Investigators: Gabi Cirlig, Michael Gethers, Lisa Gansky, Dina Haines
Those of us who are of “a certain age” have fond memories of the first time we played what are now considered “retro” video games. Perhaps the biggest thing that sticks out about games of that era is the vibrant, 8-16 bit color palette.
The White Ops Satori Threat Intelligence and Research Team recently identified a series of 240+ Android apps, engaging in deceptive behavior by using out of context (OOC) ads. These apps make it appear that ads are actually coming from popular applications and social media platforms including Youtube and Chrome. We dubbed this investigation “RAINBOWMIX” as a nod to the colorful games of years ago. The RAINBOWMIX assortment of apps garnered more than 14 million downloads, and at its peak had more than 15 million ad impressions per day.
At first glance, RAINBOWMIX apps seem to work as advertised, although their quality likely leaves users wanting. They are often nothing more than Nintendo (NES) emulators ripped from legitimate sources or low quality games; all of the apps associated with the RAINBOWMIX operation have been removed from the Google Play Store. While not a very sophisticated tactic, the use of packers allowed these apps to bypass certain security protocols.
A packer is software that saves a bit of space and obfuscates the final payload. When the appropriate time comes, the packer will “unpack” what it contains. They are now frequently used for intellectual property protection, be it game assets... or malicious code that tries to bypass antivirus engines.
The code responsible for the out of context ads is located in spoofed/illegitimate versions of legitimate SDKs, such as Unity and Android. For clarity, this investigation did not detect any fraud directly tied to such legitimate SDKs. All of the apps discovered seem to possess fairly low detection ratings across AV engines, largely because of the packer being used. App IDs can be found in the Appendix.
App Analysis Deep Dive
Most of the RAINBOWMIX apps have a “C-shaped rating distribution curve” (with primarily 1- and 5-star reviews), which is common with suspect apps.
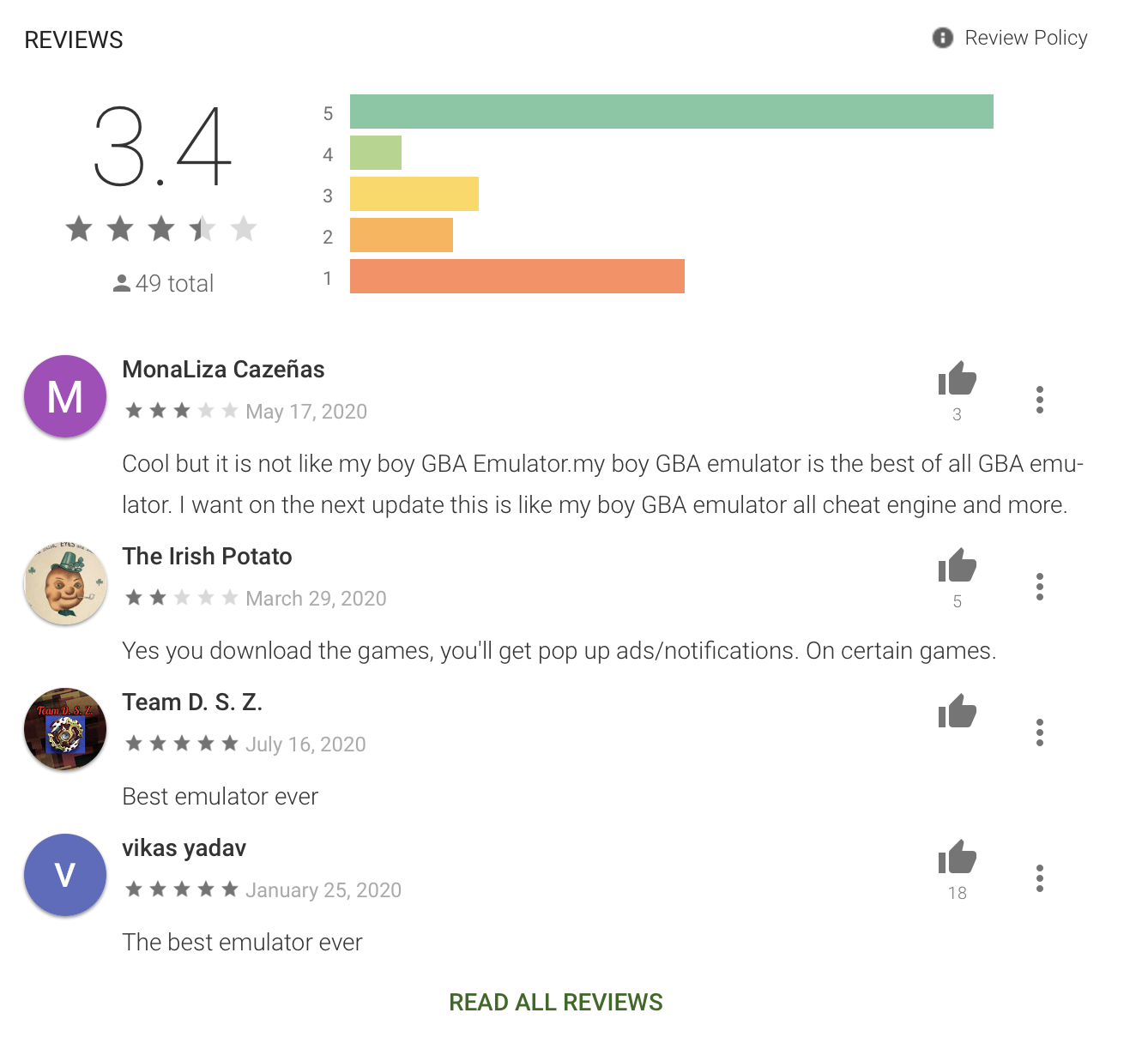
(click on any image in this post to enlarge)
C-shaped rating distribution for the APK GBA Emulator app.
