Cyber 5 — the five days from Thanksgiving through Cyber Monday — is considered the largest shopping period of the year. Online retailers raked in $33.9 billion during Cyber 5 2021, including $10.7 billion on Cyber Monday alone. Although the return to in-person shopping led to a 1.4% YoY decrease in revenue from 2020, the average shopping cart value rose 13.9%, leading to a significant increase in e-commerce revenue.
As with any major online shopping event, e-commerce businesses saw an influx of not only legitimate human buyers, but also automated bots and cybercriminals attempting to steal personal data and make fraudulent purchases.
Fortunately for our customers, PerimeterX was prepared to stop the attacks. Over the course of the five-day period, our platform prevented more than $1.5 billion in attempted fraudulent purchases by stopping the theft, validation and use of account, identity and payment information. In addition, PerimeterX stopped $37 million worth of fraudulent gift card purchases during Cyber 5.
As the leader of the HUMAN’s Enterprise Security Research Team, I want to share some important Cyber 5 trends that suggest what the future of online shopping will look like.
Overall traffic increase during Cyber 5
We saw a steady increase in traffic from late October throughout November, with clear spikes on Black Friday and Cyber Monday. Traffic rose an average of 1.02% each day, until Black Friday, which had an increase of 27% from the prior days. On Cyber Monday we’ve seen a similar jump to the one seen on Black Friday, at 28% over average in the days prior to the Cyber-5 weekend.
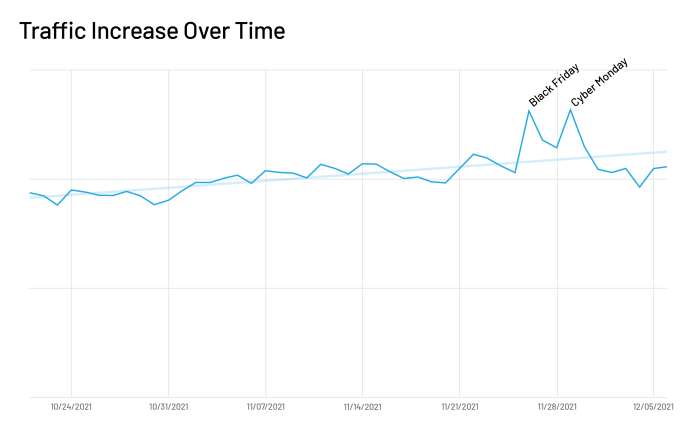
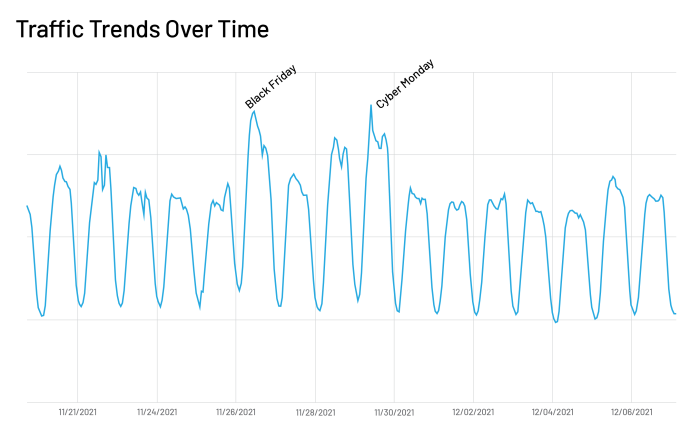
Zeroing in on the specific days in and around Cyber 5, we see that Black Friday and Cyber Monday not only had increased traffic throughout the day, but specifically during 9:00am- 7:00pm PST on Black Friday and 10:00am-10:00pm PST on Cyber Monday.
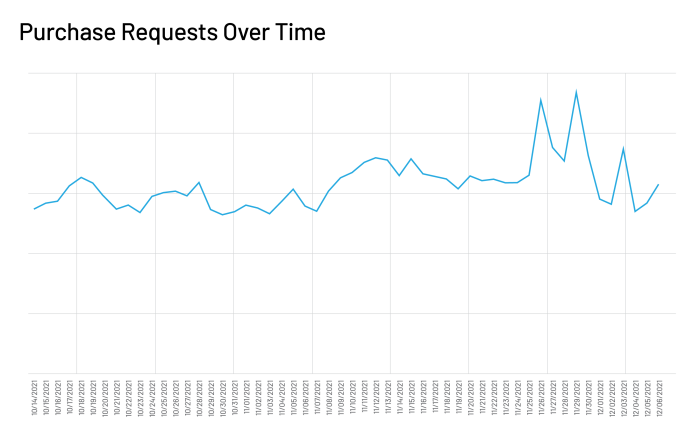
As expected, this traffic increase corresponds to more purchase requests. We saw steady increases during November in purchase and conversion rate, with the biggest spikes on Black Friday and Cyber Monday. The high sales peaks continued into early December, before dipping again the following week.
