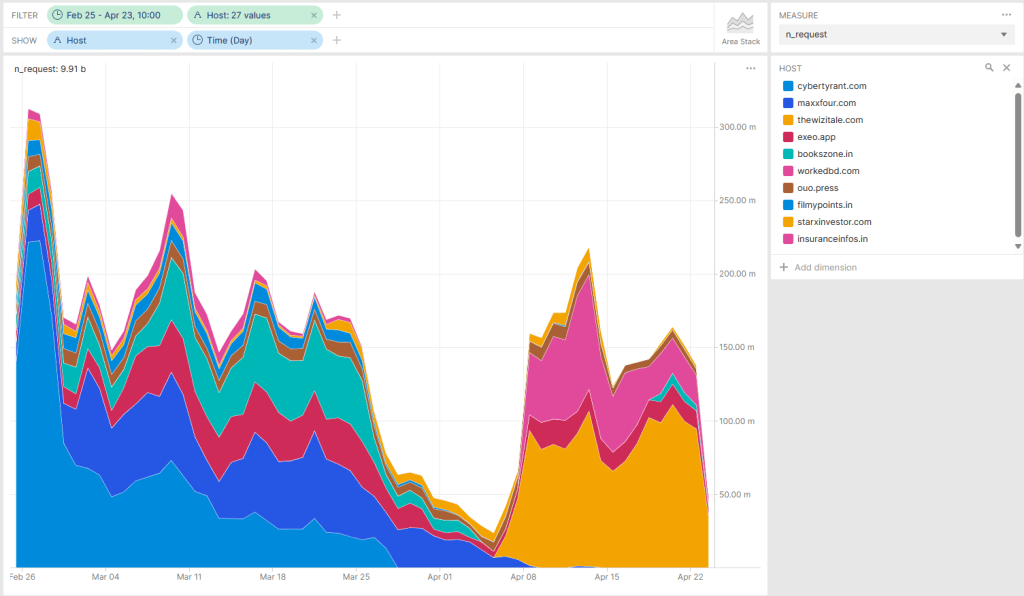
The above is a sample of Scallywag-associated traffic over a two month period in spring 2024. Notice how volume on many cashout sites drops and new sites are launched.
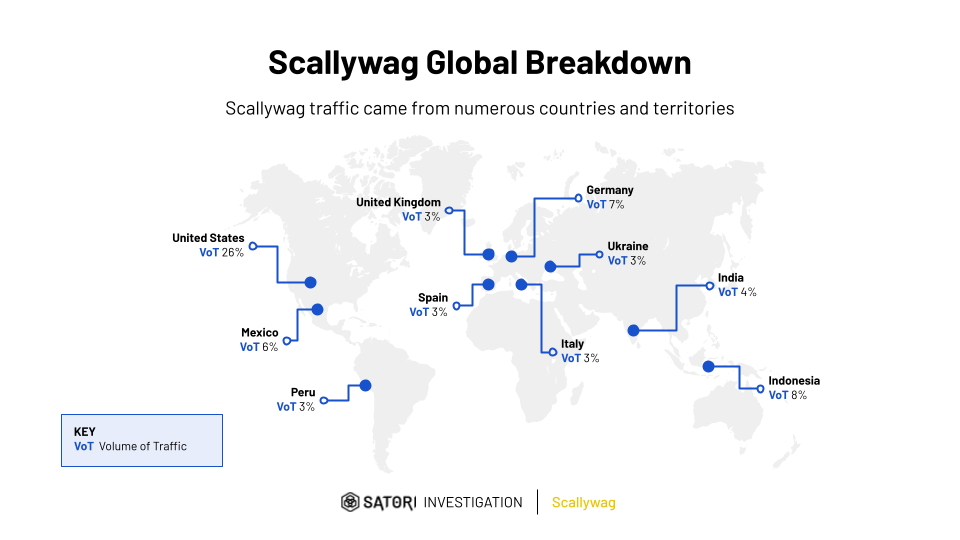
It is important to note that Scallywag is highly customizable by the threat actors who purchase access to the extensions. Each threat actor can react and attempt their own adaptations based on their particular implementation.
Finally, researchers have observed some threat actors abandoning Scallywag-style monetization tactics entirely following HUMAN defenses, pivoting instead to the use of content discovery networks.
A list of all known Scallywag domains at the time of publishing is below.