Source: White Ops Threat Intelligence
The comments section for one app in particular (since removed)—APK GBA Emulator—demonstrated negative sentiment against their developer. The reviews suggested the app is barely functional, with many reports of out-of-context ads.
| App Name | APK GBA Emulator |
| Package Name | com.androidapk.gbaemulator |
| MD5 | 2c06380e078b7dd4ba7ca322ce2f968d |
| SHA256 | acf60700eee42d673025618bea8050b92c87058451933cb192a7d51de9755bce |
| File Size | 5.5 MB |
| Google Play Store Link | https://play.google.com/store/apps/details?id=com.androidapk.gbaemulator |
| Version Analyzed | 1.0.11 |
| Developer | kitaharaeasywire |
Details of the malicious app analyzed: APK GBA Emulator
Source: Google Play Store
All RAINBOWMIX apps are packed with various versions of the Tencent Legu packer. While some of the apps are detected as malicious on multi-scanning platforms, these detections are often vague and only relate to the use of the specific packer, and not their behavior when unpacked.
It is worth noting that even while packed, these apps exhibit some potentially suspicious behavior corresponding to the interstitial component of the ad SDKs, which are renamed with labels that point to well-known apps.
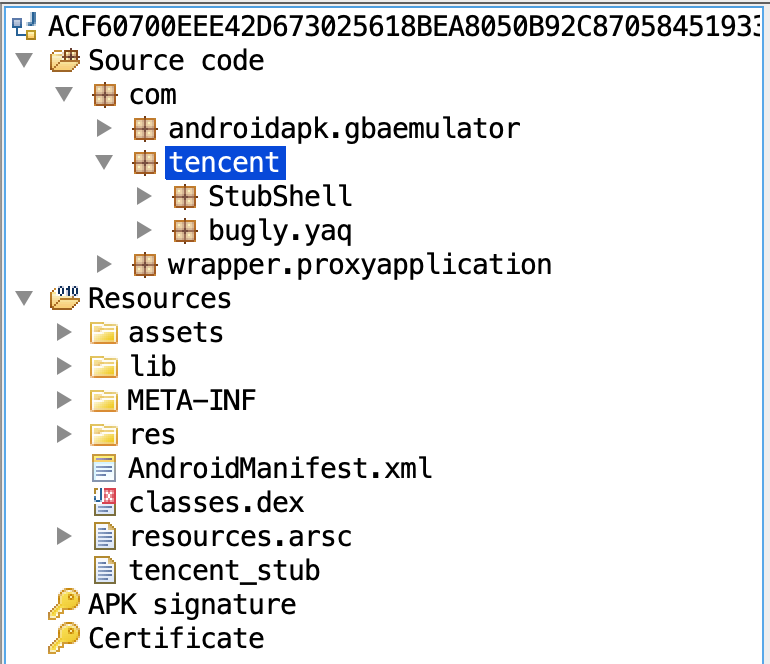
Packed contents of the APK GBA Emulator app
Source: White Ops Threat Intelligence
Inside the manifest, services and receivers respond to more triggers than they should, including:
- system boot
- connection changes
- charging cable plug in/outs
- app installations
Even though the code responsible for these services and receivers resides inside familiar packages, the code has nothing to do with these apps; the purpose was most likely to confuse analysts and trick static analysis engines which typically whitelist those namespaces. The main entry point for triggering out of context ads resides in the service com.timuz.a, which was present in all of the apps analyzed.
A suspicious amount of intents are processed inside one simple class. The receiver com.google.android.gms.common.license.a is a simple wrapper that tries to keep the service com.timuz.a running and sets up the out of context ad loop. It is contained in all bundles in the appendix.
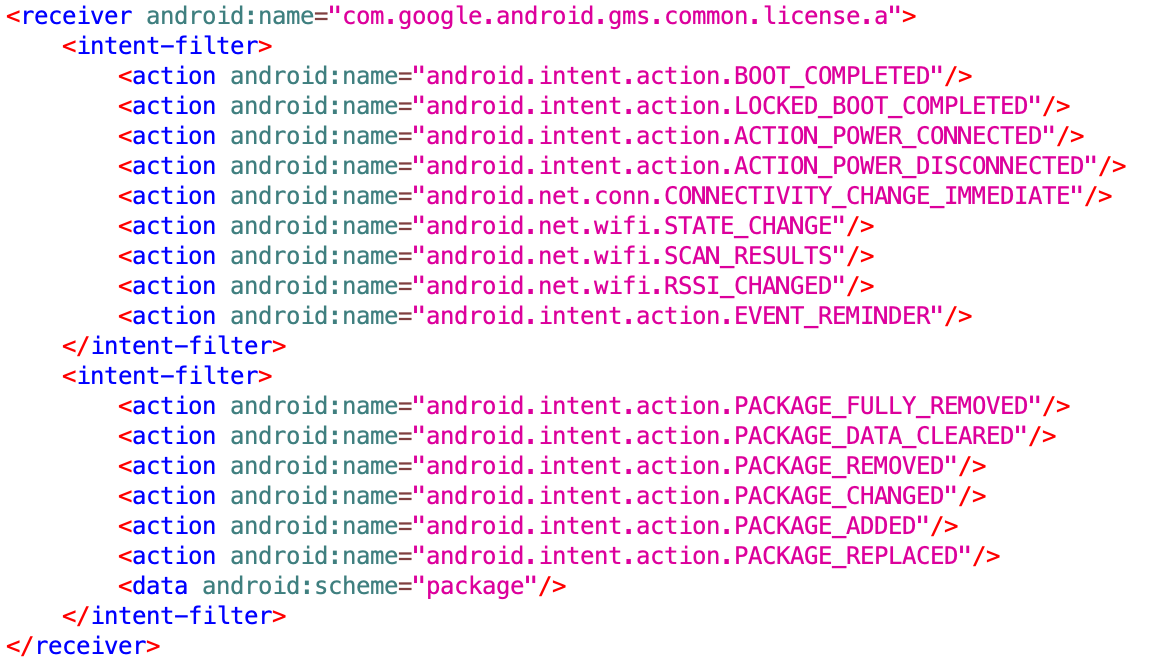
Suspicious receiver acting as persistence mechanism.