More scraping attacks during Cyber 5
There was also a spike in scraping attacks at the start and end of Cyber 5. Scraping attacks accounted for 19.17% of total traffic on Thanksgiving, 18.75% on Cyber Monday and 18.98% on the last day of November. Competitors try to use scraping bots to harvest pricing information on specific products and brands, giving them a competitive edge.The data suggests that competitors were scraping prices immediately when companies revealed their Cyber 5 prices, and again when new December prices were posted after the peak shopping event concluded.
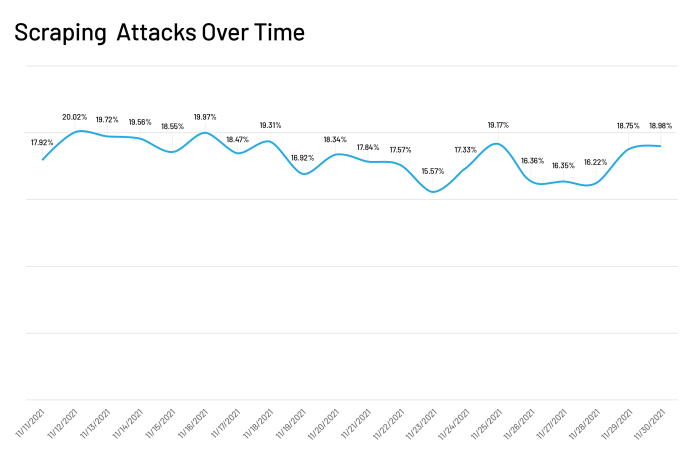
Taking into account the Cyber 5 traffic increase that I discussed above, it is clear that attackers increased their price scraping attacks as traffic increased. This explains the relatively stable percentage of scraping attacks that we observed during the middle of Cyber 5.
Spike in carding attacks before Black Friday
E-commerce businesses are on high alert for bot attacks during Cyber 5, but cybercriminals didn’t wait until then to strike. This year, we saw an increase in both carding and gift card attacks in the days leading up to Thanksgiving. This suggests that hackers were trying to validate credit card and gift card data to sell on the dark web, so they could be purchased prior to Cyber 5 and used during the big sales event.
We saw clear waves of major gift card attacks in the days leading up to Thanksgiving. One major cross-site attack occurred two weeks before the holiday, and accounted for 91.33% of all gift card validation requests across our network during that day. Gift card attacks continued to wax and wane throughout the rest of November, reaching a second peak at 72.88% several days before Thanksgiving day. Overall, HUMAN protected more than $37 million in attempted gift card fraud during this period.
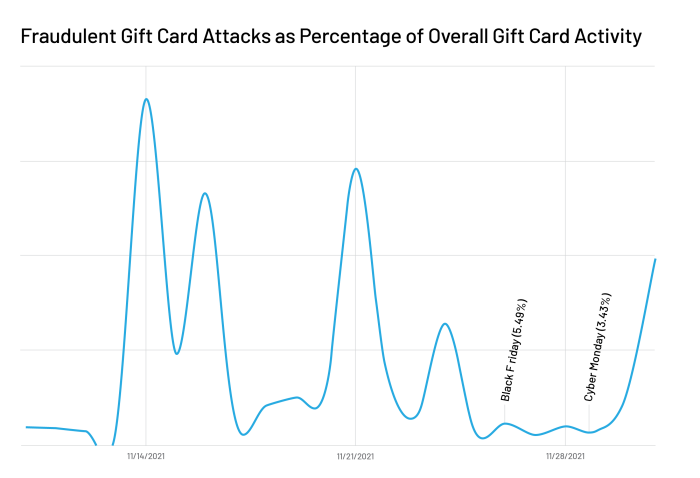
Carding followed a similar pattern. Although the ebbs and flows were less drastic in this case, the percentage of carding attacks was nearly twice as much in the week leading up to Thanksgiving as it was during Cyber 5. Thus, we conclude that carding attacks stayed constant throughout the shopping period, even as traffic increased.