Source: White Ops Threat Intelligence
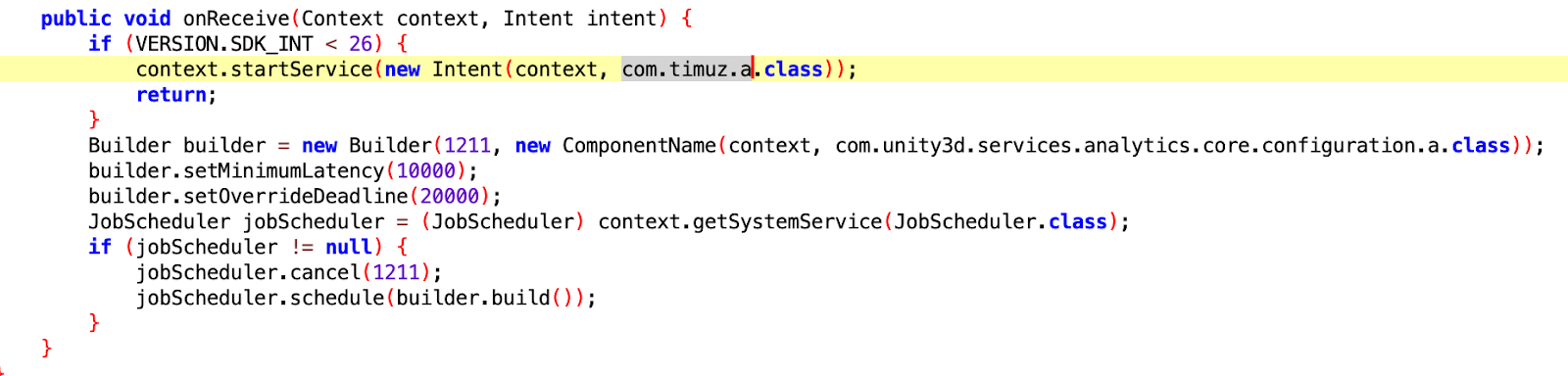
Service com.timuz.a being kept up by the persistence mechanism
Source: White Ops Threat Intelligence
The service com.timuz.a starts by getting the commands from the command-and-control (C2) (see dynamic analysis section) whose URL is hidden behind base64 encoding.
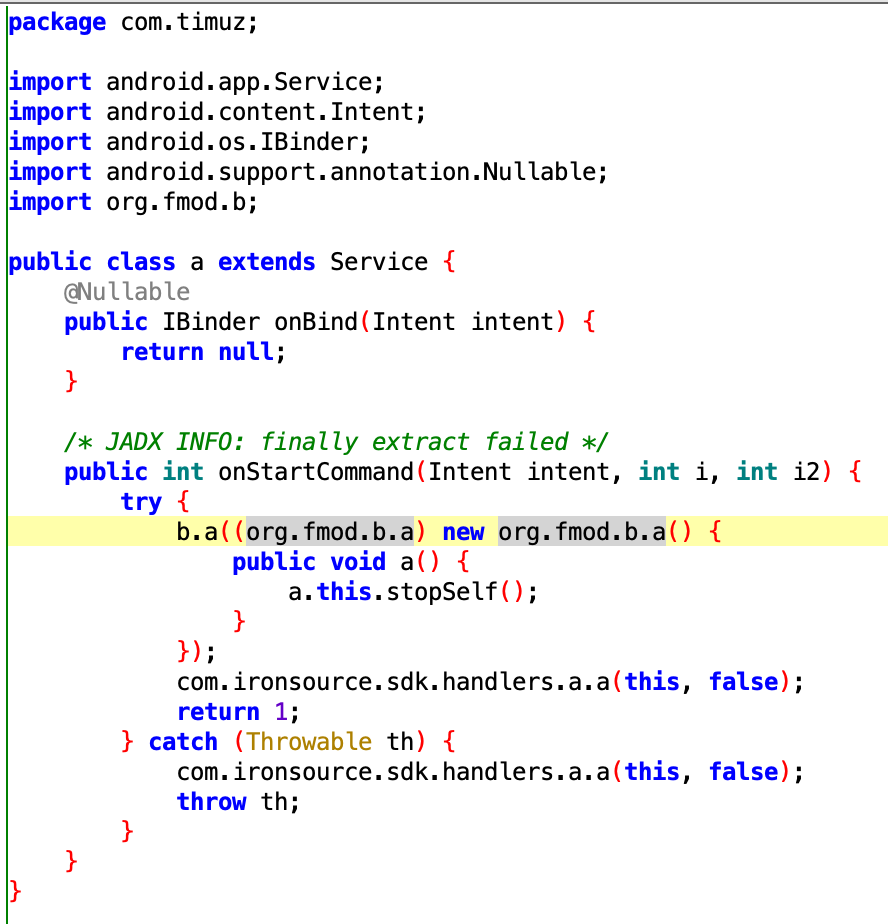
Code for C2 contact followed by an attempt of displaying an interstitial.
Source: White Ops Threat Intelligence
After the C2 responds, another service -- com.ironsource.sdk.handlers.a.a -- takes over and tries to display an out of context ad every 10 minutes. Its entrypoint is the same “god class” mentioned above that contained a plethora of broadcast receivers with android.support.coreui.a being the middleware responsible for doing the malicious interstitials. It is important to note that while com.ironsource.sdk.handlers.a.a is a legit SDK, ironSource is unlikely involved or aware of the abuse.
At this point, any semblance of finesse ends. The threat actors relied on the packer for most of the heavy (malicious) lifting, and any efforts to obfuscate their intent to do ad fraud disappear after the initial layer.
RAINBOWMIX tracked when users turned their screen on and off to better determine a good time to pop-up an ad, to help ensure that the ad impression counts, and also to ensure that an ad isn’t rendered when the screen is off. The code responsible for detecting screen on/off events was placed inside a fake Unity class com.unity.b.
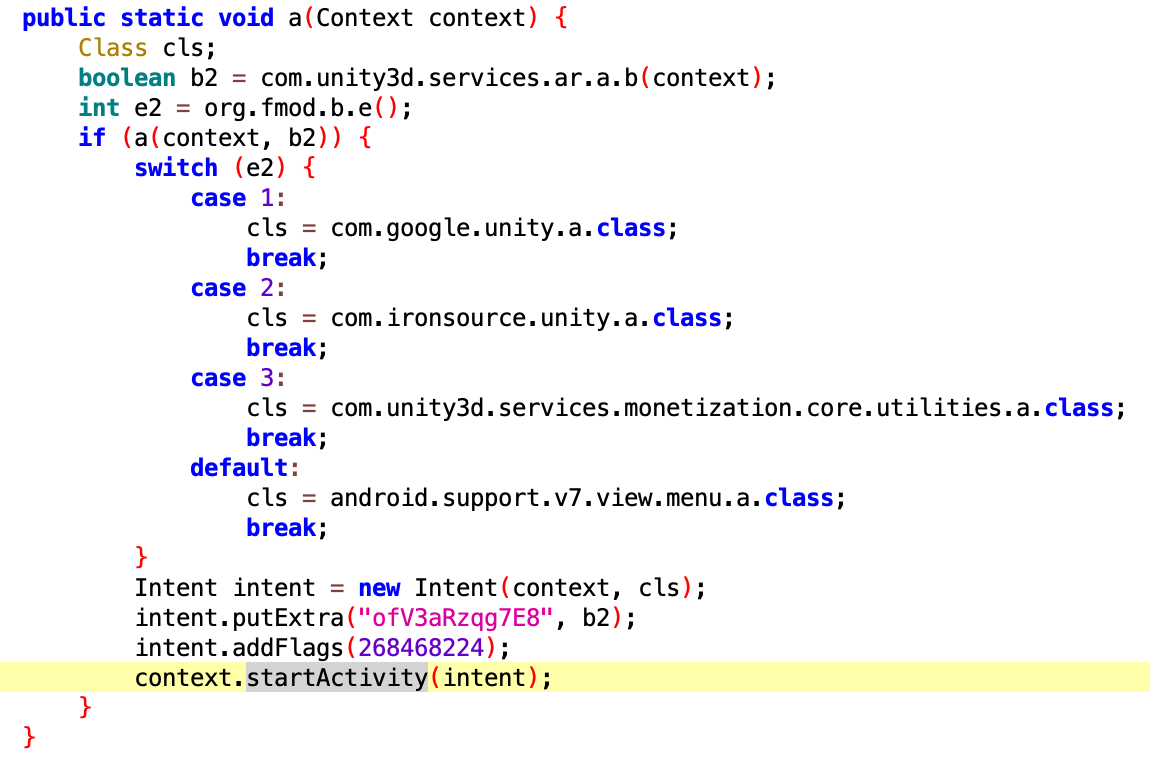
Ad activity being instantiated.
Source: White Ops Threat Intelligence
Domain and IP Information
The domain api[.]pythonexample[.]com (used as the C2 for the operation) was created in February 2017; however, this domain appears likely to be a hacked website, which was used by the threat actors to instruct the app to show the OOC interstitial ads. The domain was still active in July 2018 when a question was posed on an online forum:
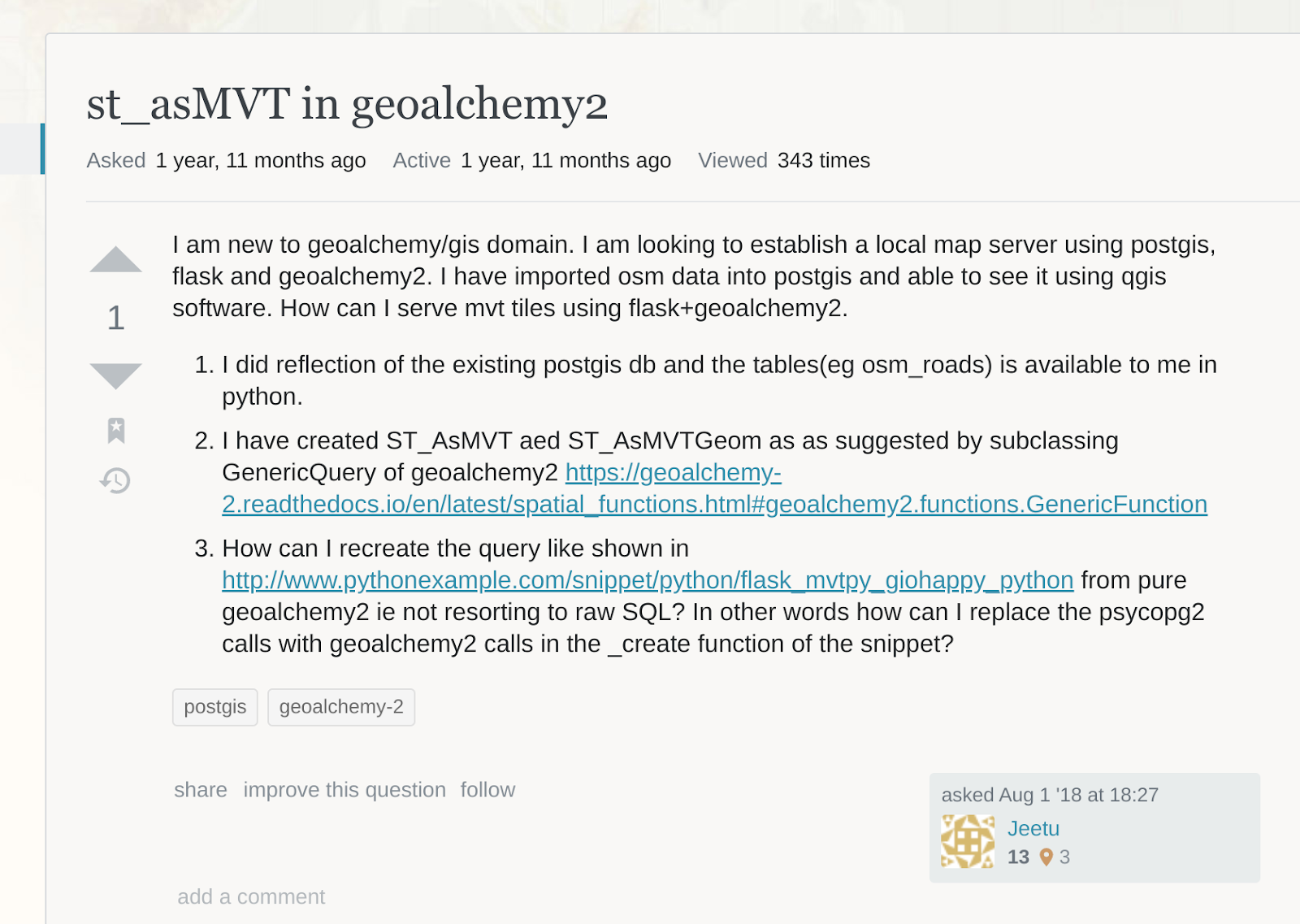
Question involving the C2 domain asked via Stack Overflow.
Source: Stack Overflow