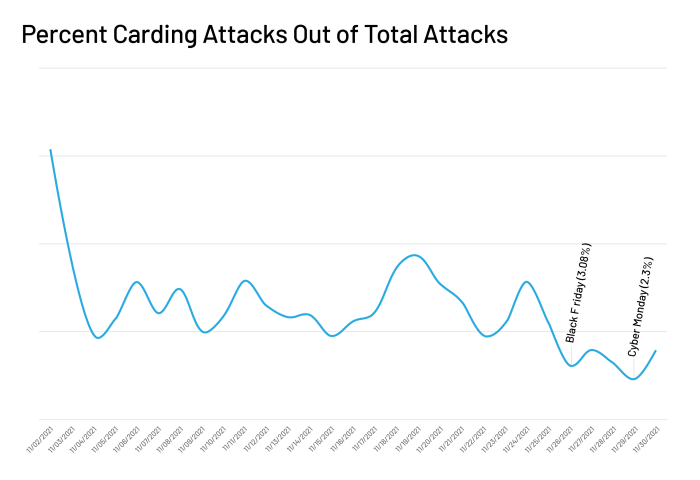
These results show that the days leading up to Cyber 5 are as big a target for bot attacks as Cyber 5 weekend itself. In some respects, these days are even more active as fraudsters prepare for the holiday fraud where they’ll use the stolen gift cards and credit cards. This serves as a wake up call for businesses that are laser-focused on Cyber 5 as the biggest days for potential cyberattacks.
Credential stuffing attacks and ATOs rose during Cyber 5
In the days and weeks leading up to Cyber 5, bot attacks set the stage for the main event: taking over accounts in order to commit fraud. Account access is extremely valuable, and it is clear from the data that this is what cybercriminals were after during Cyber 5.
Validating information — via carding, gift card cracking or credential stuffing — is only one piece of a full attack. The next step is for the cybercriminal to use the valid information to commit fraud, either by doing so themself or selling the information on the dark web for others to use. Hackers launch automated attacks to validate data before Cyber 5 in order to sell the validated information on the dark web prior to the holiday. This allows other cybercriminals to purchase a list of validated credentials and payment information in advance, so it is ready for use during big sales events.
Account fraud is where the money is — and credential stuffing attacks are the first step to a successful account takeover (ATO) attack. During Cyber 5, we identified a rise in both overall logins and in malicious login attempts. Over 74% of all login attempts to online retailers were malicious every day over this period. While the percentage of credential stuffing attempts out of the overall login attempts was steady, this translated to an overall increase in credential stuffing attempts.
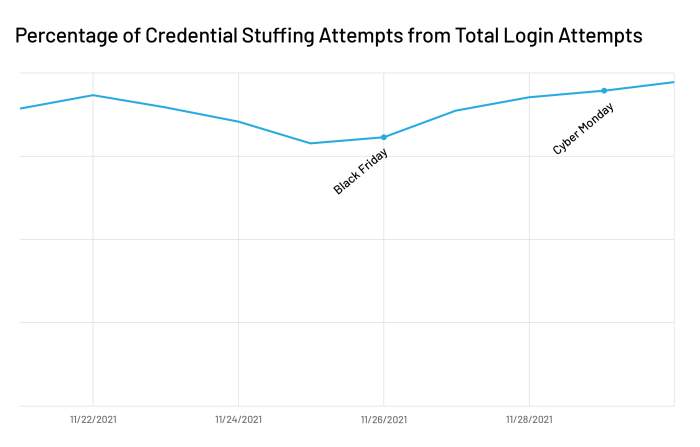
Given the tremendous opportunity to put stolen credentials to use during Cyber 5, it makes sense that there was an increase in credential stuffing activity during this period. And the after-effects of these attacks will go on even after the holiday sales are over. It is interesting to see that credential stuffing attempts for e-commerce customers jumped to 80% of total login attempts on November 30, the day after Cyber Monday, and then to 97.27% of total login attempts on December 1. This indicated that while legitimate traffic scaled down after the large sale events, malicious activity stayed at a heightened level, accounting for a higher percentage of total traffic overall.
Key takeaways
The overall trends that we saw during Cyber 5 and the entire month of November give a preview into the future threat landscape. Cybercrime is a lucrative business, and it no longer consists of one-off, ad hoc attacks during specific shopping periods. Instead, the attack lifecycle is becoming more integrated, continuous and cyclical. One kind of attack can fuel another, propagating and prolonging an attack lifecycle that hits consumers everywhere along their digital journey.
As the digital attack lifecycle increasingly becomes more like an infinite loop than a series of linear steps, HUMAN is proud of its ability to provide a layered defense that mitigates attacks wherever and whenever they occur. Today’s e-commerce merchants demand a solution that not only stops the fraudulent use of account information, but also disrupts the web attack lifecycle.