This question is two years old, which makes it seem likely that the malware authors hacked it at some point after that. When visited during this research, the domain just presents the default Ngnix page. According to VirusTotal, the earliest upload referencing the C2 was in September 2019.
Earliest records of the operation in 2019.
Source: VirusTotal
| Domain | api[.]pythonexample[.]com |
| Registrar | NameSilo, LLC |
| Creation Date | 2017-02-27 |
| Expiration Date | 2021-02-27 |
| IP Address |
104.27.145 [.]111 |
| Country | USA |
Domain details for api[.]pythonexample[.]com, used as the OOC ad landing page.
Source: White Ops Threat Intelligence
Dynamic Analysis Findings
After installing the app, the following URL is contacted, and a JSON payload is downloaded.
hxxp://api[.]pythonexample[.]com/xyyx?pn=com.androidapk.gbaemulator
This is used as the C2 of the ad SDK, which determines which ad network to use as well as the interstitials frequency. The same C2 architecture is used across all of the RAINBOWMIX apps identified in this investigation.
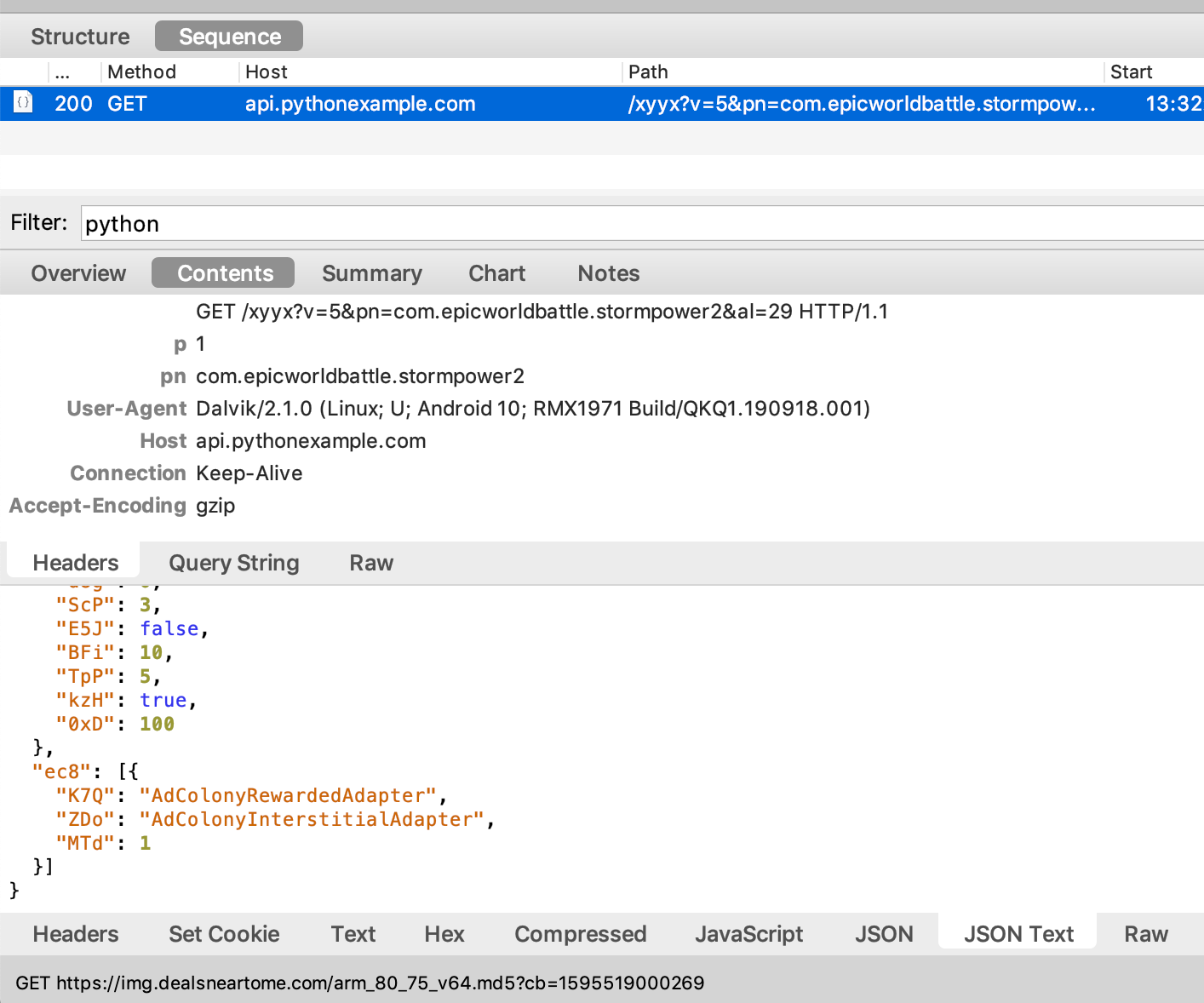
Figure 13: C2 message instructing the display of an AdColony interstitial.
Source: White Ops Threat Intelligence
Seconds after the C2 message, an AdColony interstitial appeared on the infected device’s screen, with an icon that implied to the user that the ad was being presented by a different app from what was actually showing it.
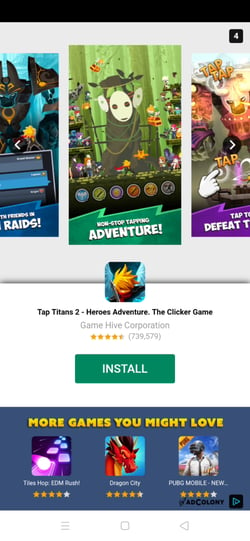 Out of context AdColony ad.
Out of context AdColony ad.
Source: White Ops Threat Intelligence

Out of context ad being rendered.
Source: White Ops Threat Intelligence
Data Analysis
The RAINBOWMIX apps have shown a considerable amount of volume over several months. There was volatility in traffic volume towards the end of April 2020 before steadily increasing heading into May. One clear and particular large spike in traffic occurred towards the middle-to-end of May, during which traffic volume approximately doubled before returning to previous levels. As of August 21, White Ops Satori team saw approximately 15 million ad impressions per day collectively from the RAINBOWMIX apps.
The graph below shows the overall RAINBOWMIX volume, as well as the volume from eight of the highest volume RAINBOWMIX apps in this time period. There is no rotation of apps evident during these months: each of the top apps has shown daily volume that roughly mimics that of the overall traffic volume over the entire period of time.
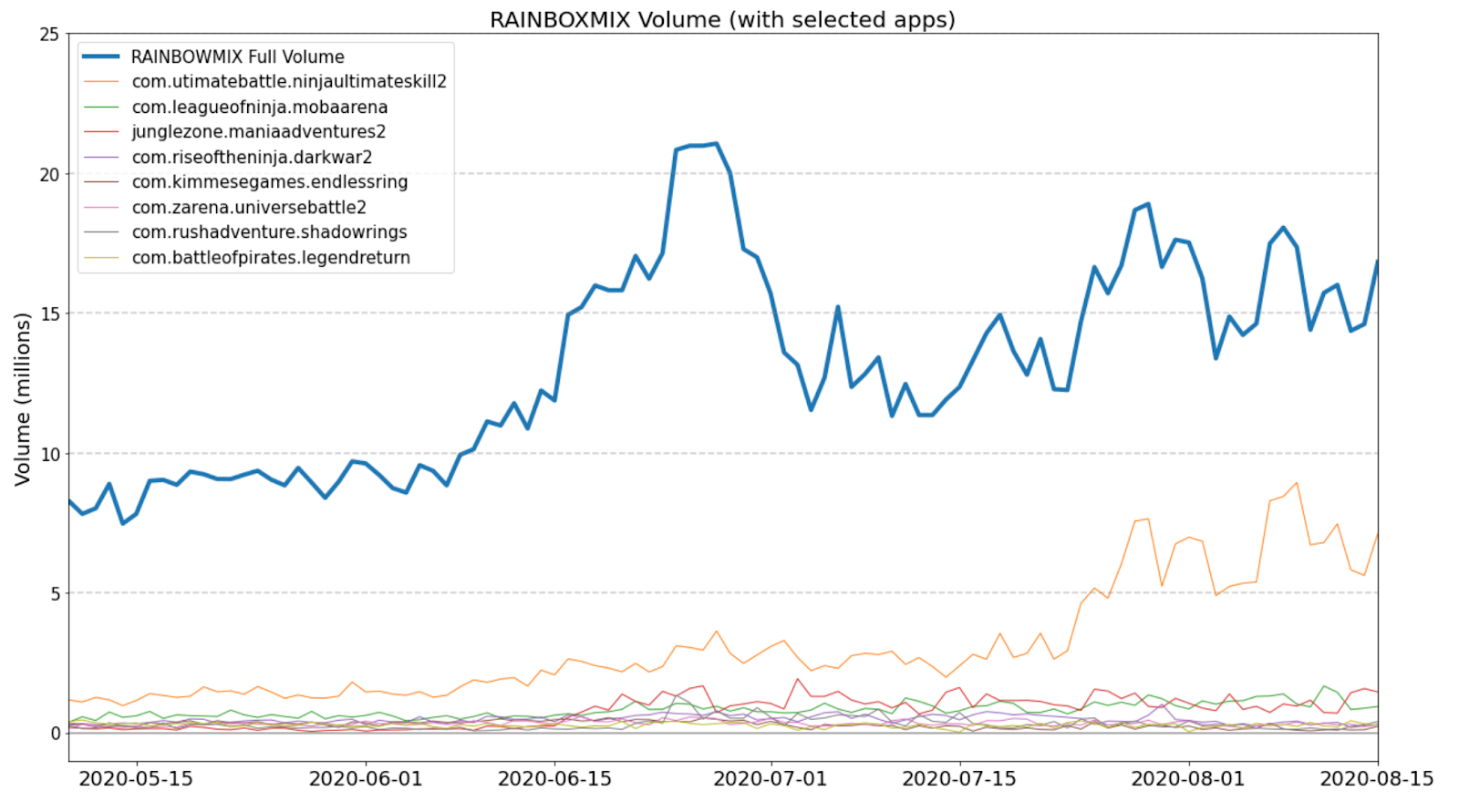
Volume of apps from May 1 - August 15, 2020.
Source: White Ops Threat Intelligence
Traffic Analysis
The ad impressions from RAINBOWMIX apps are not distinct from other, legitimate apps. This is not a big surprise: out-of-context ad impressions tend to look just like legitimate ad impressions because they are actual ad impressions on actual users’ devices. Perhaps the most remarkable aspect of this traffic is that it is so unremarkable.
The traffic comes primarily from the Americas and Asia. The top five countries include:
- 20.8% from Brazil
- 19.7% from Indonesia
- 11.0% from Vietnam
- 7.7% from the US
- 6.2% from Mexico
- 5.9% from the Philippines
Additionally, 53.3% of the traffic comes from Chrome Mobile 84, and 3.6% comes from Chrome Mobile 83. 4.9% of traffic is coming from Chrome Mobile 55, primarily from Indonesia.
66.0% of connections are cable/DSL, and 31.5% are cellular.
Distinctive APK Characteristic
White Ops rarely sees the service com.timuz.a in other apps in our pipeline and recommends using it as an indicator of RAINBOWMIX apps.
Appendix
Appendix: Apps Containing the Malicious SDK
Below is a list of the identified app package names containing the malicious SDK. This list is also available as a (txt) file or as a (pdf) file.
com.adventuregame.inforestisland
com.adventuresofchipmunks.rescuerangers
com.andersonic.play
com.androidapk.gbaemulator
com.asunaxwarrior.theflashswordlegend
com.asunaxwarrior.theflashswordlegend2
com.avengersleague.mobabattle
com.avengersleague.mobabattle2
com.badicecream.icepowers
com.badicecream.icepowers.bnn
com.badicecreamdeluxe.fruitattack
com.banjolab.ninetailstransformation
com.battleflag.senki.warofheroes
com.battleflag.senki.warofheroes2
com.battleofpirates.legendreturn
com.battleofsaiyan.universes
com.battleofsuper.warriorssuperblue
com.battleofz.sragonsmash
com.battleofz.sragonsmash2
com.battleofz.superwarriors
com.battletoads.dragonbro
com.battletoadsfighter.toadmania
com.bestclassic.supersmashflash
com.blackflag.piratesvsfairysuperbattle2
com.blazering.crazyworld
com.blazering.dashwarriors
com.bubblebobble.ghostmaze
com.buzzygames.worldtour
com.cactusteam.monstervshero
com.challenger.whitehatcowboy
com.championgame.supergodfist
com.chaosgames.kamebattle
com.circusclassic.lionjump
com.clashofdragon.stickheroes.ncr
com.classiccar.jackaljeep
com.classicnes.emulator.retrogames
com.cocolabs.magicstickwarriors
com.colorisland.bubblebobble
com.comicgames.animeninjaarena
com.comicgames.mangaworldbattlesaga
com.craftvalley.masterblockpe
com.dbzgames.resurrectionfrieza
com.dbziny.dragonkungfu
com.demonlabs.leagueofwarriors
com.denisnapoleon.felixpille.dbzauraofagod
com.denisnapoleon.felixpille.dbzauraofagod2
com.doubleheroes.dragon
com.dragonbattle.doublerevenge
com.dragonbrothers.jungleattack
com.dragonbrothers.waterfall
com.dragongames.battleofssjj
com.dragonstudio.kamestickheroes
com.dwagames.superzwarriors
com.earthbound.thegiftmanchronicles
com.epicnine.hakibattle
com.epicwildgames.demontail
com.epicworldbattle.stormpower
com.epicworldbattle.stormpower2
com.fanmades.comicninjabattle
com.farewellgames.ninjamagicwar
com.farewellgames.ninjamagicwar2
com.farmergame.saiyankoarena
com.fieldsofjustice.championsbattle
com.fighter.godofuniversecrusader
com.fireandicecouple.theicetemple
com.fireflygames.fireherolightpuzzle2
com.fireicecouple.thelighttemple
com.footballcaptain.worldtournament
com.frontierknight.evildrrobo
com.game64street.classicfighting
com.gamez64.nin64emulator
com.gammastudio.uchihabattle
com.gbcdeluxe.emulatorforandroid
com.greatdbzgames.dragonofdiamond
com.gunsmoke.legendshooting
com.hokage.unlimitedheroes
com.hopkins.borutofights
com.hotboyandicegirl.templeinforest
com.hotboyandicegirl.templeinforest2
com.hotboyandicegirl.templeinforest3
com.jackalshooting.supersoliders
com.johnslabs.superwarriorsmoba
com.jojovsninja.battle
com.jumpsuperstars.ultimatebattle
com.karolinagames.powerfighters
com.karolinagames.powerfighters2
com.kidicarus.angelland
com.kimmesegames.endlessring
com.kingdomguardian.rushwars
com.kingdomofbowmans.magicarrow
com.kingofsaiyan.dragonarena
com.kingofuniversefighters.ultrainstinct
com.kissonthebeach.lovelygirl
com.knucklesadvance.megamix
com.kog.zenexhibitionmarch
com.leagueofjustice.animewarriors
com.leagueofjustice.animewarriors2
com.leagueofjustice.animewarriorsreturn
com.leagueofninja.mobaarena
com.leagueofninja.mobabattle
com.leagueofninja.mobabattle2
com.legendarywarrior.powerofbroly
com.legendofmana.secret
com.legendstudio.bardockwarrior
com.leoneboy.zroyalaction
com.liongames.supermonkeykong
com.littlestardev.powerchampionship
com.lovelygames.swimmingpoolkissing
com.lufiagame.riseofthesinistrals
com.mangawar.battleofchaos
com.mazeescapeunblocked.kunmonkey
com.megagens.mdemulator
com.metalgear.superwarriors
com.mgba.romsemulators
com.minigames.icecreammazepuzzle
com.monfirered.gbaemulator
com.mortalfighting.arcadepro
com.msluggames.supervehicle
com.myboypro.gbcemulatorpro
com.namekgame.dragons
com.narugames.ninjafarewell
com.nauticalking.burningwill
com.nauticalking.burningwill2
com.ndsemuclassic.emulator
com.ndsemuclassic.emulatorv2
com.ndsplayer.ndsemuforandroid
com.neopop.neogeo.poco
com.nesfcbro.nesemulator
com.nicbros.thesecretrings
com.nido64.n64retrogames.emulator
com.ninjaarena.legendfighting2
com.ninjabattle.shinobilegend
com.ninjabon.battleofninja
com.ninjagames.legendroad
com.ninjamoba.finalbattle
com.ninjarampage.legendarypower
com.ninjarevenge.bladevssoul2
com.ninjasurvival.deathmatch
com.nswon.legendaryshinobiwar
com.pandagames.skilldashpower
com.panicmaze.mushroomkingdom
com.persianwarrior.recuseprincessjasmine
com.PiSNES.SNESforAPK
com.pocketlabs.emeraldmonsters
com.pokeblack.ndsemulator
com.pokediamond.ndsemulator
com.pokeemerald.gbaemulator
com.pokegba.pokegamess
com.pokerubygames.gbaemulator
com.pokestadium.n64emulator
com.powerzfighters.superkakarot
com.puzzgmamesstudio.icecaveattack
com.puzzlegames.bombmaze
com.pwlegend.fiercefightingarcade
com.rabbitgames.ringchampion
com.racingbattle.zdragonjumpracing
com.redfirepoke.gbaemulator
com.rikigames.shenronblast
com.rikigames.shenronblast2
com.ringmania.lostworld
com.riseoftheninja.darkwar
com.riseoftheninja.darkwar2
com.roadfighterclassic
com.ronandgames.superzwarriors
com.roulettegame.soccerrandomteamgen
com.royalflush.princesssidestory
com.rubypoke.kingofmonsters
com.rushadventure.shadowrings
com.saiyanchampions.thelegacyofsaiyan
com.saiyanclassic.fightinggames
com.saiyanfight.vsninjapirate
com.saiyanfighters.kingofavengers
com.saiyanrevenge.zlegendaryz
com.saiyanvsninja.arena
com.sbo.awakeningofsaiyan
com.senamo.ultimateninjawar
com.sgs.superbluefullpower
com.shadowdash.returnofknu
com.shadowrun.adventuresofdashheroes
com.shinigami.realmdeathfight
com.shinigami.realmdeathfight2
com.shinigami.tournamentofshinobi
com.simulators.blockartwarcraft.survival
com.smashbros.fightingarena
com.smashbros.shadowrun
com.smcgames.snesplayer
com.soldierforce.snowfield
com.somari2019.theadventurer
com.starsfighting.greatwarofheroes
com.stealthnaruassassins.tournament
com.stickgames.batlestarsv5
com.stickhero.xiaoreturn
com.stickninjafight.legendary
com.streethopper.basketchallenge
com.superclassic.dashwarriors
com.supercomicgames.starsfighting
com.superdinosaurs.frogsoldier
com.superdug.diggerinmaze
com.superfireboy.theforestdungeon
com.superfireboy.thelightdungeon
com.SuperGG.FightingWorld.HerofromUniverse
com.supermjbuu.besttransformations
com.superrockheroes.battlenetwork
com.supersmash.n64emulator
com.superspeed.heroes2019
com.superturtleswarriors.ninjaproject
com.superturtleswarriors.secretproject
com.superzfighter.tournament
com.sweetygames.animeavenger
com.sweetykiss.bedroomkissing
com.sweetykiss.bedroomkissing2
com.swimmingpoolkissing.princess
com.themagicalquest.mouse
com.thewildwestriders.bountyhunters
com.thronedefender.riseofarcher
com.tinygame.circusclassic
com.tournamentgames.zenoexpochampion
com.UltimateArena.championZZZ
com.ultimatefighting.masterofskill
com.ultimatefighting.masterofskill2
com.ultimateflash.ringexe
com.ultimateninja.animechampions
com.ultimateninja.fightingheroes
com.ultrafighting.anime.champions
com.ultrafighting.anime.champions2
com.ultrafighting.animechampions
com.ultrajackman.animebattle
com.unity.gamestapzfusionsaga2
com.utimatebattle.ninjaultimateskill2
com.warriorsgame.RiseofBroly
com.whitehat.spyhunter
com.woodman.fireredmonsters
com.xwarriors.giantrings
com.zarcade.zflashdimension
com.zarena.universebattle2
com.zbattlegame.superwarriors
com.zcrusherpower.pwg
com.zeldagames.n64emulator
com.zenogames.dragonzevolution
com.zhyperdimension.infinitebattle
com.zulugames.kaiwarriors
com.zuniversewarriors.kochampion
com.zwarriors.legendreturn
junglezone.maniaadventures2




